Critical Authentication Bypass Flaw in MOVEit Transfer Under Active Exploitation

Threat actors are swiftly exploiting a newly discovered critical authentication bypass flaw in Progress MOVEit Transfer, less than a day after the vendor disclosed the vulnerability.
MOVEit Transfer is a managed file transfer (MFT) solution widely used in enterprise environments for secure file transfers between business partners and customers over SFTP, SCP, and HTTP protocols.
The critical flaw, identified as CVE-2024-5806, allows attackers to bypass authentication in the Secure File Transfer Protocol (SFTP) module, which handles file transfers over SSH. Exploiting this vulnerability, attackers can access sensitive data on the MOVEit Transfer server, upload, download, delete, or modify files, and intercept or tamper with file transfers.
Exploit Code in the Wild
The Shadowserver Foundation, a threat monitoring platform, reported that exploitation attempts began almost immediately after Progress published the bulletin on CVE-2024-5806. Hackers are actively targeting vulnerable endpoints.
https://x.com/Shadowserver/status/1805676078620401831
Network scans by Censys show approximately 2,700 internet-exposed MOVEit Transfer instances, primarily in the US, UK, Germany, Canada, and the Netherlands. However, the number of instances that haven’t applied the necessary security updates or mitigations remains unknown.
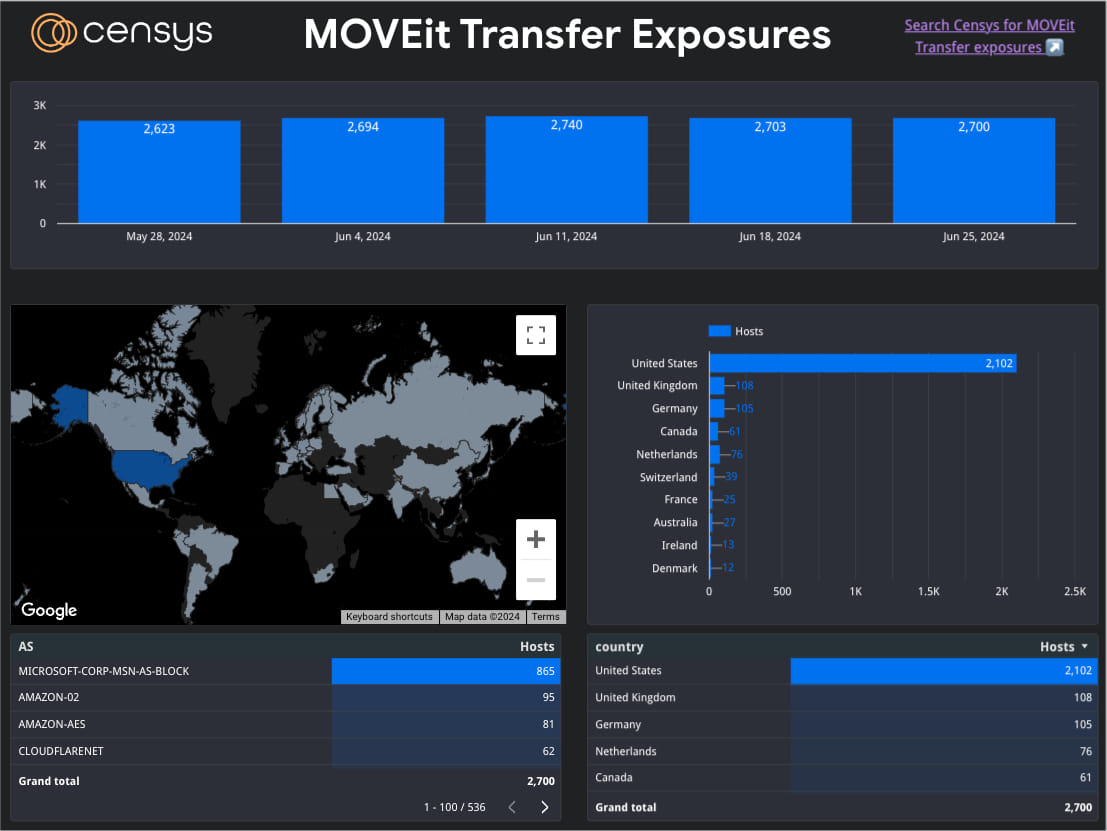 Internet-exposed MOVEit Transfer instances
Internet-exposed MOVEit Transfer instances
Source: Censys
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Shadowserver’s report follows the release of technical details about the vulnerability by the offensive security company watchTowr. They provided a thorough analysis of how attackers can manipulate SSH public key paths to force the server to authenticate using attacker-controlled paths, potentially exposing Net-NTLMv2 hashes.
Additionally, proof-of-concept exploit code for CVE-2024-5806 is publicly available from watchTowr and vulnerability researchers Sina Kheirkhah and Aliz Hammond. This public availability is likely to accelerate the pace of attacks, making it crucial for organizations to apply the related security updates and mitigations immediately.
Patches for CVE-2024-5806
Progress has released patches for the following affected MOVEit Transfer versions:
- 2023.0.0 before 2023.0.11
- 2023.1.0 before 2023.1.6
- 2024.0.0 before 2024.0.2
These fixes are available on the Progress Community portal. Customers without a current maintenance agreement should contact the Renewals team or their Progress partner representative to resolve the issue promptly.
MOVEit Cloud customers do not need to take any action, as patches have already been automatically deployed.
Trending: Offensive Security Tool: Freeway
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













