Cloudflare DDoS Safeguards Ironically Exploited via Cloudflare

Of concern is the fact that this bypass can be executed with minimal prerequisites: the attackers simply need to create a free Cloudflare account, which becomes part of the attack process. However, it’s worth noting that attackers must possess knowledge of the targeted web server’s IP address to exploit these vulnerabilities effectively.
Certitude’s researcher Stefan Proksch discovered that the heart of the issue lies in Cloudflare’s approach of using shared infrastructure that accepts connections from all tenants, which has led to the discovery of two distinct vulnerabilities affecting Cloudflare’s “Authenticated Origin Pulls” and “Allowlist Cloudflare IP Addresses” features.
“Authenticated Origin Pulls” is a security feature provided by Cloudflare to ensure that all HTTP(s) requests directed to an origin server pass through Cloudflare rather than originating from potential attackers. When configured, customers can upload their SSL/TLS certificates via an API or generate one through Cloudflare, with the latter being the default and simpler method.
 Cloudflare origin certificate installation
Cloudflare origin certificate installation
Source: BleepingComputer
Offensive Security, Bug Bounty Courses
In this process, Cloudflare uses the SSL/TLS certificate for authenticating HTTP(S) requests between its reverse proxies and the customer’s origin server, effectively safeguarding the website against unauthorized access.
However, the vulnerabilities come into play as Cloudflare employs a shared certificate for all customers, instead of employing tenant-specific certificates. Consequently, all connections originating from Cloudflare are treated as legitimate, allowing attackers to circumvent this protection.
Attackers can exploit this vulnerability by establishing a custom domain with Cloudflare and directing the DNS A record to the victim’s IP address. Then, they can deactivate all protection features for this custom domain in their own tenant and route their attacks through Cloudflare’s infrastructure.
This approach enables attackers to evade protection measures, as they appear to be originating from Cloudflare itself.
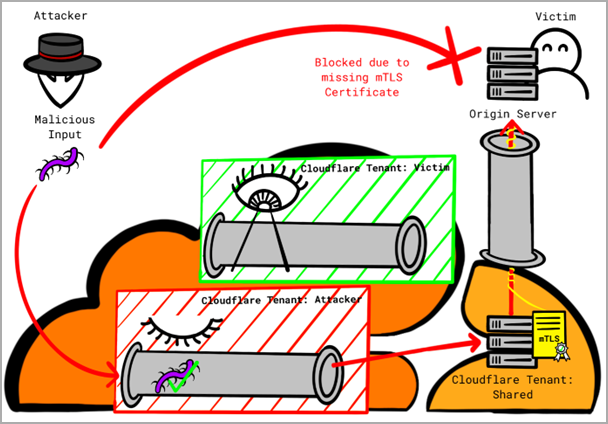 Exploiting shared Cloudflare certificates (Certitude)
Exploiting shared Cloudflare certificates (Certitude)
Mitigating this vulnerability necessitates the use of custom certificates rather than relying on certificates generated by Cloudflare.
The second vulnerability affects Cloudflare’s “Allowlist Cloudflare IP Addresses” feature, which permits only traffic originating from Cloudflare’s IP address range to access clients’ origin servers. Here, attackers can once again exploit a logic flaw by setting up a domain with Cloudflare, pointing the domain’s DNS A record to the target victim’s server’s IP address, disabling all protection features for the custom domain, and redirecting malicious traffic through Cloudflare’s infrastructure.
This traffic is perceived as trusted from the victim’s perspective, thereby bypassing security controls.
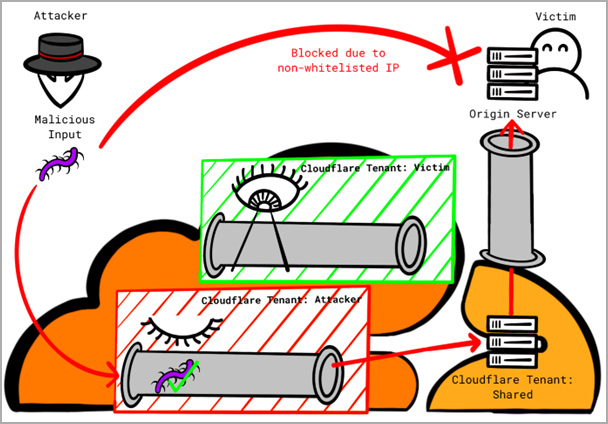 Exploiting Allowlist Cloudflare IP (Certitude)
Exploiting Allowlist Cloudflare IP (Certitude)
Proof-of-concept demonstrations have been shared to illustrate how these vulnerabilities can be leveraged to bypass Cloudflare’s protections.
In light of these findings, Certitude recommends the following defense measures:
- Utilize custom certificates when configuring the “Authenticated Origin Pulls” feature, rather than relying on Cloudflare’s shared certificate.
- Employ Cloudflare Aegis (if available) to define a more specific egress IP address range dedicated to each client.
The researchers who discovered these logic flaws, Florian Schweitzer and Stefan Proksch, reported them to Cloudflare via HackerOne on March 16, 2023. However, the issue was categorized as “informative,” prompting concerns about the need for additional protection mechanisms or notifications to clients with potentially vulnerable configurations. Cloudflare has not yet responded to inquiries on these matters.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]












