Cicada3301: A New Ransomware-as-a-Service Operation

A new ransomware-as-a-service (RaaS) operation named Cicada3301 has quickly emerged, already listing 19 victims on its extortion portal. This cybercrime operation has no connection to the legitimate Cicada 3301 cryptographic puzzle game from 2012-2014, despite using the same logo for promotion on cybercrime forums.
Launch and Early Attacks
Cicada3301 began promoting its operation and recruiting affiliates on June 29, 2024, via the RAMP ransomware and cybercrime forum. However, evidence from BleepingComputer shows that Cicada attacks started as early as June 6, indicating that the gang was initially operating independently before seeking affiliates.
 Cicada3301 ransomware operator seeking affiliates on RAMP forums
Cicada3301 ransomware operator seeking affiliates on RAMP forums
Source: Truesec
Double-Extortion Tactics
Like other ransomware operations, Cicada3301 uses double-extortion tactics. This involves breaching corporate networks, stealing data, and encrypting devices. The encryption key and threats to leak stolen data are used to pressure victims into paying a ransom. The gang operates a data leak site as part of this scheme.
 Cicada3301 extortion portal
Cicada3301 extortion portal
Source: BleepingComputer
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Malware Analysis and Similarities with ALPHV/BlackCat
An analysis by Truesec revealed significant overlaps between Cicada3301 and ALPHV/BlackCat, suggesting a possible rebrand or a fork created by former ALPHV core team members. Key similarities include:
- Both are written in Rust.
- Both use the ChaCha20 algorithm for encryption.
- Both employ identical VM shutdown and snapshot-wiping commands.
- Both share the same user interface command parameters, file naming conventions, and ransom note decryption methods.
- Both use intermittent encryption on larger files.
ALPHV performed an exit scam in early March 2024, stealing $22 million from Change Healthcare and claiming a fake FBI takedown.
Initial Access via Brutus Botnet
Truesec’s investigation suggests that Cicada3301 may partner with or utilize the Brutus botnet for initial access to corporate networks. The Brutus botnet, associated with global VPN brute-forcing activities targeting Cisco, Fortinet, Palo Alto, and SonicWall appliances, first appeared two weeks after ALPHV shut down, aligning the timelines of both groups.
VMware ESXi Targeting
Cicada3301 operates both Windows and Linux/VMware ESXi encryptors. The VMWare ESXi Linux encryptor, analyzed by Truesec, uses a special key entered as a command line argument to launch the encryptor. This key decrypts a JSON blob containing the configuration for encrypting a device.
The main function, linux_enc, uses the ChaCha20 stream cipher for file encryption, with the symmetric key encrypted using an RSA key. The encryption keys are generated randomly using the ‘OsRng’ function.
Trending: 10 Misconceptions about Hacking
Trending: OSINT Tool: cloud_enum
Specific File Targeting and Encryption Methods
Cicada3301 targets specific file extensions matching documents and media files, applying intermittent encryption for files larger than 100MB and encrypting entire contents for smaller files. The encryptor appends a random seven-character extension to the file name and creates ransom notes named ‘RECOVER-[extension]-DATA.txt,’ similar to BlackCat/ALPHV encryptors.
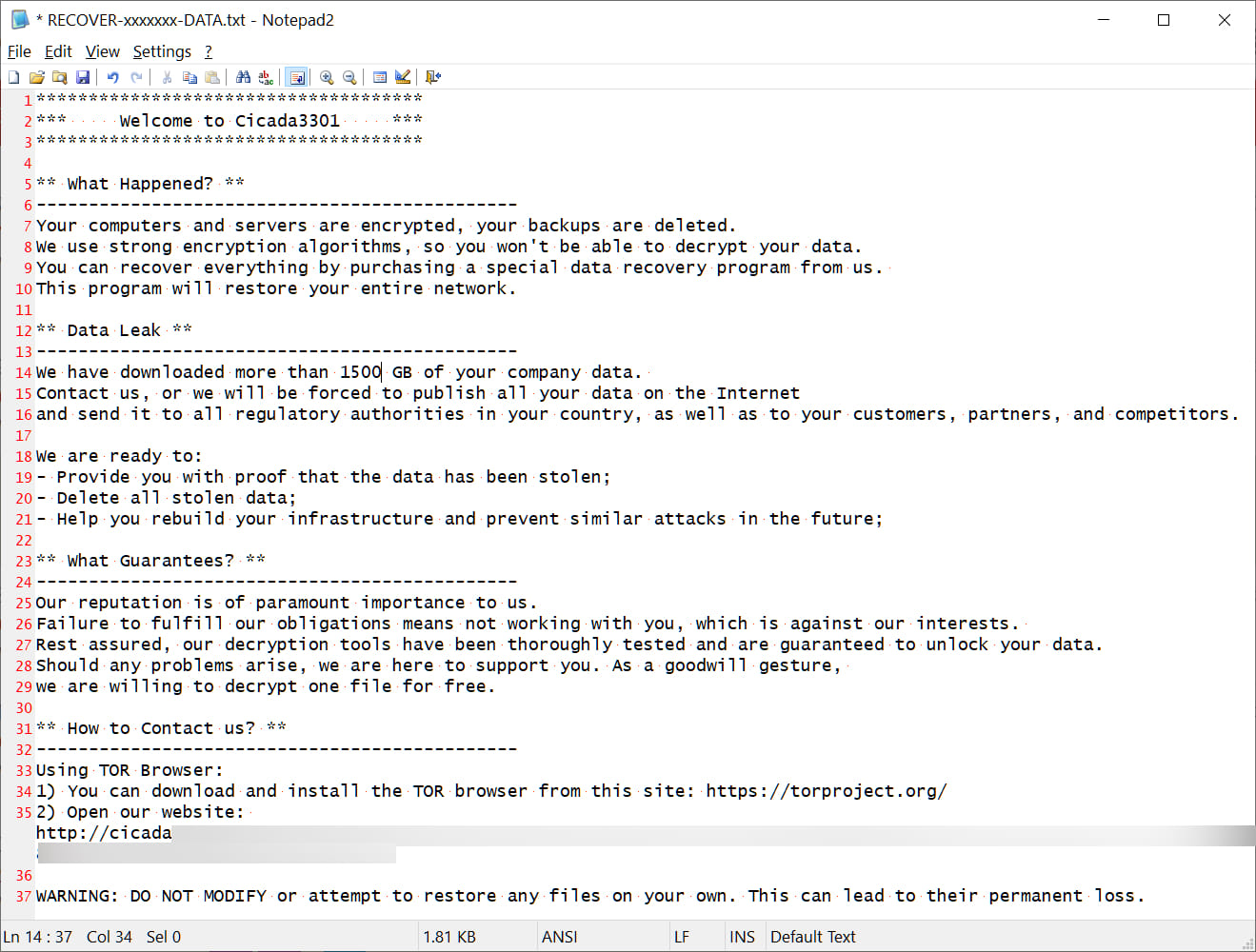 Cicada3301 ransom note
Cicada3301 ransom note
Source: BleepingComputer
Advanced Tactics
The ransomware includes parameters such as:
- sleep: Delays the encryptor’s execution to evade detection.
- no_vm_ss: Encrypts VMware ESXi virtual machines without shutting them down first.
By default, Cicada3301 uses ESXi’s esxcli and vim-cmd commands to shut down virtual machines and delete snapshots before encryption.
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













