ClearFake Campaign Targets macOS with Atomic Stealer Malware
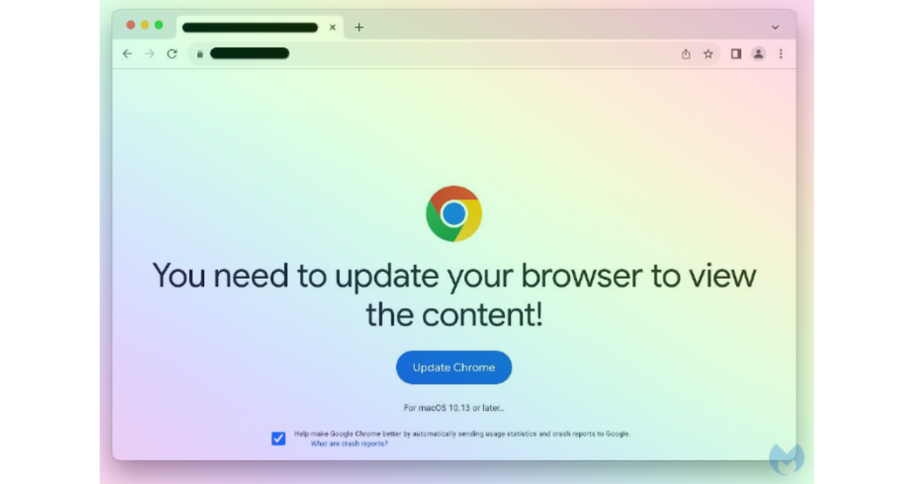
The ClearFake campaign is now delivering the powerful Atomic Stealer (AMOS) macOS information stealer through deceptive browser update prompts. Security researchers at Malwarebytes have flagged this as a significant threat, emphasizing the continuous enhancements made to the Atomic Stealer by its authors.
Designed to specifically target macOS, the Atomic Stealer goes beyond traditional information theft, extracting sensitive data such as Keychain passwords, system details, desktop files, and macOS credentials. Its reach extends to multiple browsers, compromising auto-fills, passwords, cookies, wallets, and credit card information. Notably, popular cryptowallets like Electrum, Binance, Exodus, Atomic, and Coinomi are also at risk.

SALE: Benefit from discounted prices on our Courses from 24/11 to 06/12.
Offensive Security, Bug Bounty Courses
The ClearFake campaign, initially discovered by Randy McEoin in August, utilizes compromised websites as a distribution channel for fake browser updates. Recent upgrades, including the use of smart contracts for redirect mechanisms, have made it a potent and widespread social engineering scheme. Alarmingly, the campaign has now set its sights on Mac users, distributing ClearFake along with the associated payload to deceive victims.

Security researcher Ankit Anubhav first observed this Mac-focused distribution on November 17. The attackers craftily mimic the official Apple Safari and Chrome pages on compromised sites. Unsuspecting victims, prompted to click the “update” button, receive a DMG file disguised as a Safari or Chrome update. Once opened, the file requests the admin password and immediately executes malicious commands.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: securityaffairs.com













