Critical Juniper Vulnerabilities Spark Urgent CISA Warning for Federal Agencies

The Cybersecurity and Infrastructure Security Agency (CISA) has issued a critical warning to federal agencies, urging immediate action to secure Juniper devices on their networks.The urgency stems from four vulnerabilities identified in Juniper’s J-Web interface, namely CVE-2023-36844, CVE-2023-36845, CVE-2023-36846, and CVE-2023-36847, which have already been exploited in remote code execution (RCE) attacks.
This advisory comes on the heels of Juniper’s recent update, confirming successful exploitation of the vulnerabilities in the wild. Juniper’s Security Incident Response Team (SIRT) has recommended an urgent upgrade for customers, emphasizing the gravity of the situation.
ShadowServer, a threat monitoring service, detected exploitation attempts as early as August 25th, a mere week after Juniper released security updates. watchTowr Labs also contributed to the urgency by releasing a proof-of-concept (PoC) exploit, further emphasizing the critical nature of the vulnerabilities.
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
According to ShadowServer data, over 10,000 Juniper devices with exposed J-Web interfaces are at risk, with a significant concentration in South Korea. Administrators are strongly advised to take immediate action by either upgrading JunOS to the latest release or, at the very least, restricting internet access to the J-Web interface to eliminate the attack vector.
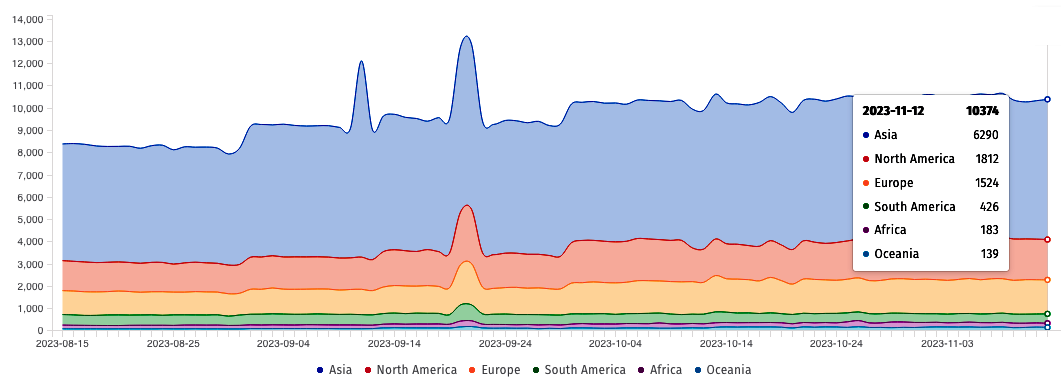 Internet-exposed Juniper devices (Shadowserver)
Internet-exposed Juniper devices (Shadowserver)
In a notable move, these four actively exploited Juniper vulnerabilities have been added to CISA’s Known Exploited Vulnerabilities Catalog, underlining their status as frequent attack vectors. This addition triggers a binding operational directive (BOD 22-01) requiring U.S. Federal Civilian Executive Branch Agencies to secure Juniper devices within an accelerated timeframe. The federal agencies are mandated to complete the upgrading process by November 17th, marking a swift response to the potential risks posed by these vulnerabilities.
Trending: Jeff Foley – OWASP Amass Founder
Trending: Offensive Security Tool: Ghauri
While the directive primarily targets federal agencies, CISA strongly encourages all organizations, including private companies, to prioritize the patching of these vulnerabilities promptly. This proactive approach aligns with CISA’s ongoing efforts to enhance the security posture of critical infrastructure, ensuring robust defense mechanisms against evolving cyber threats.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













