CoralRaider Exploits CDN Cache to Deploy Info-Stealer Malware
A recently discovered cyber campaign orchestrated by a threat actor known as CoralRaider has leveraged a content delivery network (CDN) cache to conceal information-stealing malware, targeting systems in the U.S., U.K., Germany, and Japan.
CoralRaider, identified as a financially motivated threat actor focused on acquiring credentials, financial data, and social media accounts, has deployed LummaC2, Rhadamanthys, and Cryptbot info stealers obtained from malware-as-a-service platforms available on underground forums.
Cisco Talos, a leading cybersecurity firm, has attributed this campaign to CoralRaider with moderate confidence, citing similarities in tactics, techniques, and procedures (TTPs) observed in previous attacks associated with the threat actor.
 CoralRaider’s attack spread
CoralRaider’s attack spread
Cisco Talos
CoralRaider Infection
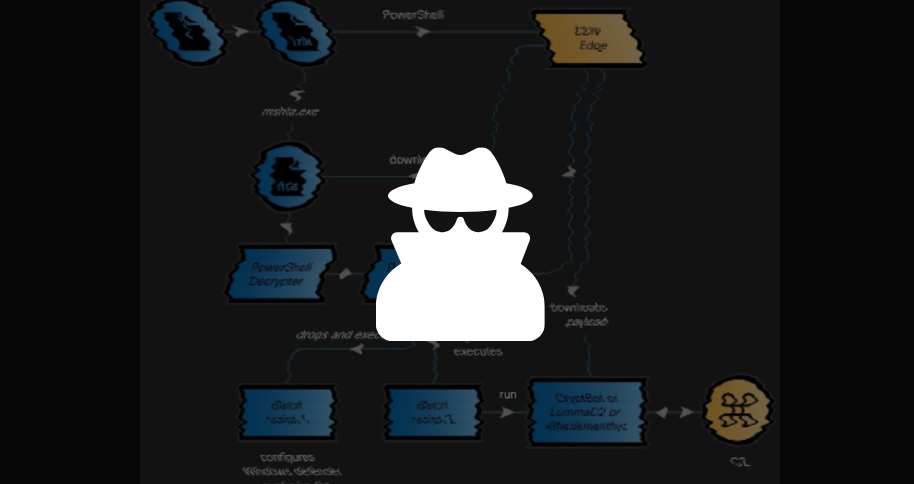
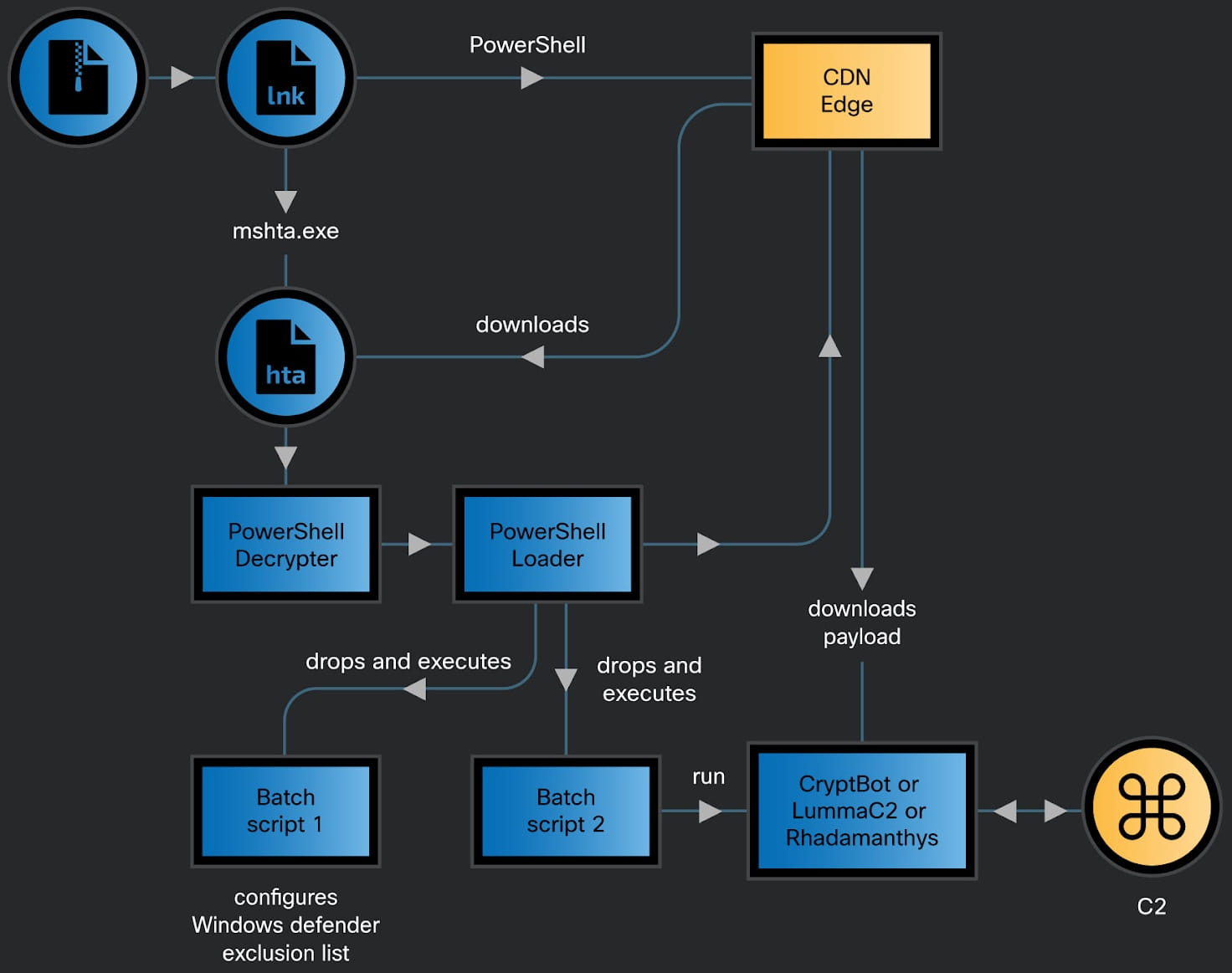
The CoralRaider infection chain begins with victims unwittingly opening an archive containing a malicious Windows shortcut file (.LNK). The delivery method of this archive remains unclear but could involve malicious email attachments, downloads from untrusted sources, or malvertising.
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Upon execution, the .LNK file triggers PowerShell commands that fetch and execute a heavily obfuscated HTML Application (HTA) file from an attacker-controlled subdomain hosted on the Bynny CDN platform. This technique utilizes the CDN cache as a delivery server to evade detection and bypass network defenses.
The HTA file contains JavaScript responsible for decoding and initiating a PowerShell decrypter script, which subsequently unpacks a second script designed to craft a batch file in a temporary folder. This batch script modifies Windows Defender exclusions to evade detection.
The threat actor utilizes a native Windows binary, FoDHelper.exe LoLBin, to edit registry keys and circumvent User Access Control (UAC) security features.
Following these steps, the PowerShell script proceeds to download and execute one of three info-stealing payloads: Cryptbot, LummaC2, or Rhadamanthys, stored in locations excluded from Windows Defender’s scanning.
 Infection chain diagram
Infection chain diagram
Cisco Talos
Trending: Offensive Security Tool: 403jump
CoralRaider’s preference for LummaC2 and Rhadamanthys stems from their recent updates, adding potent capabilities such as capturing RDP logins and reviving expired Google account cookies. Additionally, Cryptbot, although less prevalent, remains a formidable threat known for infecting a substantial number of computers.
