Cybercriminals Target MS-SQL Servers with Trigona Ransomware

AhnLab, a South Korean cybersecurity firm, has uncovered a Trigona ransomware campaign that targets poorly secured and internet-exposed Microsoft SQL (MS-SQL) servers. The attackers are deploying Trigona ransomware payloads on the servers by brute-forcing or guessing easy-to-guess account credentials.
The Trigona ransomware campaign uses a CLR Shell malware, which is used to harvest system information, alter the compromised account’s configuration, and escalate privileges to LocalSystem by exploiting a vulnerability in the Windows Secondary Logon Service.
Once the ransomware is launched, it encrypts all files on victims’ devices except those in specific folders, including the Windows and Program Files directories. Before encryption, the gang claims to steal sensitive documents that will get added to its dark web leak site.
 Trigona ransom note (BleepingComputer)
Trigona ransom note (BleepingComputer)
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
Trigona Ransomware’s Techniques to Ensure System Encryption and Compromised File Renaming
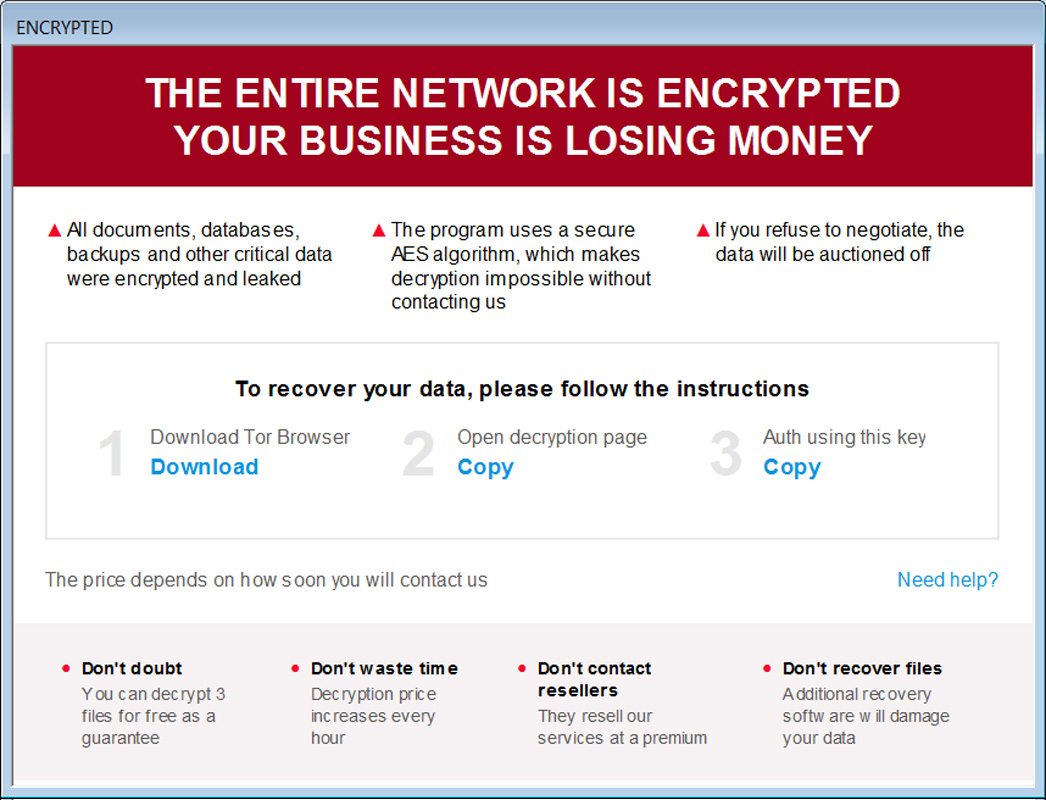
The ransomware renames encrypted files by adding the ._locked extension and creates ransom notes named “how_to_decrypt.hta” in each folder with information about the attack, a link to the Trigona Tor negotiation website, and a link that contains the authorization key needed to log into the negotiation site.
To ensure the systems will be encrypted even after a reboot, the ransomware binary is configured to automatically launch on each system restart via a Windows autorun key. Before encryption, the malware also disables system recovery and deletes any Windows Volume Shadow copies, making recovery impossible without the decryption key.
Trending: Offensive Security Tool: Mythic
Trigona ransomware on the rise
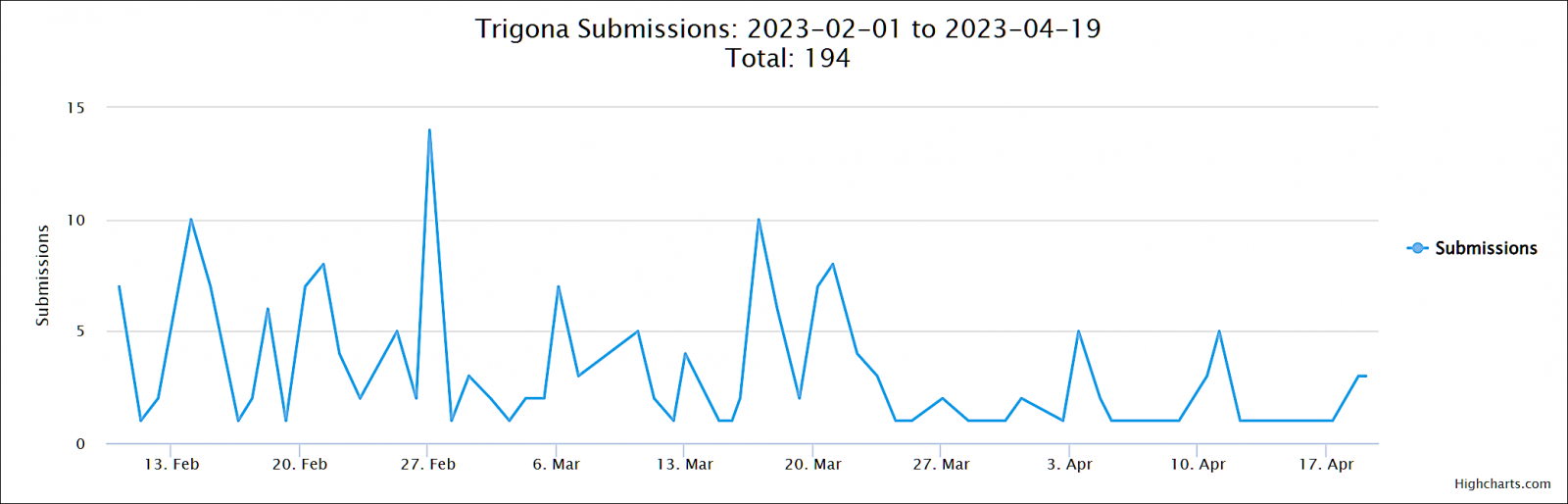
The Trigona ransomware gang has been behind a constant stream of attacks, with at least 190 submissions to the ID Ransomware platform since the start of the year.
 Trigona sample submissions (ID Ransomware)
Trigona sample submissions (ID Ransomware)
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com












