Clever Phishing Toolkit Emerges: Fake WinRAR and Windows File Explorer on ZIP Domains
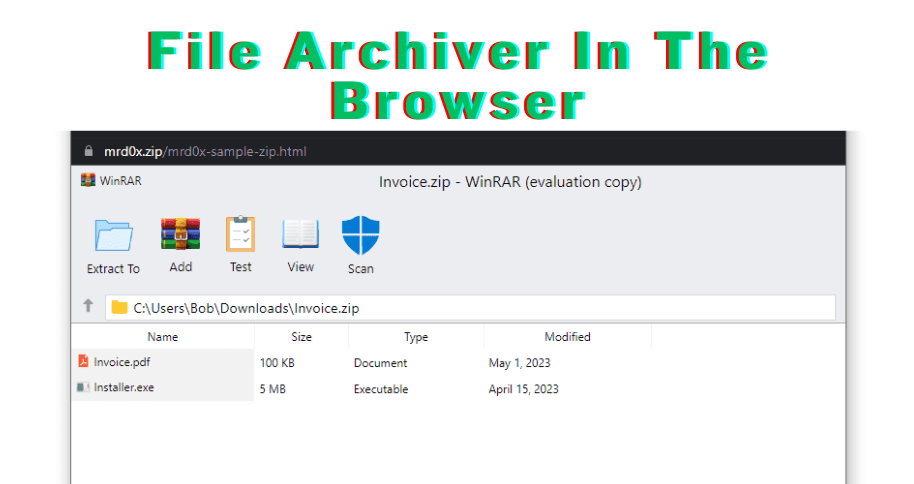
In a concerning development, a newly discovered phishing kit dubbed ‘File Archivers in the Browser’ has surfaced, taking advantage of ZIP domains to perpetrate fraudulent activities. This insidious toolkit leverages the display of counterfeit WinRAR and Windows File Explorer windows within the browser interface, cleverly deceiving unsuspecting users into launching malicious files.
Earlier this month, Google introduced the option to register ZIP top-level domain (TLD) addresses, enabling users to host websites or create email addresses using ZIP extensions. However, since their release, a heated debate has ensued regarding the potential cybersecurity risks associated with these domains.
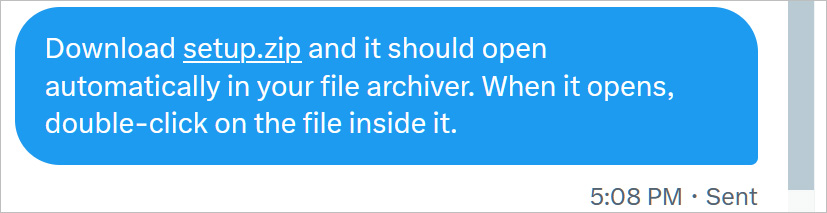 Twitter DM automatically turns setup.zip into a link – BleepingComputer
Twitter DM automatically turns setup.zip into a link – BleepingComputer
While some experts argue that concerns are exaggerated, the primary worry revolves around certain websites automatically converting strings ending with ‘.zip’ into clickable links. This functionality inadvertently opens the door to malware delivery and phishing attacks, as individuals may be deceived into clicking on seemingly harmless links.
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
A file archiver in the browser
Addressing these apprehensions, esteemed security researcher mr.d0x has unveiled an ingenious phishing toolkit that capitalizes on ZIP domains. This toolkit simulates the presence of authentic file archiver software, such as WinRAR, within the browser interface, fostering an appearance of legitimacy.
During a demonstration shared with BleepingComputer, the toolkit showcased its ability to embed a counterfeit WinRAR window directly in the browser when a .zip domain is accessed. Users are presented with a seemingly legitimate ZIP archive, complete with the illusion of browsing its contents. Notably, the toolkit’s effectiveness is heightened when deployed as a popup window, allowing for the removal of the address bar and scrollbar, resulting in a more convincing WinRAR window illusion.
