Cisco Secure Client Software for Windows Vulnerable to Privilege Escalation Attack

A high-severity vulnerability has been discovered in Cisco Secure Client Software for Windows (formerly AnyConnect Secure Mobility Client), which could allow attackers to elevate privileges to the SYSTEM account. This software enables secure Virtual Private Network (VPN) connections for remote work and provides network administrators with endpoint management features and telemetry.
Tracked as CVE-2023-20178, the vulnerability allows authenticated threat actors to escalate privileges to the Windows operating system’s SYSTEM account through low-complexity attacks that do not require user interaction. Exploitation involves abusing a specific function of the Windows installer process.
Cisco has released security updates to address this flaw, stating that there is no evidence of active exploitation or public exploit code targeting the vulnerability at present. The fix is included in the latest versions of AnyConnect Secure Mobility Client for Windows (4.10MR7) and Cisco Secure Client for Windows (5.0MR2).
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
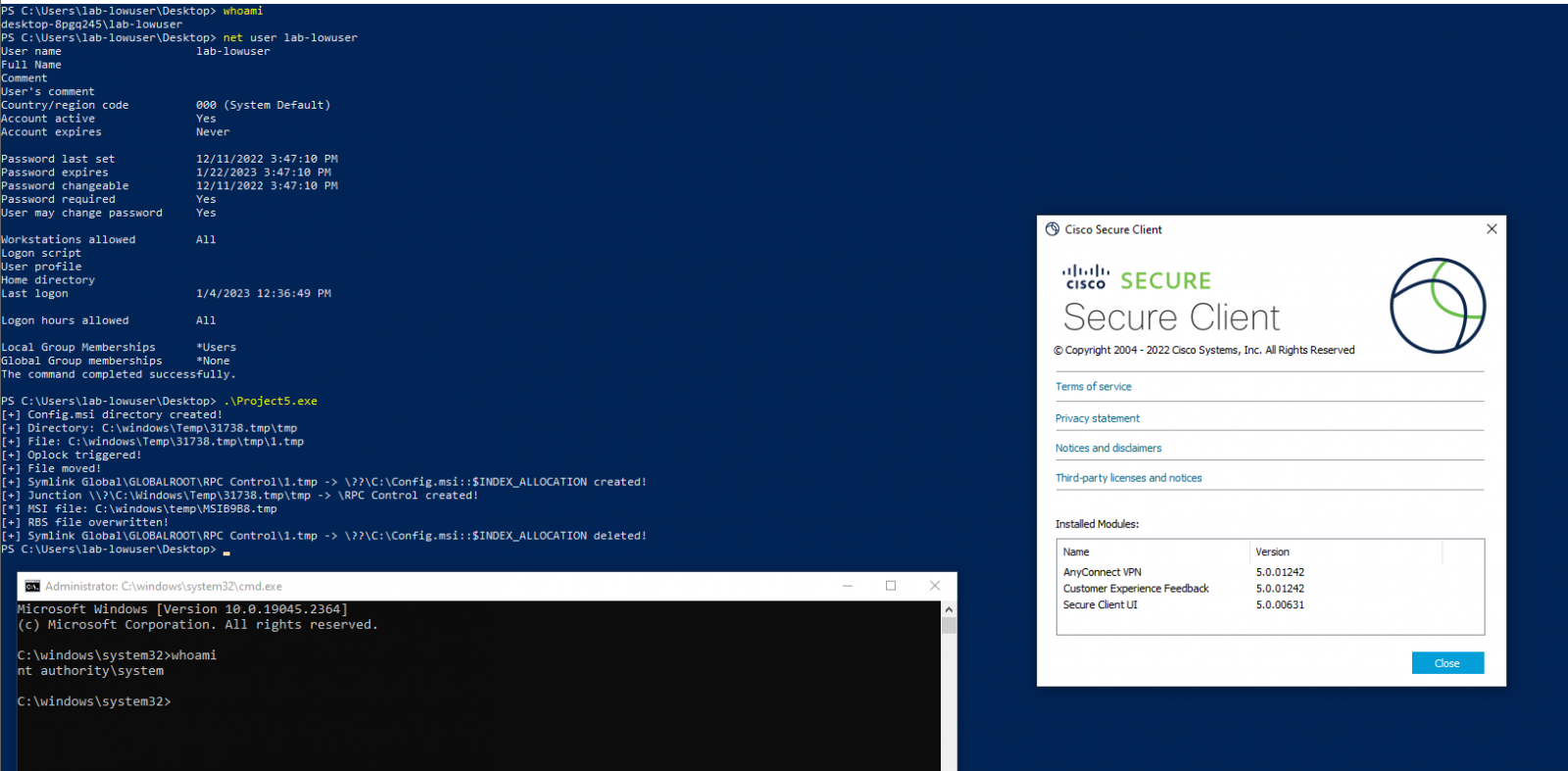
Recently, security researcher Filip Dragović discovered and reported the Arbitrary File Delete vulnerability to Cisco and published proof-of-concept (PoC) exploit code earlier this week. The PoC was tested against Cisco Secure Client (version 5.0.01242) and Cisco AnyConnect (version 4.10.06079).
The vulnerability arises when the vpndownloader.exe process is initiated in the background upon connecting to the VPN. It creates a directory in “c:\windows\temp” with default permissions in a specific format. The researcher explains that by exploiting this behavior, an attacker can delete arbitrary files as the NT Authority\SYSTEM account.
Trending: Offensive Security Tool: PhoneSploit Pro
The attacker can then escalate privileges by spawning a SYSTEM shell through arbitrary file deletion, leveraging the Windows installer behavior and the execution of a client update process after a successful VPN connection.
This incident serves as a reminder of the importance of promptly patching software vulnerabilities. In the past, Cisco has addressed other security flaws in AnyConnect, some of which were actively exploited in attacks. Users are advised to keep their software up to date to mitigate potential risks.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com












