Conti ransomware’s internal chats leaked after siding with Russia


Reading Time: 2 Minutes
A Ukrainian security researcher has leaked over 60,000 internal messages belonging to the Conti ransomware operation after the gang sided with Russia over the invasion of Ukraine.
BleepingComputer has independently confirmed the validity of these messages from internal conversations previously shared with BleepingComputer regarding Conti’s attack on Shutterfly.
AdvIntel CEO Vitali Kremez, who has been tracking the Conti/TrickBot operation over the last couple of years, also confirmed to BleepingComputer that the leaked messages are valid and were taken from a log server for the Jabber communication system used by the ransomware gang.
Kremez told BleepingComputer that the data was leaked by a researcher who had access to the “ejabberd database” backend for Conti’s XMPP chat server. This was also confirmed by cybersecurity firm Hold Security.
In total, there are 393 leaked JSON files containing a total of 60,694 messages since January 21, 2021, through today. Conti launched their operation in July 2020, so while it contains a big chunk of their internal conversations, it is not all of them.
These conversations contain various information about the gang’s activities, including previously unreported victims, private data leak URLs, bitcoin addresses, and discussions about their operations.
For example, the conversation below is the Conti members wondering how BleepingComputer learned of their attack on Shutterfly in December.
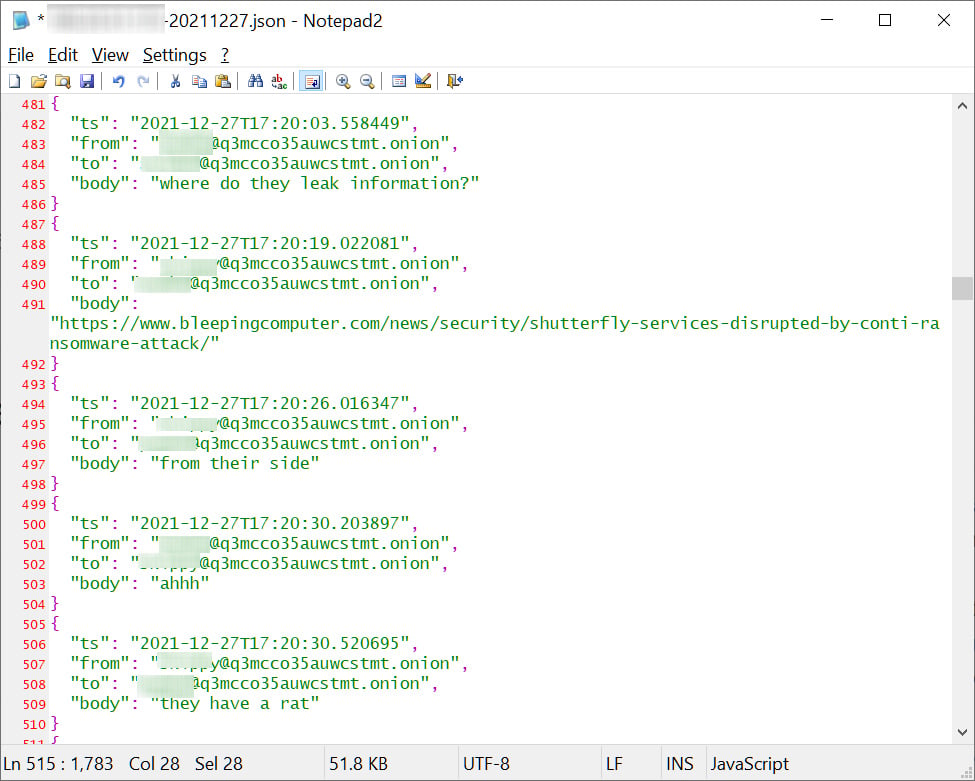
Translated by Google Translate
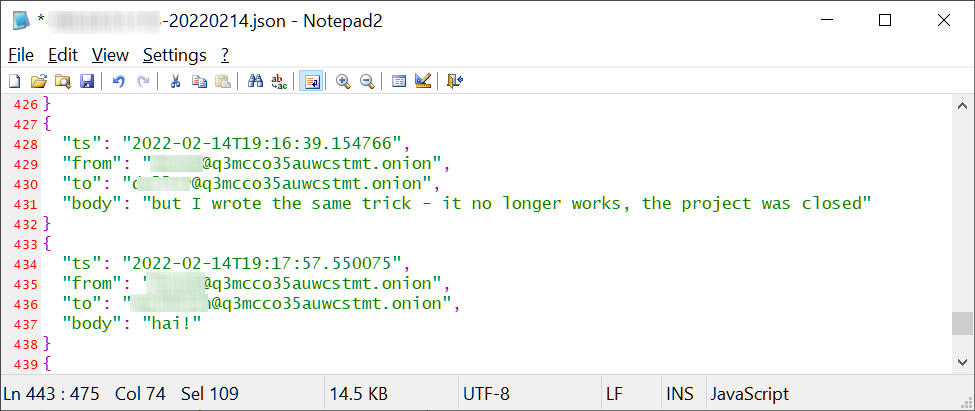
Kremez also shared a snippet of conversation that he found discussing how the TrickBot operation was shut down, as we reported last week.