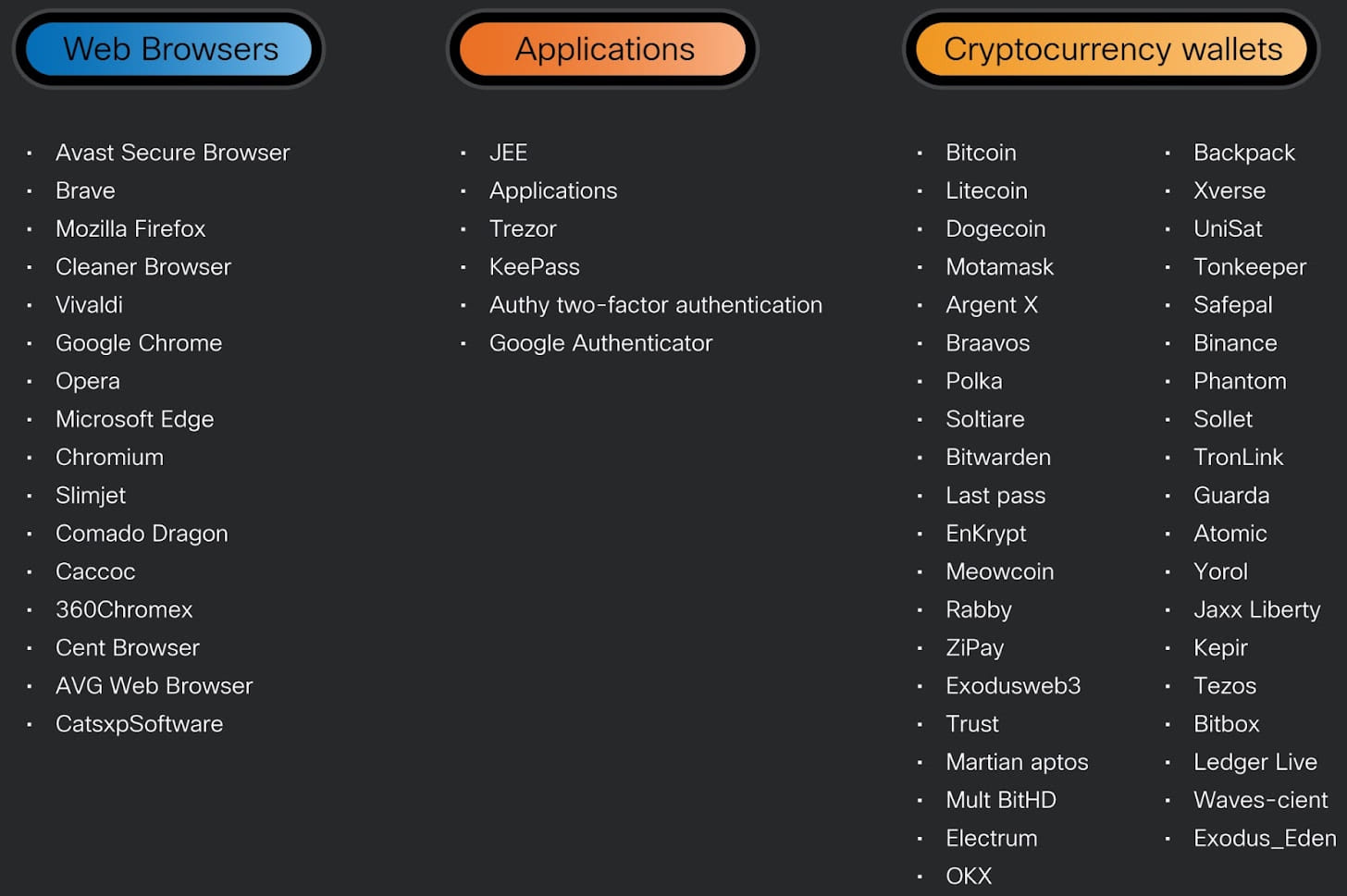
Cisco Talos underscores that the recent variant of Cryptbot deployed by CoralRaider, introduced in January, features enhanced obfuscation, anti-analysis mechanisms, and an expanded list of targeted applications, including databases for password managers and authenticator apps to pilfer cryptocurrency wallets protected by two-factor authentication.
