CryptoClippy: New Malware Targeting Users for Cryptocurrency Theft

CryptoClippy malware
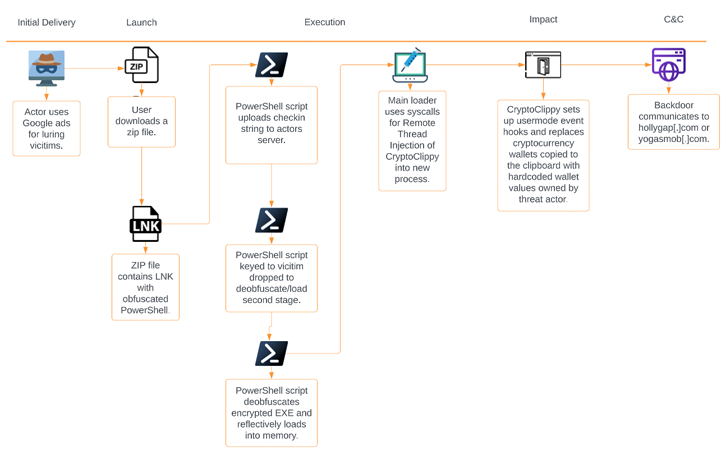
Portuguese users have recently become the target of a new form of malware, codenamed CryptoClippy. This particular malware is capable of stealing cryptocurrency as part of a malvertising campaign that entices users searching for “WhatsApp web” to rogue domains hosting the malware, according to a new report by Palo Alto Networks Unit 42.
CryptoClippy is a type of cryware known as clipper malware, which monitors a victim’s clipboard for content matching cryptocurrency addresses and replaces them with a wallet address under the control of the threat actor. The malware uses regular expressions to identify what type of cryptocurrency the address pertains to and then replaces the clipboard entry with a visually similar but adversary-controlled wallet address for the appropriate cryptocurrency. This means that when the victim pastes the address from the clipboard to conduct a transaction, they are unknowingly sending cryptocurrency directly to the threat actor.
The illicit scheme has reportedly netted the operators around $983 so far, with victims found across several industries including manufacturing, IT services, and real estate.
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
Sophisticated Malware Delivery Tactics Increase Threat to Portuguese Users
To deliver the malware to potential victims, the campaign leverages SEO poisoning techniques and traffic direction systems (TDS). The TDS checks whether the user’s preferred browser language is Portuguese and if so, redirects them to a rogue landing page, where they can become infected with CryptoClippy. Users who do not meet this criteria are simply redirected to the legitimate WhatsApp Web domain, without any malicious activity taking place, thus avoiding detection.
It’s worth noting that the use of poisoned search results to deliver malware has been adopted by other threat actors, most notably those associated with the GootLoader malware. This trend demonstrates a growing sophistication and effectiveness of these tactics in bypassing security measures and delivering malware to unsuspecting victims.
Trending: Offensive Security Tool: Nginxpwner
Users urged to remain vigilant against growing threats to personal data security
The findings come just days after SecurityScorecard reported on another form of malware called Lumma, which is capable of harvesting data from web browsers, cryptocurrency wallets, and various apps, including AnyDesk, FileZilla, KeePass, Steam, and Telegram.
As always, it’s crucial for users to remain vigilant and cautious when browsing the internet, especially when searching for popular services like WhatsApp Web. They should be careful not to click on suspicious links or download any suspicious files, and always use reputable anti-malware software to protect themselves against potential threats.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: thehackernews.com