Critical Flaw – JetBrains Urges Immediate Patching of TeamCity Servers

JetBrains has issued an urgent call to action for customers to swiftly patch their TeamCity On-Premises servers in response to a critical authentication bypass vulnerability, identified as CVE-2024-23917. This severe flaw, affecting all versions of TeamCity On-Premises from 2017.1 through 2023.11.2, poses a grave risk of enabling attackers to seize control of vulnerable instances with admin privileges.
JetBrains emphasized the importance of updating servers to version 2023.11.3 to address the vulnerability promptly. For users unable to immediately upgrade, a security patch plugin is available to secure servers running TeamCity 2018.2+ and versions 2017.1, 2017.2, and 2018.1.
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Acknowledging the urgency of the situation, JetBrains advised temporarily restricting public access to servers if immediate mitigation is not feasible. While JetBrains confirmed that all TeamCity Cloud servers have been patched, it remains undisclosed whether CVE-2024-23917 has been exploited in the wild to compromise Internet-exposed TeamCity On-Premises servers.
Shadowserver’s monitoring has identified over 2,000 exposed TeamCity servers online, heightening the urgency for mitigation efforts. This vulnerability bears resemblance to a prior exploit, CVE-2023-42793, which was leveraged by the APT29 hacking group and various ransomware gangs in widespread attacks.
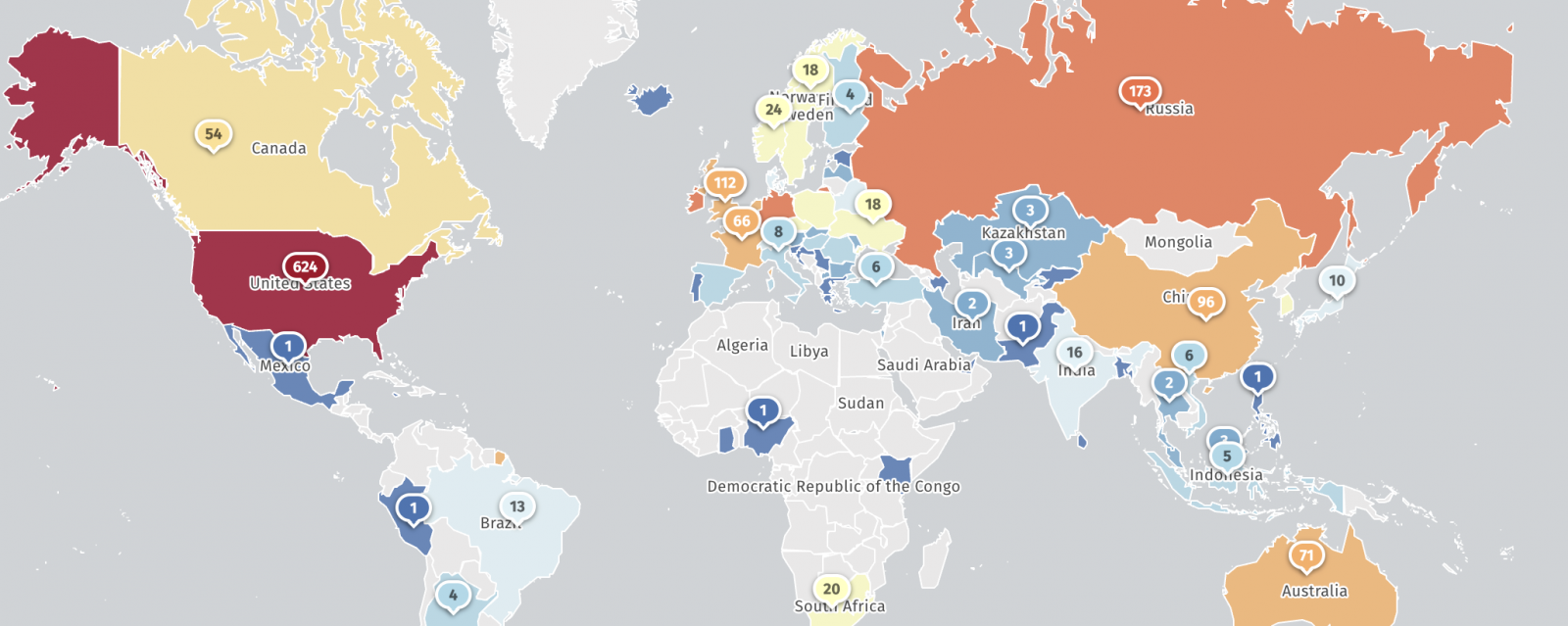 TeamCity servers exposed online (Shadowserver)
TeamCity servers exposed online (Shadowserver)
Trending: Recon Tool: go-dork


