Critical Python URL Parsing Flaw Allows Bypass of Filtering Methods

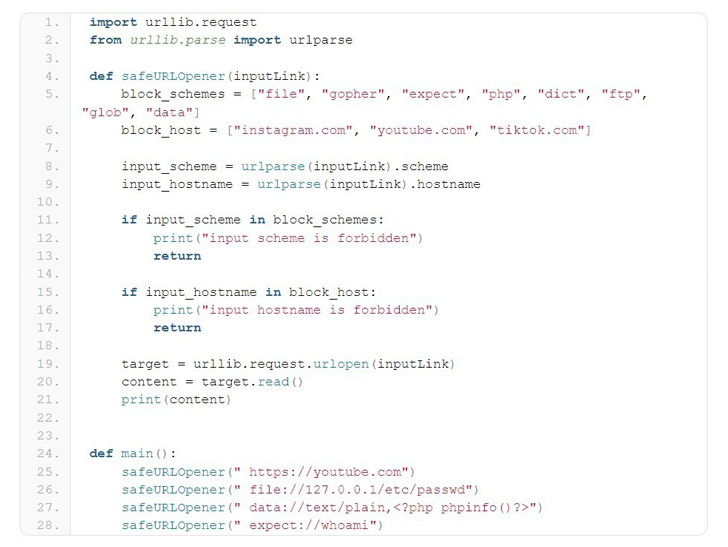
A significant security vulnerability has been unveiled in Python’s URL parsing function, which could potentially be exploited to evade domain or protocol filtering mechanisms that rely on blocklists. The flaw, identified as CVE-2023-24329 and credited to security researcher Yebo Cao, has a CVSS score of 7.5 and could lead to arbitrary file reads and command execution. The CERT Coordination Center (CERT/CC) published an advisory on this issue, emphasizing that the vulnerability arises when the entire URL commences with blank characters, thereby rendering domain and scheme filtering methods ineffective.
This security concern has prompted action from the Python community, resulting in the release of patched versions to address the vulnerability. The flaw has been mitigated in the following versions:
- Version 3.12 and above
- Version 3.11.x starting from 3.11.4
- Version 3.10.x starting from 3.10.12
- Version 3.9.x starting from 3.9.17
- Version 3.8.x starting from 3.8.17
- Version 3.7.x starting from 3.7.17
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
The urllib.parse function is widely utilized for breaking down URLs into their individual components or assembling components into a complete URL string. However, CVE-2023-24329 underscores a vulnerability due to inadequate input validation. This vulnerability allows threat actors to bypass blocklisting methods by providing a URL that initiates with blank characters, such as ” https://youtube[.]com“.
Security researcher Yebo Cao remarked, “While blocklisting may not be the most robust solution, it remains relevant in various scenarios. This vulnerability empowers attackers to elude the protection mechanisms devised by developers for schemes and hosts. It is anticipated that this vulnerability could facilitate Server-Side Request Forgery (SSRF) and Remote Code Execution (RCE) in a wide array of contexts.”
Trending: Offensive Security Tool: Nucleimonst3r
This disclosure takes place against the backdrop of recent research that has brought attention to security fixes within the Python language. Some of these fixes occur silently, lacking a corresponding Common Vulnerabilities and Exposures (CVE) identifier. This “silent” approach to code commits potentially exposes unpatched systems to the risk of exploitation by malicious actors, highlighting the significance of thorough and transparent security practices.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: thehackernews.com












