Critical OpenWrt Vulnerability Allowed Potential Malicious Firmware Distribution via Attended Sysupgrade

A critical vulnerability (CVE-2024-54143) in OpenWrt’s Attended Sysupgrade feature, used to create custom firmware images, could have been exploited to distribute malicious firmware packages.
What Is OpenWrt?
OpenWrt is a popular, highly customizable Linux-based operating system for embedded devices, especially routers and IoT hardware. It supports devices from major brands like ASUS, D-Link, Belkin, and many others, offering advanced features and greater flexibility compared to stock firmware.
The Vulnerability
Flatt Security researcher RyotaK discovered the issue during a routine home lab upgrade. The flaw, rated critical with a CVSS v4 score of 9.3, was found in OpenWrt’s Attended Sysupgrade (ASU) service. This feature simplifies upgrading devices by preserving packages and settings during firmware updates.
Two Main Issues Identified:
Command Injection via Package Names:
- The
sysupgrade.openwrt.orgservice processes inputs through commands in a containerized environment. - Improper handling of the
makecommand allowed arbitrary command injection via manipulated package names.
- The
Hash Truncation Vulnerability:
- The service uses a 12-character truncated SHA-256 hash (48 bits) for caching build artifacts.
- This makes brute-forcing collisions feasible, enabling attackers to reuse cache keys from legitimate firmware builds.
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Exploit Demonstration
By combining these flaws, RyotaK demonstrated that it was possible to modify legitimate firmware artifacts and serve malicious firmware. Using Hashcat on an RTX 4090 GPU, the researcher brute-forced hash collisions to overwrite firmware builds.
The result? Malicious firmware could be distributed to unsuspecting users through poisoned images, compromising their devices.
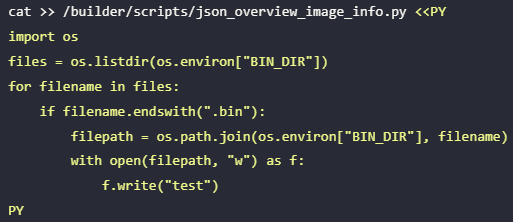 Python script used for overwriting legitimate firmware builds
Python script used for overwriting legitimate firmware builds
Source: Flatt Security
OpenWrt’s Response
OpenWrt’s team acted swiftly upon receiving the private report:
- Service Taken Down: The sysupgrade.openwrt.org service was disabled immediately.
- Rapid Fix and Recovery: The vulnerability was patched, and the service was restored within 3 hours on December 4, 2024.
The team confirmed no evidence of malicious activity during the 7-day log window they were able to review. However, they advised users to regenerate and reinstall firmware images to eliminate any potential risk
Trending: Recon Tool: Argus
Recommendations for Users
Upgrade Firmware Immediately:
- Perform an in-place upgrade with the same firmware version to ensure a clean, safe image.
Self-Hosted ASU Instances:
- If running a public ASU service, update it immediately to include the latest fixes.
Verify Downloads:
- While there is no evidence of compromised images from
downloads.openwrt.org, users should remain cautious and re-download firmware if necessary.
- While there is no evidence of compromised images from
Stay Updated:
- Follow OpenWrt announcements for further guidance and updates.
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