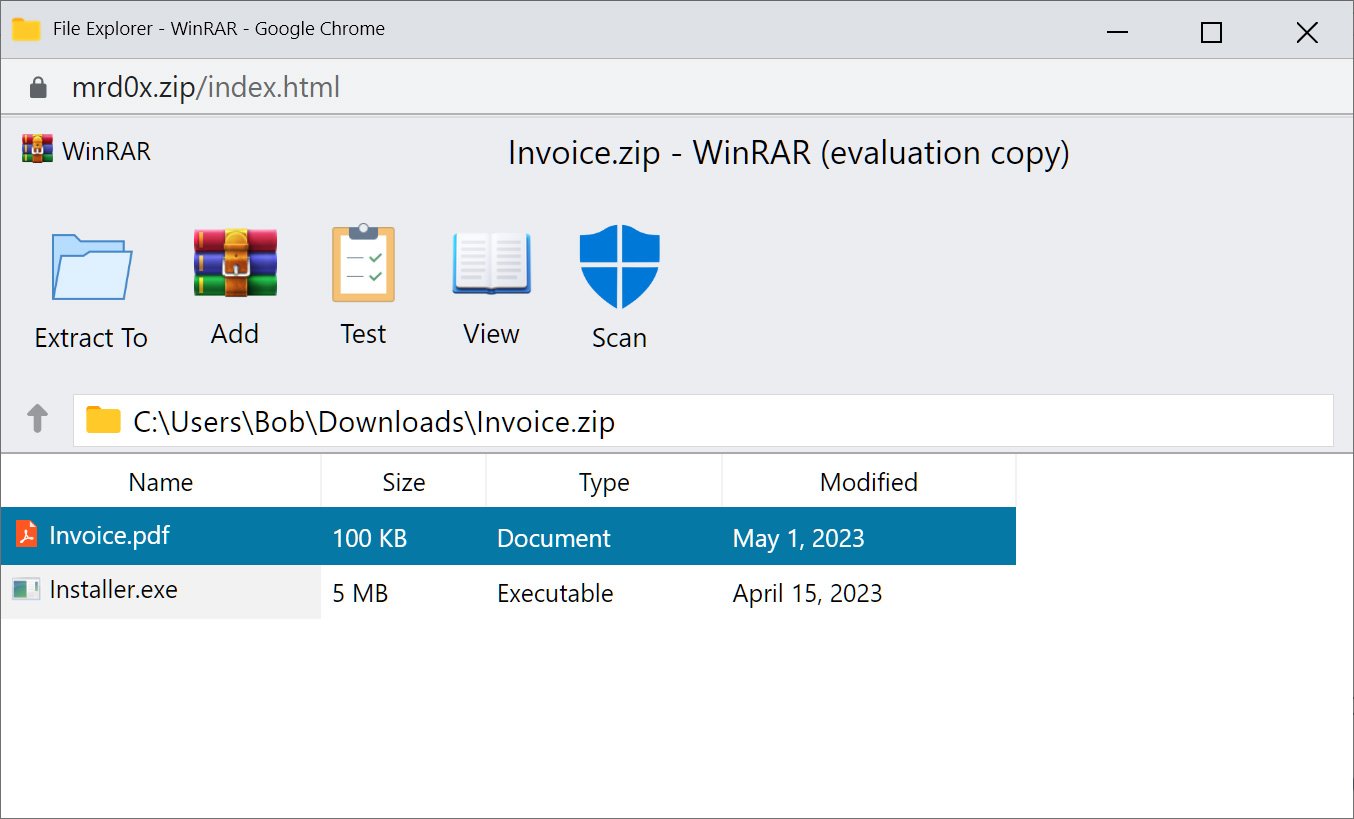 Fake in-browser WinRar screen pretending to open a ZIP archive
Fake in-browser WinRar screen pretending to open a ZIP archive
Source: BleepingComputer
To further enhance its credibility, the researchers behind the toolkit implemented a deceptive security scan button. Upon clicking, users are greeted with a reassuring message indicating that the scanned files are free from threats—a tactic aimed at instilling a false sense of security.
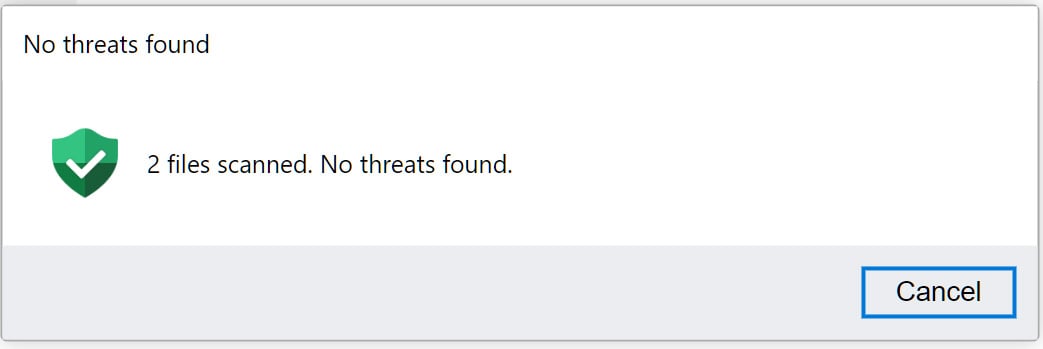 Fake file scanner
Fake file scanner
Source: BleepingComputer
Despite retaining the browser’s address bar, this sophisticated toolkit has the potential to deceive unsuspecting victims into believing they are interacting with a genuine WinRAR archive. Moreover, the possibility of employing creative CSS and HTML techniques could refine the toolkit’s effectiveness even further.
Additionally, mr.d0x has developed another variant of the phishing toolkit, featuring a counterfeit in-browser Windows File Explorer interface that pretends to open ZIP files. While still a work-in-progress with some missing elements, this variant adds another layer to the phishing kit’s deceptive capabilities.
