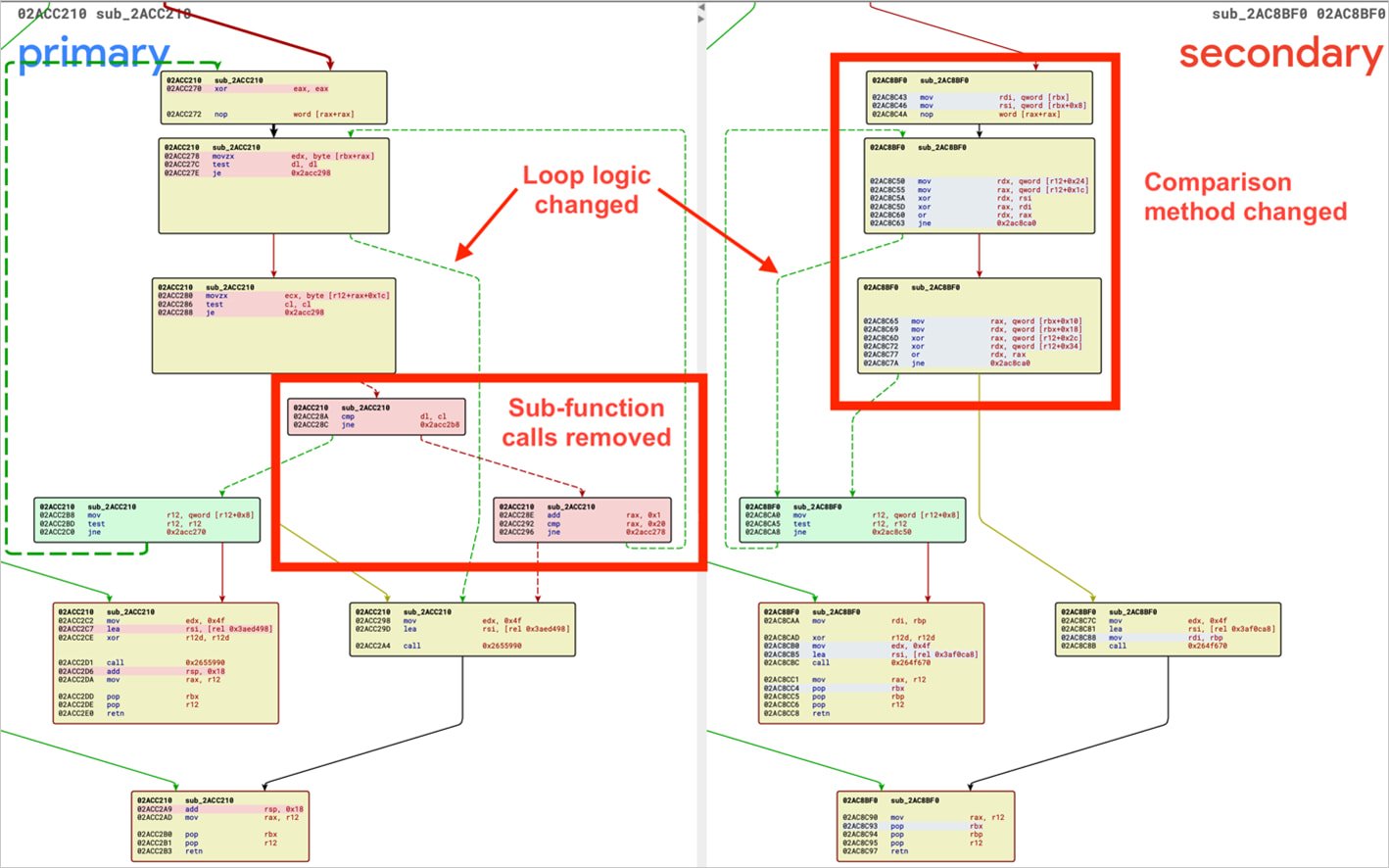
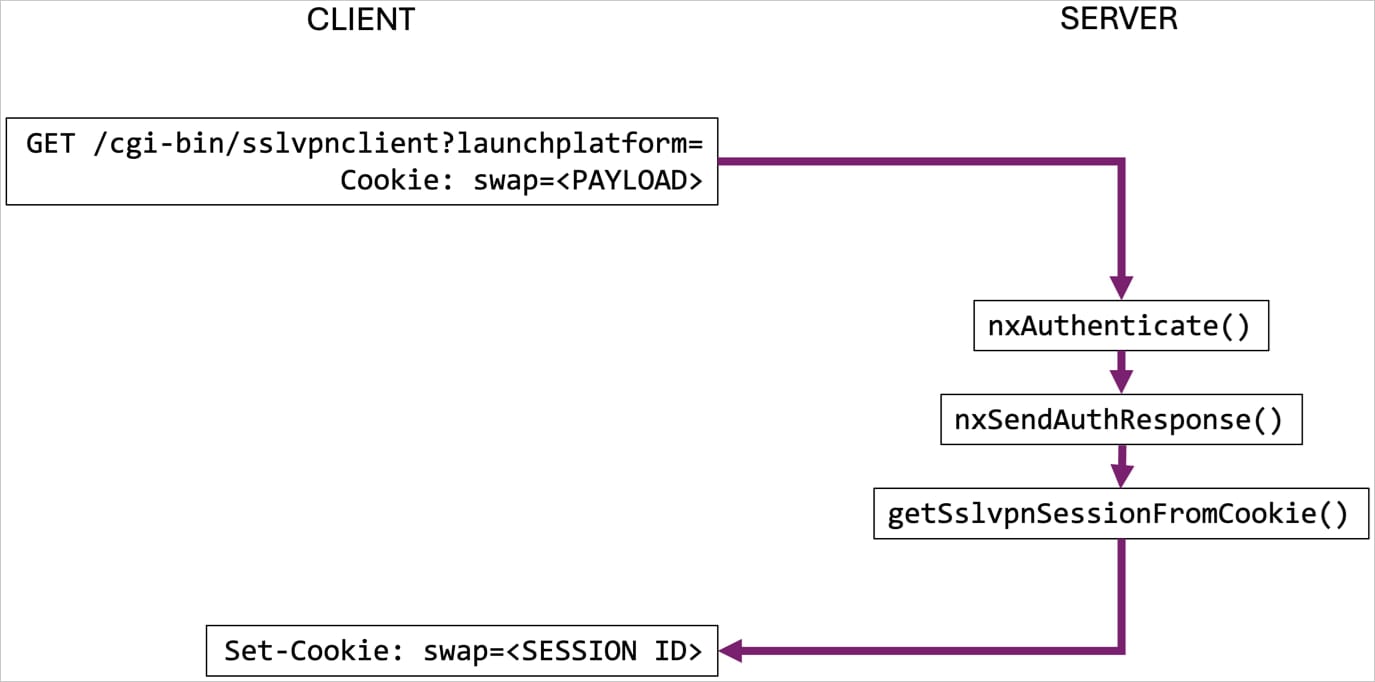
Critical SonicWall VPN Flaw Lets Hackers Hijack Sessions

Reading Time: 3 Minutes
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Impacted SonicOS Versions
- 7.1.x (up to 7.1.1-7058)
- 7.1.2-7019
- 8.0.0-8035
- Affects Gen 6 and Gen 7 SonicWall firewalls, including SOHO series devices.
Patch Availability
- Fixed in SonicOS 8.0.0-8037 and later, 7.0.1-5165 and higher, 7.1.3-7015 and higher, 6.5.5.1-6n and higher.
- SonicWall’s bulletin provides model-specific patch details.
Current Risk Level
- As of February 7, around 4,500 internet-exposed SonicWall SSL VPN servers remain unpatched.
- With the exploit details now public, attackers are expected to actively target vulnerable devices.
Action Required
- Apply firmware updates immediately to protect against attacks.
- Disable SSL VPN if not in use.
- Monitor VPN logs for unauthorized session activity.
- Implement multi-factor authentication (MFA) to add an extra security layer.
With an active proof-of-concept exploit now available, the risk of exploitation is high. Organizations using SonicWall SSL VPN should patch immediately to prevent unauthorized access.
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com