There are also conversations about Conti/TrickBot’s Diavol ransomware operation and 239 bitcoin addresses containing $13 million in payments, which were added to the Ransomwhere site.
239 Bitcoin addresses representing ~$13.1 million in payments from the Conti leak have been added to https://t.co/lBxHWCQm7S. The full dataset is available to download from the site.#ransomware #Conti
— Ransomwhere (@ransomwhere_) February 27, 2022
The leak of these messages is a severe blow to the ransomware operation, providing sensitive intelligence to researchers and law enforcement about their internal processes.
While the above snippets are only a tiny piece of the leaked conversations, we can expect to see far more information learned from the data in the coming weeks.
See Also: Recon Tool: Metagoofil
Messages leaked over Conti’s siding with Russia
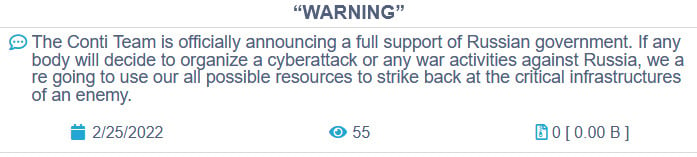
Earlier this week, the Conti ransomware operation published a blog post announcing their full support for the Russian government’s attack on Ukraine. They also warned that if anyone organized a cyberattack against Russia, the Conti gang would strike back at critical infrastructure.
After Ukrainian Conti affiliates grew upset over the siding with Russia, the Conti gang replaced their message with another one, stating that they “do not ally with any government” and that they “condemn the ongoing war.”
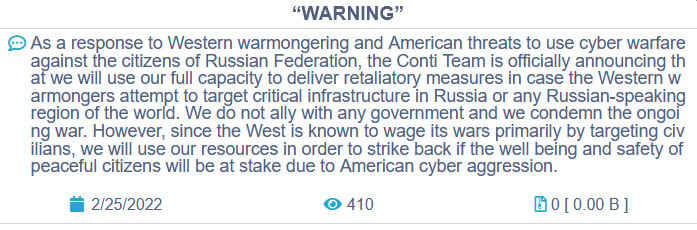
However, their change of heart came too late, and a Ukrainian security researcher who reportedly had access to Conti’s backend XMPP server emailed BleepingComputer and other journalists tonight with a link to the leaked data.
The reason shared as to why they leaked the private conversations can be read below:
Here is a friendly heads-up that the Conti gang has just lost all their sh*t. Please know this is true.
The link will take you to download an 1.tgz file that can be unpacked running tar -xzvf 1.tgz command in your terminal .
The contents of the first dump contain the chat communications (current, as of today and going to the past) of the Conti Ransomware gang. We promise it is very interesting.There are more dumps coming , stay tuned.
You can help the world by writing this as your top story.It is not malware or a joke.
This is being sent to many journalists and researchers.Thank you for your support
Glory to Ukraine!
See Also: How ILOVEYOU worm became the first global computer virus pandemic
Russia’s invasion of Ukraine has led to hackers, ransomware gangs, and security researchers picking sides in the conflict.
While some ransomware gangs have sided with Russia, others, like LockBit, are staying neutral.
On the other hand, Ukraine has asked volunteer researchers and hackers to join their “IT Army” to conduct cyberattacks on Russian targets, with many rallying to the call.
As for Conti, while this leak is embarrassing and provides immense insight into their operation, we are not likely to see them going away any time soon. With their recent take over of the stealthy BazarBackdoor malware and becoming an actual crime syndicate, they will, unfortunately, continue to be a threat.
Source: bleepingcomputer.com/
Source Link