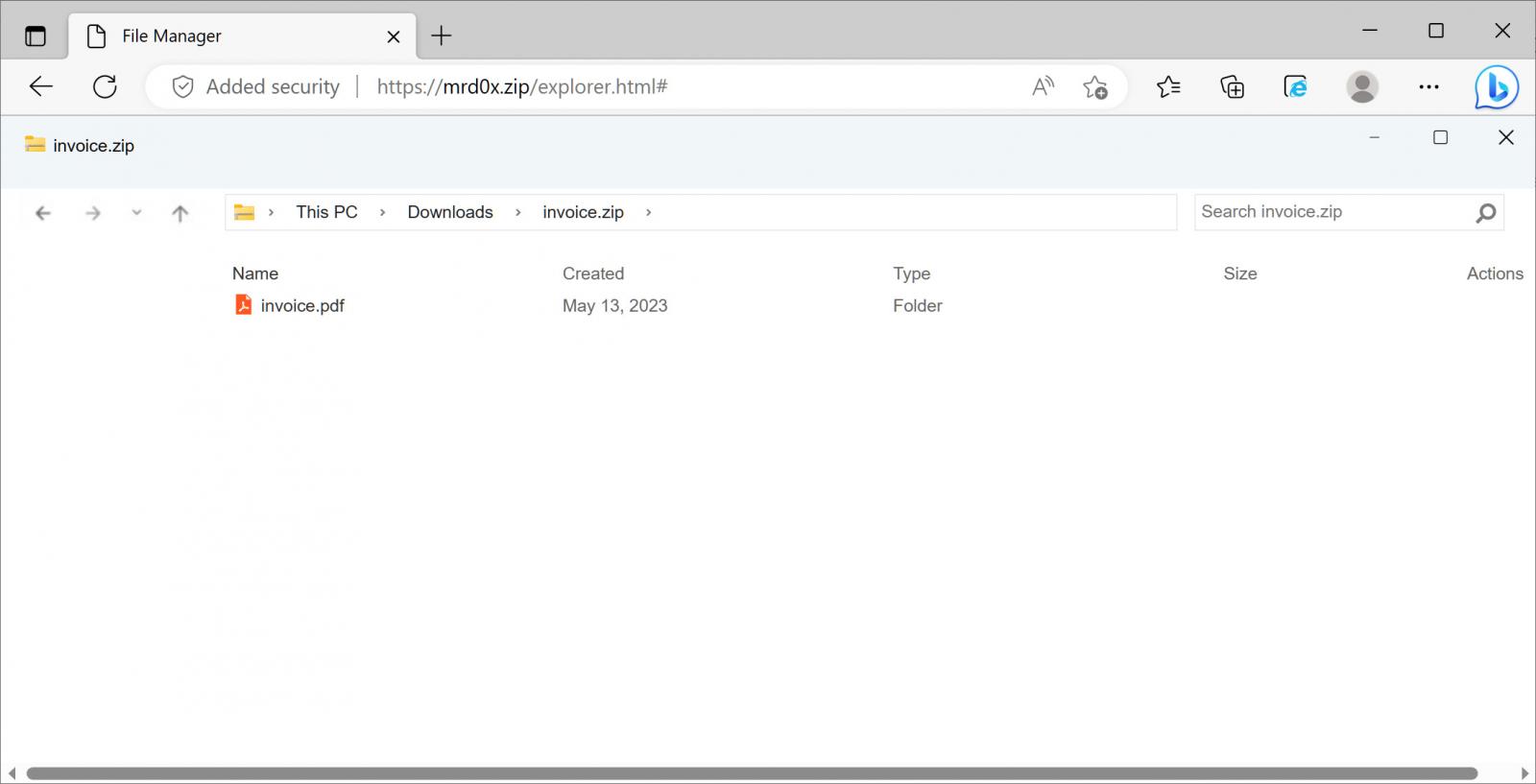 Fake Windows File Explorer shown in the browser
Fake Windows File Explorer shown in the browser
Source: BleepingComputer
Trending: Recon Tool: Sniffer
Phishing Toolkit
This phishing toolkit, as explained by mr.d0x, poses a dual threat, enabling both credential theft and malware delivery. For instance, within the fake WinRAR window, if a user double-clicks on a PDF file, they may unknowingly be redirected to a fraudulent page that solicits their login credentials under the guise of accessing the file.
Furthermore, the toolkit can be employed to deliver malware by presenting a PDF file for download, which, when clicked, initiates the download of an identically named .exe file. Given that Windows does not display file extensions by default, users may perceive it as a harmless PDF file, subsequently falling victim to executing the concealed executable.
Of particular concern is how Windows searches for files and, when unable to locate them locally, resorts to opening the searched string within a browser. If the string corresponds to a valid domain, the associated website will be launched; otherwise, Bing search results will be displayed. This mechanism inadvertently opens the door for potential abuse, as cybercriminals registering ZIP domains mirroring common file names can trick the operating system into opening malicious websites masquerading as genuine ZIP archives displayed by WinRAR.
This elaborate technique serves as a stark reminder of the vulnerability introduced by ZIP domains, which can be exploited for the creation of sophisticated phishing attacks, malware delivery, and credential theft. As a renowned figure in the field, mr.d0x has previously showcased his prowess in devising clever phishing toolkits, including the utilization of VNC for bypassing multi-factor authentication (MFA) and the Browser-in-the-Browser technique, which threat actors leveraged to pilfer Steam credentials.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com