 Apps targeted by latest Cryptbot version
Apps targeted by latest Cryptbot version
Cisco Talos
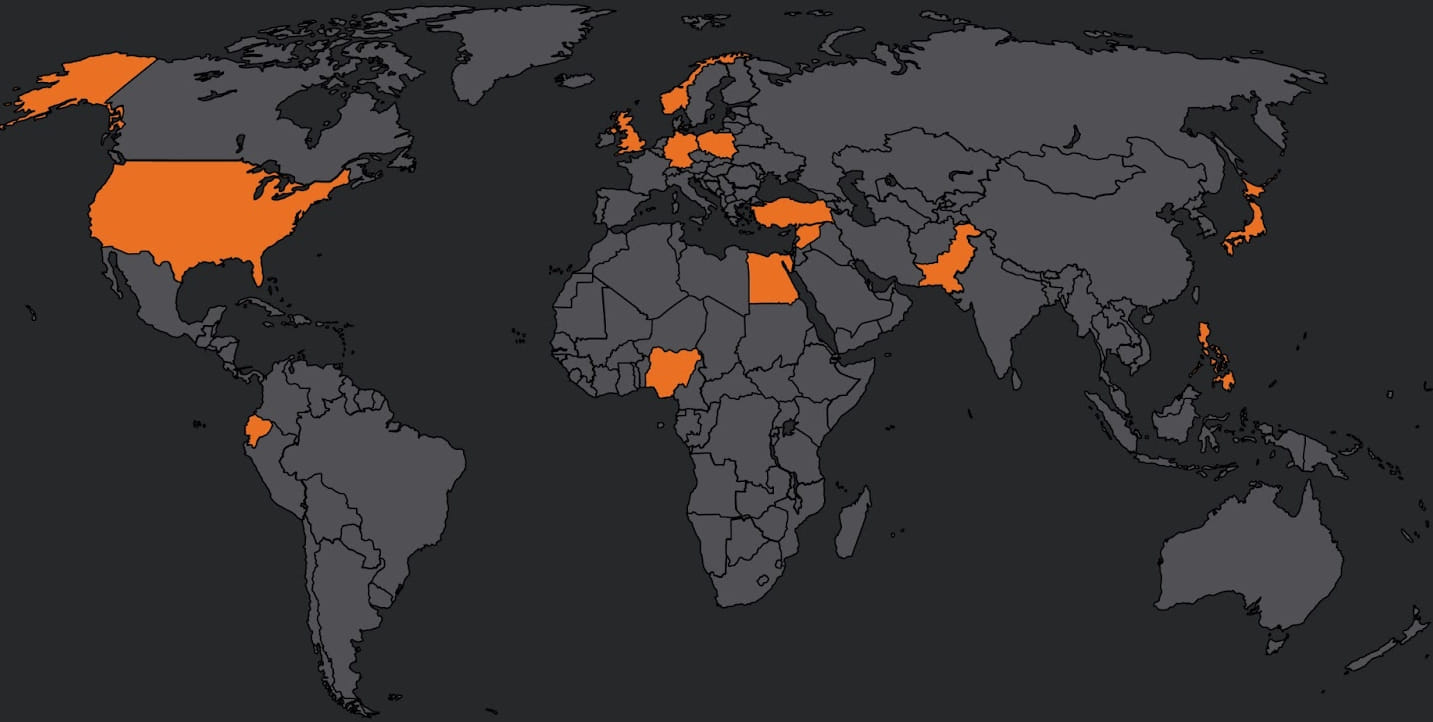
CoralRaider, operational since at least 2023 and believed to originate from Vietnam, previously relied on a Telegram bot for command-and-control (C2) functions and data exfiltration. While historically targeting Asian and Southeast Asian countries, CoralRaider’s latest operation has broadened its scope to encompass nations such as the U.S., Nigeria, Pakistan, Ecuador, Germany, Egypt, the U.K., Poland, the Philippines, Norway, Japan, Syria, and Turkey.
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













