Cybercriminals Exploit Apple iMessage to Bypass Phishing Protection

Cybercriminals are deploying a cunning tactic to bypass Apple iMessage’s built-in phishing protections, tricking users into re-enabling disabled links in phishing messages. This technique leverages human behavior to target unsuspecting victims and gain access to sensitive information.
How iMessage Phishing Protection Works
Apple’s iMessage automatically disables links in messages sent from unknown senders, including both email addresses and phone numbers. This protective measure prevents users from inadvertently clicking on malicious links.
However, Apple has confirmed that if users reply to these messages or add the sender to their contacts, the links become active again, effectively disabling iMessage’s phishing safeguards.
The Cybercriminals’ Strategy
Tricking Users into Responding
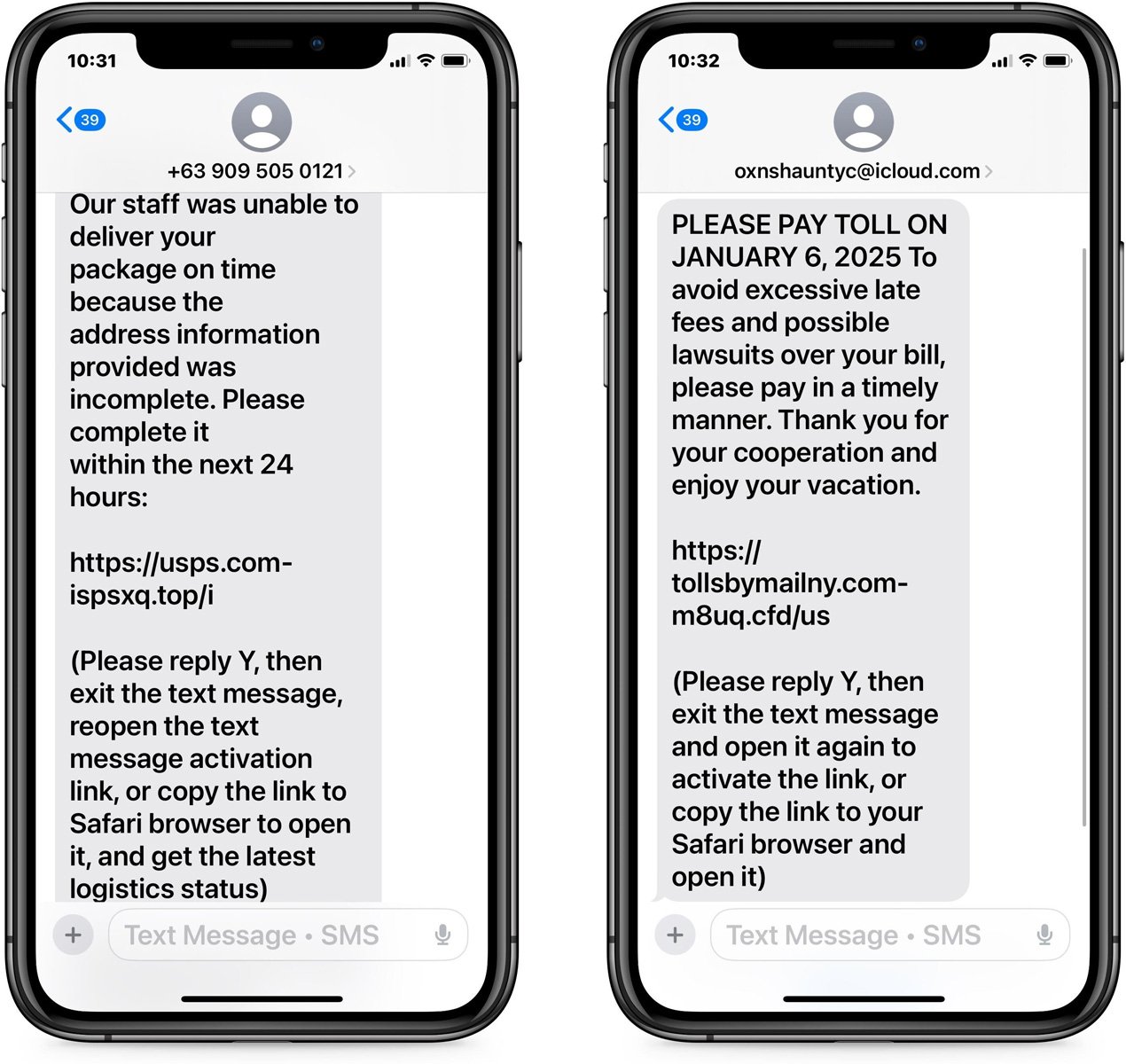
Recent smishing (SMS phishing) campaigns use familiar tactics to trick users into replying to their messages. Common examples include:- Fake USPS shipping issues
- Unpaid toll notifications
These messages often ask users to reply with “Y” or similar responses. For example:
“Please reply Y, then exit the text message, reopen the activation link, or copy the link to Safari browser to open it.”
By replying, users inadvertently enable the previously disabled links, making them accessible for clicking.
Behavioral Manipulation
Cybercriminals exploit the fact that users are accustomed to replying “STOP,” “YES,” or “NO” to confirm appointments or opt out of messages. This familiarity increases the likelihood of a reply, enabling the malicious links.
 SMS phishing attacks with disabled links
SMS phishing attacks with disabled links
Source: BleepingComputer
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Why This Tactic Works
- Trust in Familiar Prompts: Users often associate simple replies like “Y” with legitimate interactions.
- Targeting Vulnerable Populations: Older individuals or those less familiar with digital scams are more likely to fall for these tactics.
- Behavior Tracking: Even if users don’t click on the activated links, their reply confirms to the threat actor that the phone number is active and the recipient engages with texts, making them a prime target for future attacks.
Trending: Offensive Security Tool: XSRFProbe
How to Stay Safe
Do Not Reply to Unknown Messages
If you receive a message with disabled links or from an unknown sender asking you to reply, do not respond.Verify the Message
Contact the organization or company directly to confirm the authenticity of the message. Avoid relying on the information in the text.Educate Vulnerable Users
Help less tech-savvy individuals recognize phishing scams by showing them examples and explaining the risks of engaging with unknown messages.Use Third-Party Security Tools
Consider using additional anti-phishing tools or services to enhance your mobile security.
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













