Critical Vulnerability in D-Link DIR-859 WiFi Routers Being Actively Exploited

Hackers are exploiting a severe vulnerability affecting all D-Link DIR-859 WiFi routers to steal account information, including passwords. This security issue, disclosed in January and tracked as CVE-2024-0769, has a severity score of 9.8 and involves a path traversal flaw leading to information disclosure.
Details of CVE-2024-0769
The flaw exists in the “fatlady.php” file of the D-Link DIR-859 router and impacts all firmware versions. This vulnerability allows attackers to leak session data, escalate privileges, and gain full control over the device via the admin panel.
Despite the DIR-859 model reaching its end-of-life (EoL) and no longer receiving updates, D-Link released a security advisory explaining the flaw. However, no patch will be provided for CVE-2024-0769, so owners are strongly advised to switch to a supported device immediately.
Active Exploitation in the Wild
Threat monitoring platform GreyNoise has detected active exploitation of CVE-2024-0769. Hackers are using a slight variation of the public exploit to target the ‘DEVICE.ACCOUNT.xml’ file, which contains account names, passwords, user groups, and user descriptions.
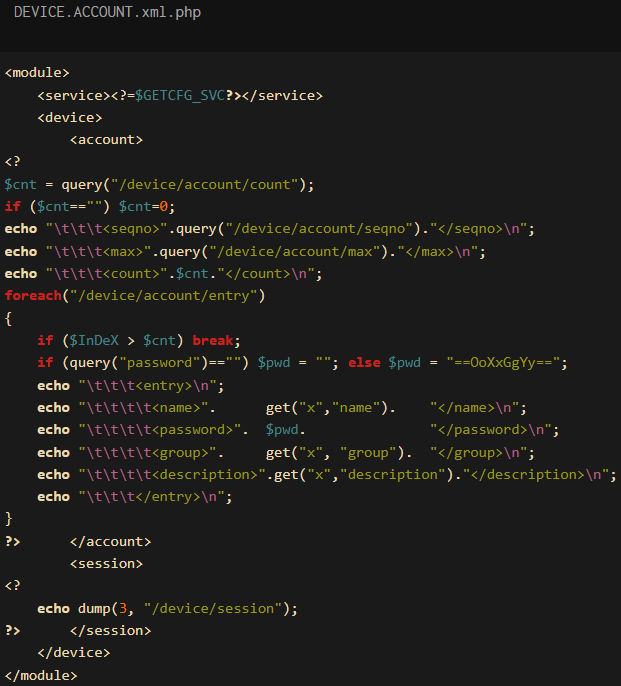 Contents of the retrieved configuration file
Contents of the retrieved configuration file
Source: GreyNoise
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
The attack uses a malicious POST request to ‘/hedwig.cgi,’ exploiting the CVE-2024-0769 vulnerability to access sensitive configuration files via the ‘fatlady.php’ file. This file potentially contains user credentials, allowing attackers to take over the device.
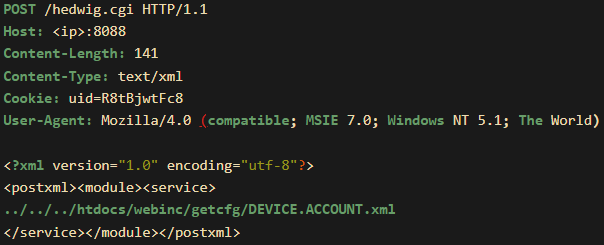
Malicious POST request
Source: GreyNoise
Motivations and Potential Impacts
While GreyNoise has not determined the attackers’ motivations, the targeting of user passwords indicates an intention to take full control of the device. Such control could have severe implications for the security of the network and data privacy.
“It is unclear at this time what the intended use of this disclosed information is,” the researchers explain. “It should be noted that these devices will never receive a patch. Any information disclosed from the device will remain valuable to attackers for the lifetime of the device as long as it remains internet-facing” – GreyNoise
Broader Implications and Defensive Measures
The public proof-of-concept exploit, which current attacks rely on, targets the ‘DHCPS6.BRIDGE-1.xml’ file but could be adapted to target other configuration files, including:
- ACL.xml.php: Access control lists configurations
- ROUTE.STATIC.xml.php: Static routing configurations
- INET.WAN-1.xml.php: WAN interface configurations
- WIFI.WLAN-1.xml.php: WiFi settings
Trending: Offensive Security Tool: Genzai
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













