Critical Flaw in Popular WordPress Plugin Puts Millions of Websites at Risk
Wordfence has identified a severe authentication bypass vulnerability in the WordPress plugin ‘Really Simple Security’, previously known as ‘Really Simple SSL’. This critical flaw affects both the free and Pro versions of the plugin, which is used on over four million websites. The vulnerability, designated as CVE-2024-10924, could allow remote attackers to gain full administrative access to compromised sites.
Key Points of the Vulnerability
- Discovery and Disclosure: The flaw was discovered by Wordfence researcher István Márton on November 6, 2024, and publicly disclosed shortly thereafter.
- Affected Versions: Plugin versions from 9.0.0 to 9.1.1.1 are impacted. The issue has been fixed in version 9.1.2, released on November 12 for Pro users and November 14 for free users.
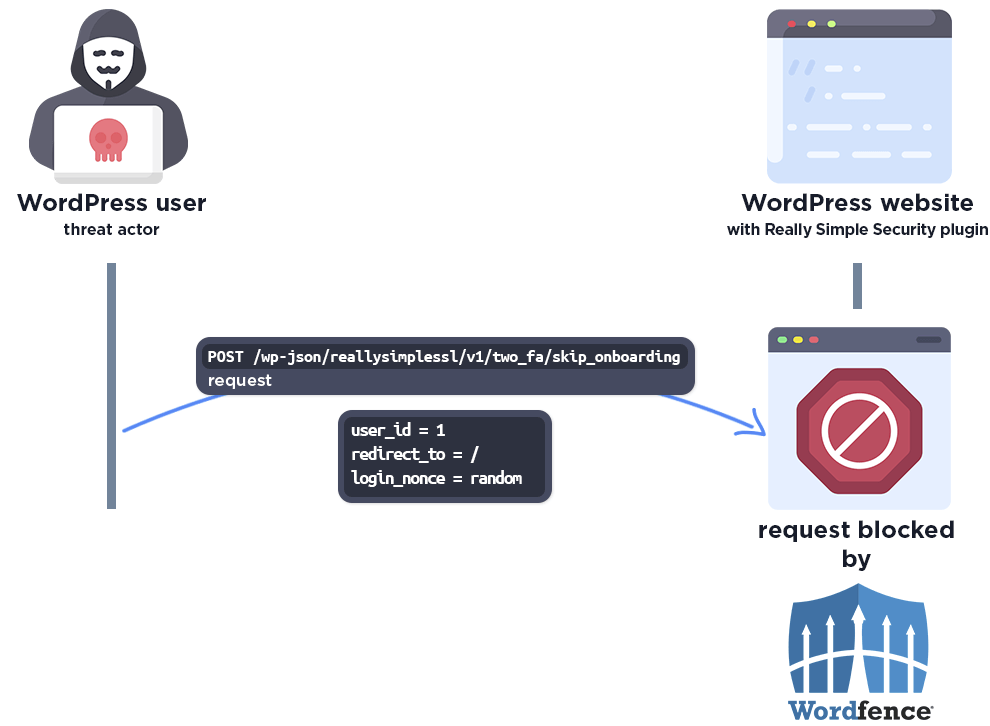
- Nature of the Flaw: The vulnerability is rooted in improper handling of user authentication within the plugin’s two-factor authentication (2FA) REST API actions. Specifically, the ‘check_login_and_get_user()’ function fails to reject invalid ‘login_nonce’ values, allowing unauthorized access via the ‘user_id’ parameter alone.
Exploitation and Impact
- Mass Exploitation Potential: The flaw can be exploited en masse using automated scripts, potentially leading to large-scale website takeover campaigns.
- Immediate Threat: Given the critical nature of the vulnerability, Wordfence has recommended that hosting providers force-update the plugin on customer sites and scan their databases to ensure no vulnerable versions are in use.
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Technical Details
- Authentication Bypass Mechanism: The flaw lies in the handling of the ‘login_nonce’ parameter. When this parameter is invalid, the ‘check_login_and_get_user()’ function improperly invokes ‘authenticate_and_redirect()’, allowing authentication based solely on ‘user_id’.
- 2FA Impact: Although 2FA is disabled by default, many administrators enable it for enhanced security. Ironically, this configuration makes their sites vulnerable to the flaw.
The Wordfence firewall rule detects the malicious REST API action and blocks the request.
Mitigation and Recommendations
- Immediate Update Required: Users must update to version 9.1.2 immediately. The update has been coordinated with WordPress.org to ensure force security updates are applied to users’ sites.
- Pro Version Users: Users of the Pro version, whose auto-updates are disabled post-license expiration, need to manually update to the latest version.
- Verification: Administrators should verify that their sites are running the latest version and monitor for any signs of unauthorized access.
Trending: Offensive Security Tool: emp3r0r
Current Statistics and Exposure
- As of the latest update, approximately 450,000 downloads of the updated version have been logged, leaving 3.5 million sites potentially exposed to the vulnerability.
Wordfence has emphasized the critical nature of this vulnerability, marking it as one of the most severe in their 12-year history of vulnerability reporting.
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com