Critical Flaw Exposes 92,000 D-Link NAS Devices: Arbitrary Command Injection and Backdoor Revealed

A recent disclosure by threat researcher ‘Netsecfish’ has unveiled severe vulnerabilities affecting multiple end-of-life D-Link Network Attached Storage (NAS) device models. The flaws, identified as CVE-2024-3273, involve an arbitrary command injection and a hardcoded backdoor within the ‘/cgi-bin/nas_sharing.cgi’ script’s HTTP GET Request Handler component.
The vulnerability stems from two critical issues:
- Hardcoded Backdoor: The presence of a hardcoded account (‘messagebus’ with an empty password) facilitates unauthorized access.
- Arbitrary Command Injection: A flaw in the “system” parameter allows attackers to execute arbitrary commands remotely by injecting base64-encoded commands via HTTP GET requests.
When exploited together, these vulnerabilities enable threat actors to gain unauthorized access to sensitive information, manipulate system configurations, or induce denial of service conditions.
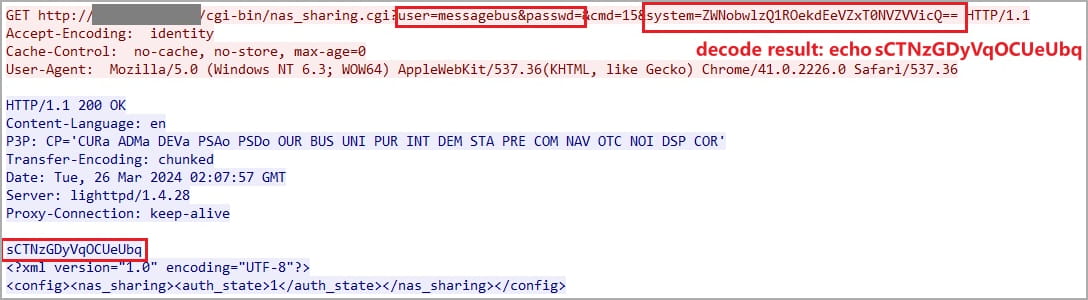 Example of the malicious request (Netsecfish|GitHub)
Example of the malicious request (Netsecfish|GitHub)
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Impacted D-Link NAS device models include:
- DNS-320L (Versions 1.11, 1.03.0904.2013, 1.01.0702.2013)
- DNS-325 (Version 1.01)
- DNS-327L (Versions 1.09, 1.00.0409.2013)
- DNS-340L (Version 1.08)
According to Netsecfish’s network scans, over 92,000 vulnerable D-Link NAS devices are exposed online, making them susceptible to exploitation through these critical flaws.
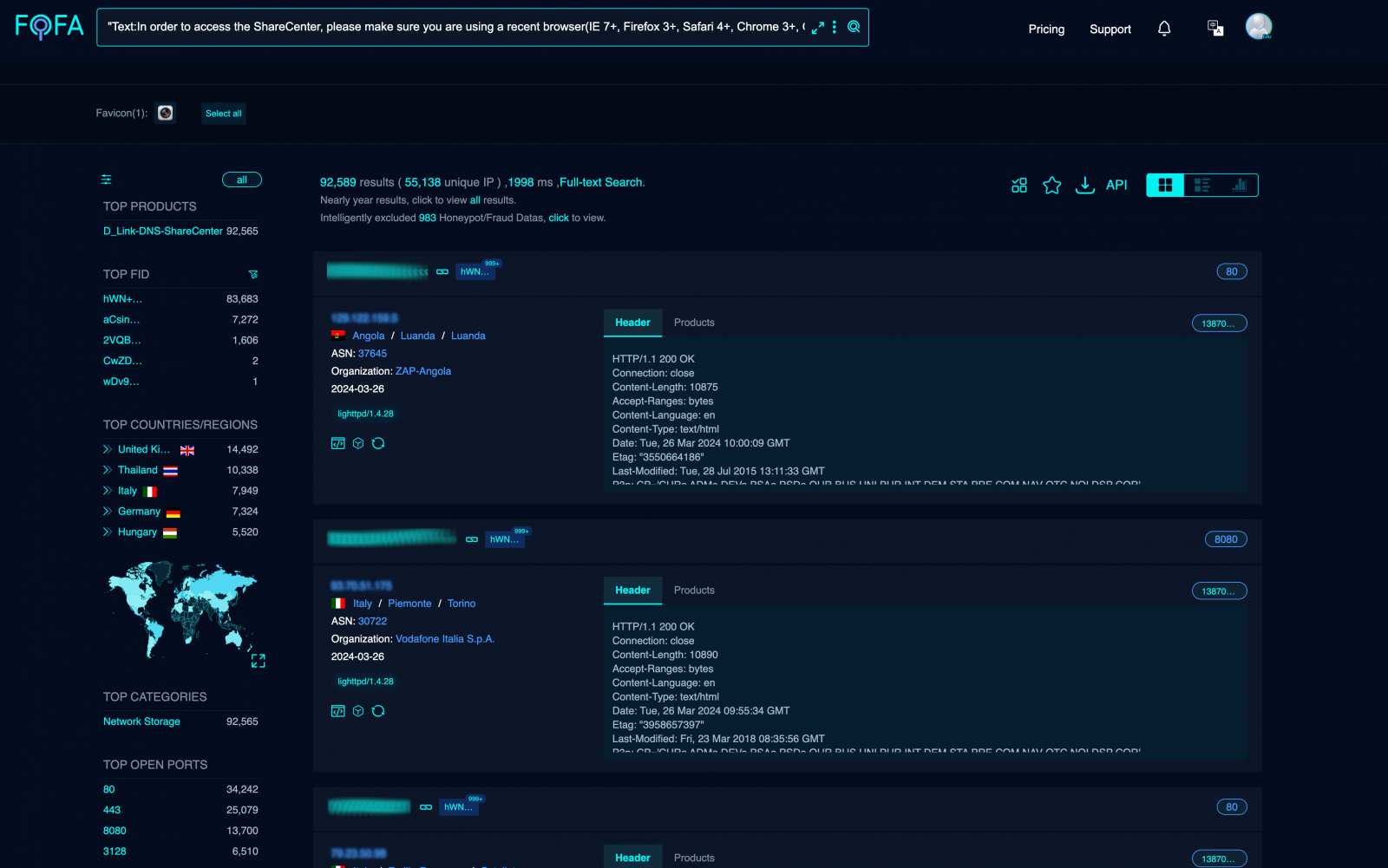 Internet scan results (Netsecfish|GitHub)
Internet scan results (Netsecfish|GitHub)
No patches available
No patches are available for these end-of-life devices, as confirmed by D-Link, as they have reached the end of service life and are no longer supported. D-Link advises users to retire these devices and replace them with supported alternatives that receive regular firmware updates.
Trending: Deep Dive to Fuzzing for Maximum Impact
Trending: OSINT Tool: NetScout


