Critical Vulnerability in Visual Studio Code, Malicious Extensions Can Steal Authentication Tokens

A significant security vulnerability has been unveiled in Microsoft’s Visual Studio Code (VS Code), the widely used code editor and development environment. This flaw enables malicious extensions to extract authentication tokens stored within Windows, Linux, and macOS credential managers.
Authentication tokens, pivotal for integrating with third-party services and APIs such as Git, GitHub, and other coding platforms, are at the core of seamless software development. Exploiting this vulnerability could lead to severe consequences for organizations, including unauthorized system access and potential data breaches.
Malicious extensions stealing secrets
Cycode researchers, who brought this flaw to light, found that the root cause lies in the lack of segregation of authentication tokens within VS Code’s ‘Secret Storage.’ This storage system uses Keytar, VS Code’s communication wrapper for Windows credential manager, macOS keychain, and Linux keyring.
Regrettably, any extension running within VS Code, even if malicious, can access the Secret Storage and misuse Keytar to retrieve stored tokens.
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
Cycode’s Alex Ilgayev revealed that except for the integrated GitHub and Microsoft authentication, all saved credentials stem from third-party extensions. These could be official Microsoft extensions like Git, Azure, Docker/Kubernetes, or third-party ones such as CircleCI, GitLab, and AWS.
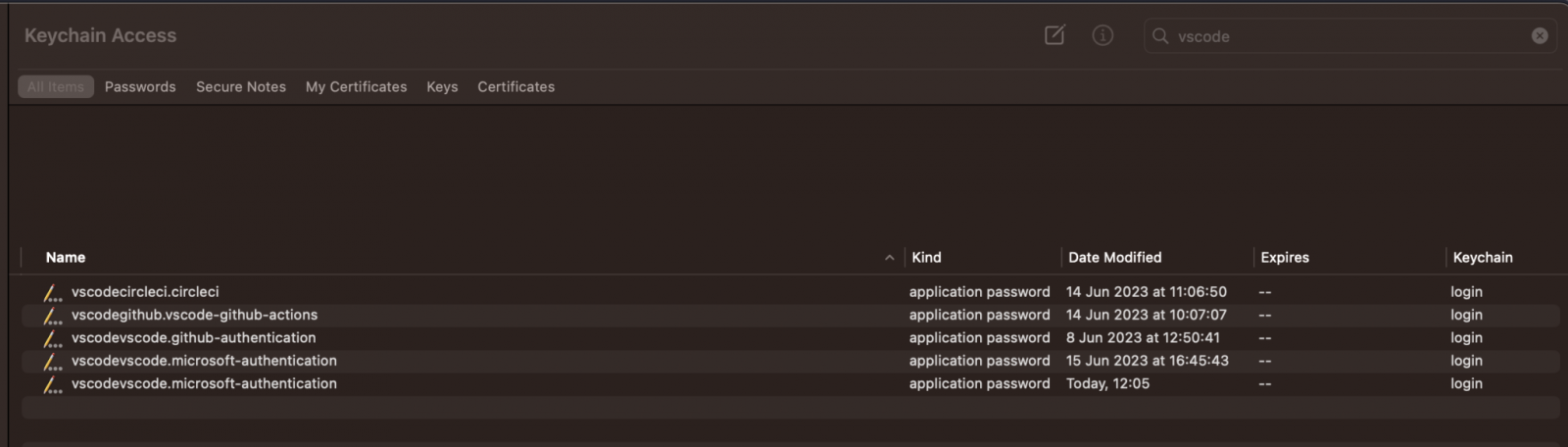 Keychain containing login passwords
Keychain containing login passwords
Source: Cycode
The researchers initially experimented with a malicious extension targeting CircleCI, exposing its secure token and even transmitting it to their server. They then developed a more versatile attack method, uncovering a potential vulnerability in VS Code’s security framework.
It was discovered that any VS Code extension is authorized to access the keychain as the operating system has already granted access to it. Cycode managed to develop a proof-of-concept malicious extension that successfully retrieved tokens not only from other extensions but also from VS Code’s built-in login and sync functionalities for GitHub and Microsoft accounts.
