Cybercriminals Exploit Cloudflare Tunnel for Malware Campaigns

Emerging Threat Using Cloudflare Tunnel
Researchers have identified a growing trend where threat actors are increasingly abusing the Cloudflare Tunnel service to distribute remote access trojans (RATs). First detected in February, this cybercriminal activity leverages the free TryCloudflare service to spread multiple RATs, including AsyncRAT, GuLoader, VenomRAT, Remcos RAT, and Xworm.
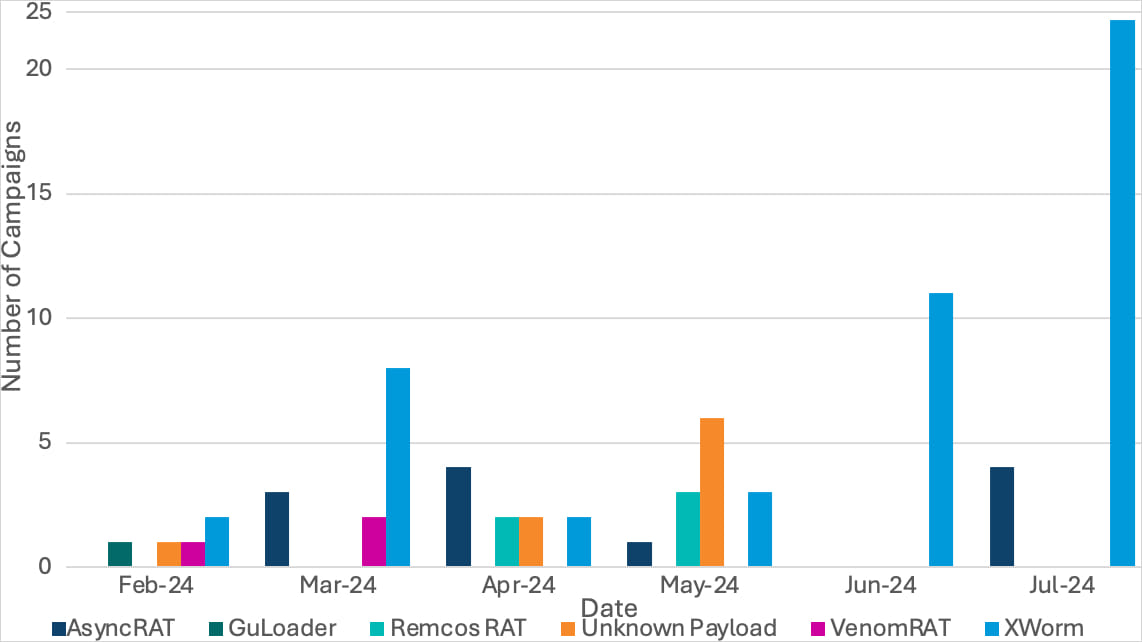 Campaigns attributed to the same activity cluster
Campaigns attributed to the same activity cluster
Source: Proofpoint
Cloudflare Tunnel Service Misuse
The Cloudflare Tunnel service allows for the proxying of traffic through an encrypted tunnel, providing secure and convenient access to local services and servers over the internet without exposing IP addresses. This service, intended to enhance security by eliminating the need to open public inbound ports or set up VPN connections, has been misused by threat actors to evade detection and gain remote access to compromised systems.
Temporary Subdomains for Malicious Activity
With TryCloudflare, users can create temporary tunnels to local servers without needing a Cloudflare account. Each tunnel generates a temporary random subdomain on the trycloudflare.com domain, routing traffic through Cloudflare’s network to the local server. Threat actors exploit this feature to mask their activities and evade detection.
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Latest Campaign Details
In a recent report by Proofpoint, cybersecurity experts observed malware activity targeting organizations in the law, finance, manufacturing, and technology sectors. The attackers use malicious .LNK files hosted on the legitimate TryCloudflare domain, luring targets with tax-themed emails that contain URLs or attachments leading to the LNK payload. Once launched, the payload executes BAT or CMD scripts that deploy PowerShell, eventually downloading Python installers for the final payload.
