Cloudflare CDN Flaw Enables Zero-Click Geo-Location Attack via Signal, Discord

See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Why It’s a Zero-Click Attack
This method doesn’t require the target to interact with the malicious image or message. Applications like Signal and Discord automatically download images for push notifications, enabling the attacker to execute the attack without the target opening the message.
Accuracy and Precision
- The tracking precision depends on the density of Cloudflare data centers in the region.
- In urban areas with multiple nearby data centers, the accuracy improves significantly.
- In rural or less populated regions, the accuracy is broader, typically spanning a radius of 250–300 miles.
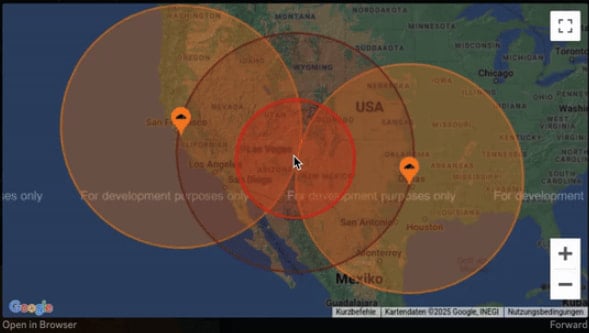 Locating the target
Locating the target
Source: hackermondev | GitHub
Experimenting with Discord’s CTO
While testing the attack, Daniel attempted to locate Discord’s CTO, Stanislav Vishnevskiy. He found that anycast routing (a load-balancing feature where multiple nearby data centers handle requests) slightly improved location accuracy around major cities.
Trending: Offensive Security Tool: ACEshark
Cloudflare’s Response
Daniel disclosed the vulnerability to Cloudflare, Signal, and Discord. Cloudflare resolved the issue in December 2024, patching the Workers bug and awarding the researcher a $200 bounty.
In a statement to BleepingComputer, a Cloudflare spokesperson said:
“This was first disclosed in December 2024 through our bug bounty program, investigated and immediately resolved… We continue to encourage third parties and researchers to report this type of activity for review by our team.”
Ongoing Feasibility
Despite the patch, Daniel found the attack still partially viable by using a VPN to simulate routing through different data centers. This approach covers approximately 54% of Cloudflare’s global data centers, although it is now more cumbersome to execute.
Signal and Discord Responses
- Signal: Dismissed the report as outside their mission’s scope to implement network-layer anonymity.
- Discord: Rejected the report, attributing the issue to Cloudflare.
Mitigation
To prevent similar attacks, Cloudflare users are advised to disable caching where necessary. Meanwhile, the incident underscores the risks posed by CDN-based caching in privacy-sensitive applications.
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com


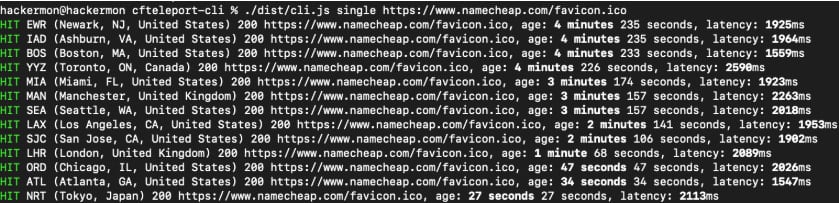 Calculating response times
Calculating response times