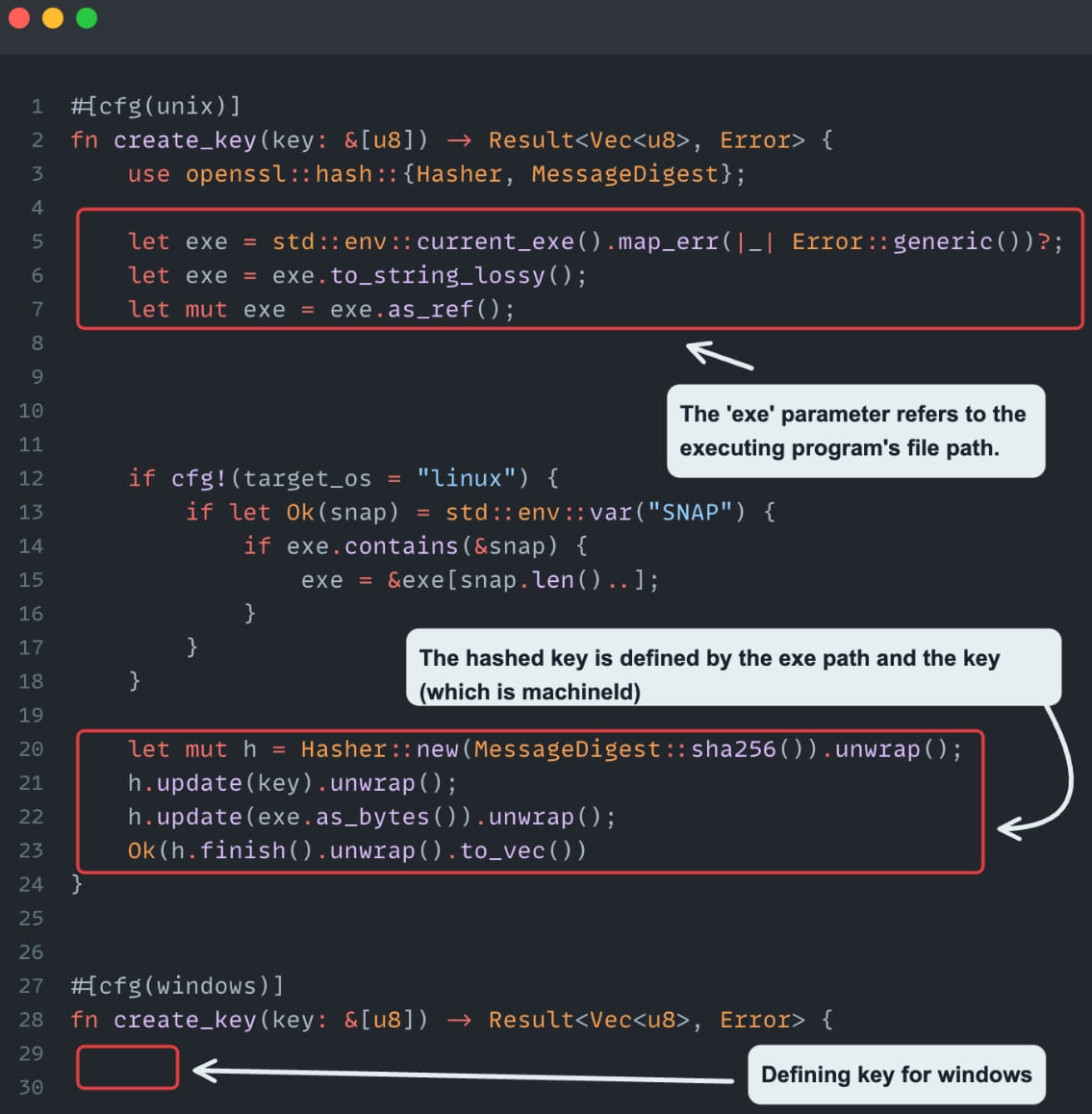 Info that helps decrypt secrets
Info that helps decrypt secrets
Source: Cycode
This exposed the potential for a “Token Stealing” attack.
The retrieved tokens were decrypted by a custom JS script run in VS Code’s Electron executable, deciphering and printing all passwords of locally installed extensions.
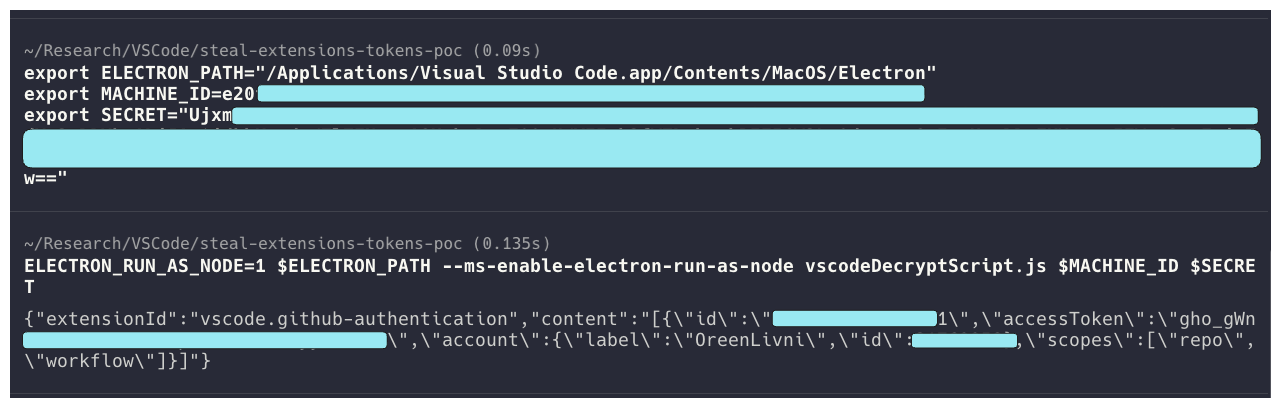
Source: Cycode
Trending: Recon Tool: RecoX
Moreover, a secondary vulnerability was detected, enabling anyone to manipulate ‘extensionId’ fields and trick VS Code into granting unauthorized access to another extension’s secure tokens. Cycode demonstrated this by mimicking CircleCI with their PoC extension, highlighting the ease with which replication of other extensions and subsequent access to their secrets can occur.
Despite disclosing the issue to Microsoft and providing a proof-of-concept extension two months ago, the tech giant opted to maintain the existing design of VS Code’s secret storage management framework. This decision has raised concerns within the cybersecurity community.
BleepingComputer has reached out to Microsoft for comments on this matter but has yet to receive a response to its inquiries.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com