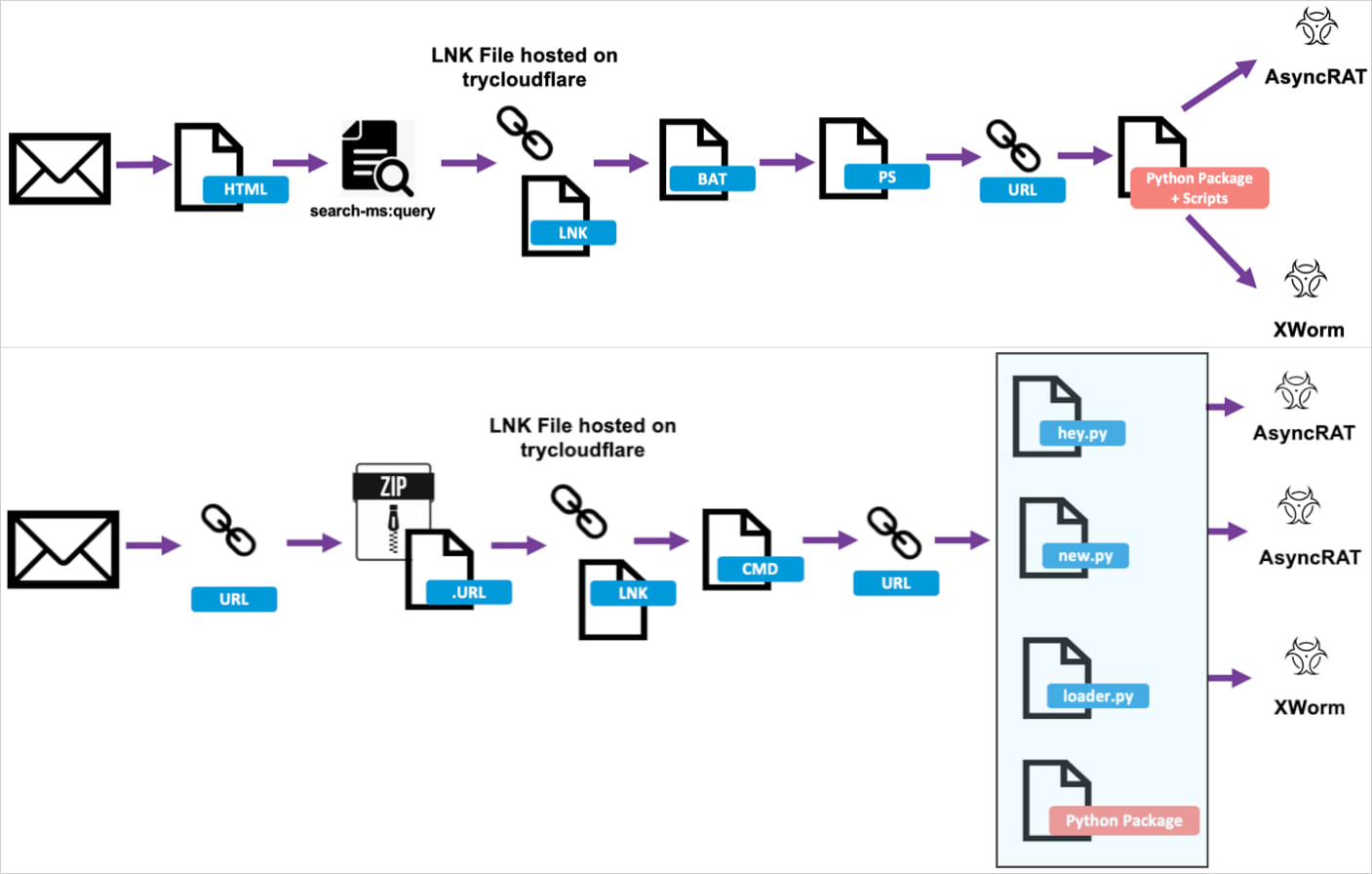 Two attack chains used in the campaign
Two attack chains used in the campaign
Source: Proofpoint
Increased Campaign Activity
Proofpoint noted a significant increase in this campaign’s activity. An email distribution wave that started on July 11 delivered over 1,500 malicious messages, compared to less than 50 messages in an earlier wave from May 28. Hosting LNK files on Cloudflare provides several benefits to the attackers, including making the traffic appear legitimate due to Cloudflare’s reputable service.
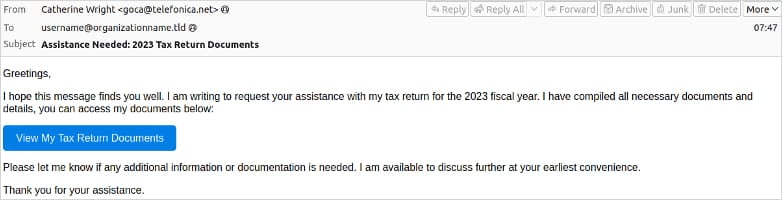 Malicious email sample
Malicious email sample
Source: Proofpoint
Challenges in Blocking Malicious Activity
The temporary nature of the subdomains used in the TryCloudflare Tunnel feature poses a challenge for defenders, as blocking these subdomains is not effective long-term. The free and reliable service also eliminates the need for cybercriminals to set up their own infrastructure, and the use of automation helps them evade blocks from Cloudflare, enabling large-scale operations.
Trending: 10 Misconceptions about Hacking
Trending: Digital Forensics Tool: Horus
Cloudflare’s Response
BleepingComputer reached out to Cloudflare regarding the malicious activity reported by Proofpoint.
A company representative stated:
“Cloudflare immediately disables and takes down malicious tunnels as they are discovered by our team or reported on by third parties. In the past few years, Cloudflare has introduced machine learning detections on our tunnel product in order to better contain malicious activity that may occur. We encourage Proofpoint and other security vendors to submit any suspicious URLs and we will take action against any customers that use our services for malware.”
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













