Critical RCE Vulnerability Threatens Thousands of Apache ActiveMQ Servers

Over three thousand internet-exposed Apache ActiveMQ servers are currently at risk due to a recently disclosed critical remote code execution (RCE) vulnerability. Apache ActiveMQ is a widely used open-source message broker that facilitates communication in enterprise environments. It supports various secure authentication and authorization mechanisms, making it a key component in systems where direct connectivity is not possible.
The vulnerability in question, CVE-2023-46604, is rated as critical and allows attackers to execute arbitrary shell commands by exploiting serialized class types in the OpenWire protocol. This could potentially lead to message interception, workflow disruption, data theft, and even lateral movement within the network.
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
Apache released fixes for this issue on October 27, 2023, with the recommended upgrade targets being versions:
- 5.15.16
- 5.16.7
- 5.17.6
- 5.18.3
Researchers from the threat monitoring service ShadowServer discovered a total of 7,249 servers accessible with ActiveMQ services. Of these, 3,329 were running a vulnerable version of ActiveMQ, leaving them exposed to remote code execution.
Trending: Jeff Foley – OWASP Amass Founder
Trending: Recon Tool: CHOMTE.SH
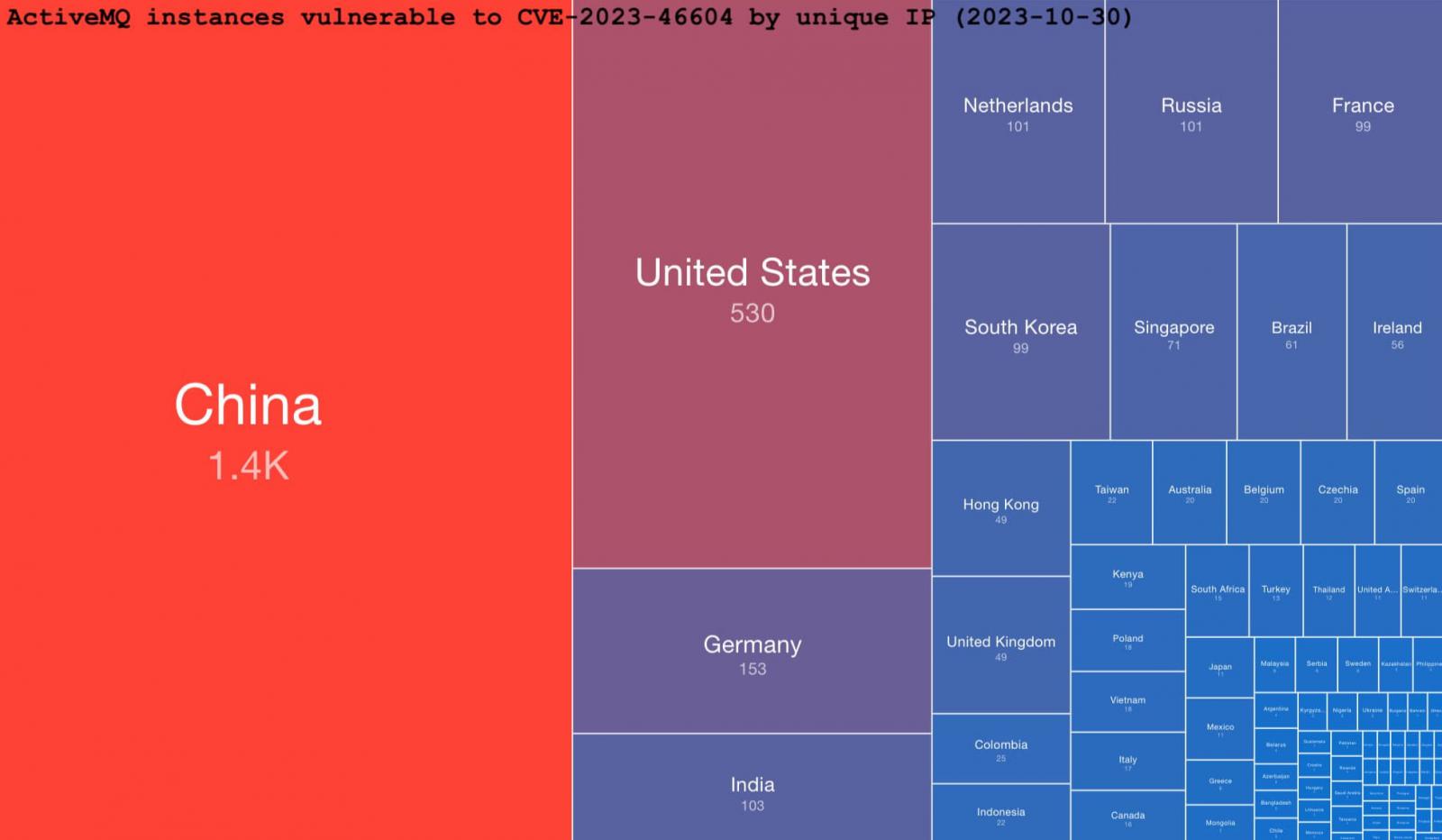 Vulnerable ActiveMQ servers as of October 30 (ShadowServer)
Vulnerable ActiveMQ servers as of October 30 (ShadowServer)
The majority of these vulnerable servers (1,400) are located in China, with the United States having 530, Germany with 153, and India, the Netherlands, Russia, France, and South Korea each having 100 or more exposed servers. With technical details on exploiting CVE-2023-46604 publicly available, applying the security updates is a time-sensitive matter.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com












