D-Link Responds to Data Breach: Employee Falls Victim to Phishing Attack

D-Link, the prominent Taiwanese networking equipment manufacturer, has confirmed a data breach linked to a recent incident where sensitive information was stolen and subsequently offered for sale on BreachForums.
The attacker claims to have gained access to D-Link’s network, compromising a significant amount of data. The stolen information reportedly includes personal details of both customers and employees, extending to the company’s CEO.
Among the data exposed are names, email addresses, physical addresses, phone numbers, account registration dates, and the last login dates of users. However, a participant in the thread where this data was shared commented on its apparent age, as the provided samples of 45 stolen records had timestamps dating back to 2012 and 2013.
The threat actor behind this breach announced the intrusion: “I have breached the internal network of D-Link in Taiwan, I have 3 million lines of customer information, as well as source code to D-View extracted from the system. This does include the information of MANY government officials in Taiwan, as well as the CEOs and employees of the company.”
The stolen data has been listed for purchase on the hacking forum since October 1st, with the threat actor demanding $500 for both the customer information and the alleged D-View source code.
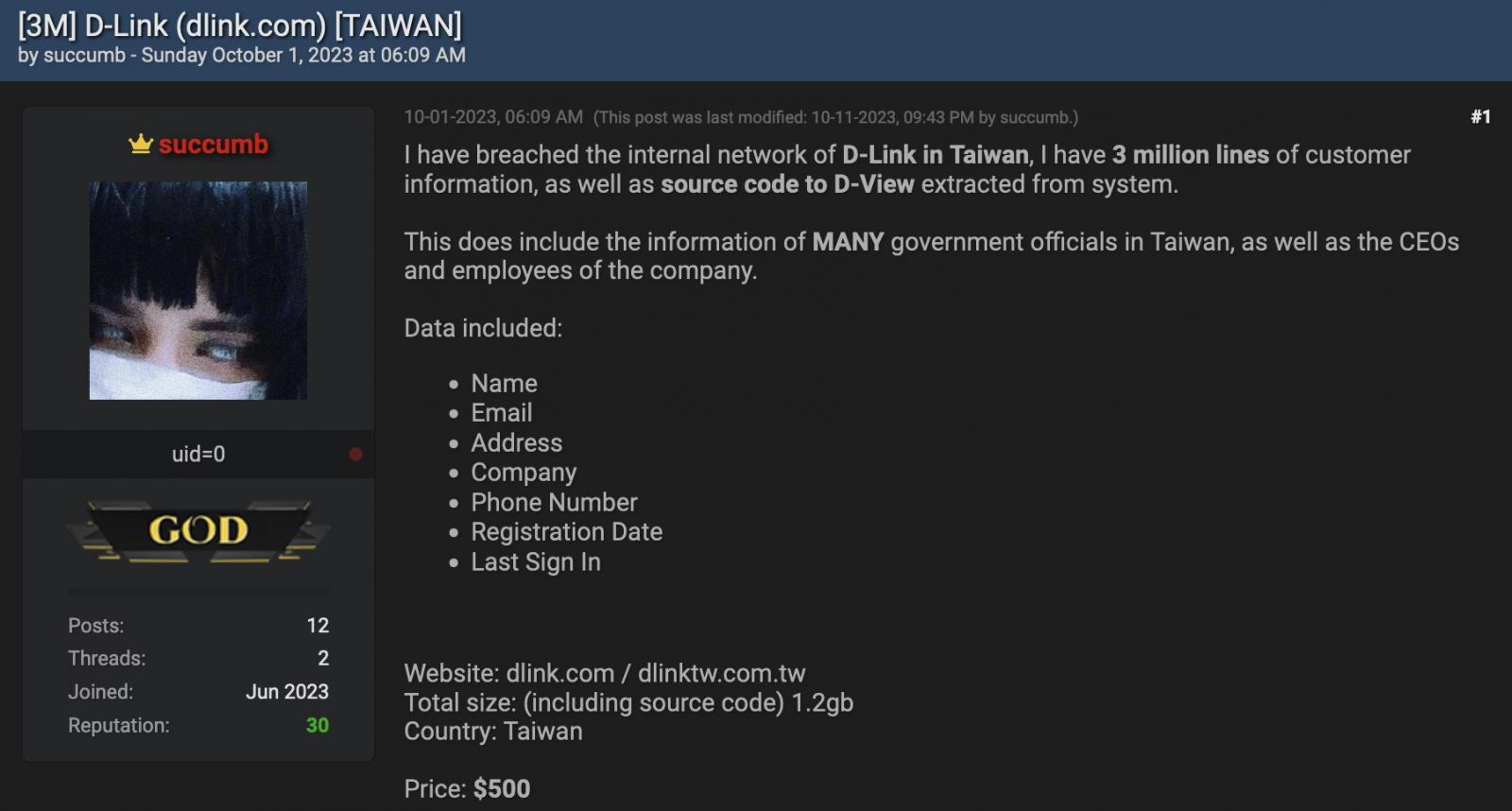 D-Link stolen data up for sale (BleepingComputer)
D-Link stolen data up for sale (BleepingComputer)
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
D-Link promptly responded to the breach by shutting down potentially affected servers and disabling all but two user accounts. The breach, as described by D-Link, occurred due to an employee falling victim to a phishing attack, which provided the attacker with access to the company’s network.
D-Link clarified that the compromised system was part of a “test lab environment” and operated on an outdated D-View 6 system that reached its end of life in 2015. The fact that an end-of-life server remained accessible on D-Link’s network for seven years is still a subject of inquiry.
Trending: Recon Tool: fetchmeurls
In contrast to the threat actor’s claims of stealing millions of users’ data, D-Link revealed that the compromised system contained approximately 700 records, all of which had been inactive for at least seven years. This data originated from a product registration system that had reached the end of its operational life in 2015.
D-Link suspects that the threat actor manipulated recent login timestamps to create the illusion of a more recent data theft. The company also reassured its customers that the majority of its user data consisted of low-sensitivity and semi-public information, thereby minimizing the impact on its customers.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com












