D-Link’s DIR-X4860 Vulnerable to Remote Command Execution with Zero-Day Exploit and Released PoC

See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Exploitation process
The exploitation process involves a series of steps, beginning with a specially crafted HNAP login request to the router’s management interface. By bypassing authentication mechanisms, attackers can gain authenticated access and exploit a command injection vulnerability, ultimately executing arbitrary commands within the router’s operating system.
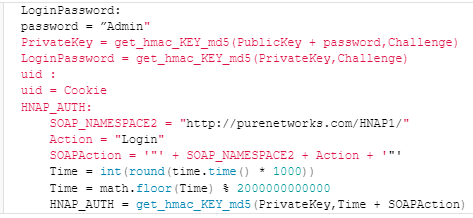 Login request that bypasses the authentication step
Login request that bypasses the authentication step
Source: SSD Secure Disclosure
Efforts to engage D-Link in resolving these security concerns have so far yielded no response. With the release of a security firmware update pending, users are advised to disable the device’s remote access management interface to mitigate the risk of exploitation.
Trending: Offensive Security Tool: 403jump
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













