DDoSia Attack Tool Upgraded with Encryption, Concealed Targeting

New Version of DDoSia Attack Tool Conceals Targets, Indicating Active Maintenance by Operators
The threat actors behind the DDoSia attack tool have released an updated variant that incorporates an additional security mechanism to conceal the list of targets. Developed in Golang, the new version aims to bring down websites through a barrage of junk HTTP requests. This enhancement was discovered by cybersecurity company Sekoia, which detailed the mechanism in a recent technical write-up.
DDoSia, attributed to the pro-Russian hacker group NoName(057)16, emerged in 2022 as the successor to the Bobik botnet. The attack tool specifically targets entities primarily located in Europe, as well as Australia, Canada, and Japan. From May 8 to June 26, 2023, the most affected countries were Lithuania, Ukraine, Poland, Italy, Czechia, Denmark, Latvia, France, the U.K., and Switzerland, with a total of 486 websites impacted.
DDoSia is a cross-platform program, capable of running on Windows, Linux, and macOS systems, with implementations in Python and Go. The tool operates by repeatedly issuing network requests, following instructions from a configuration file received from a command-and-control (C2) server.
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
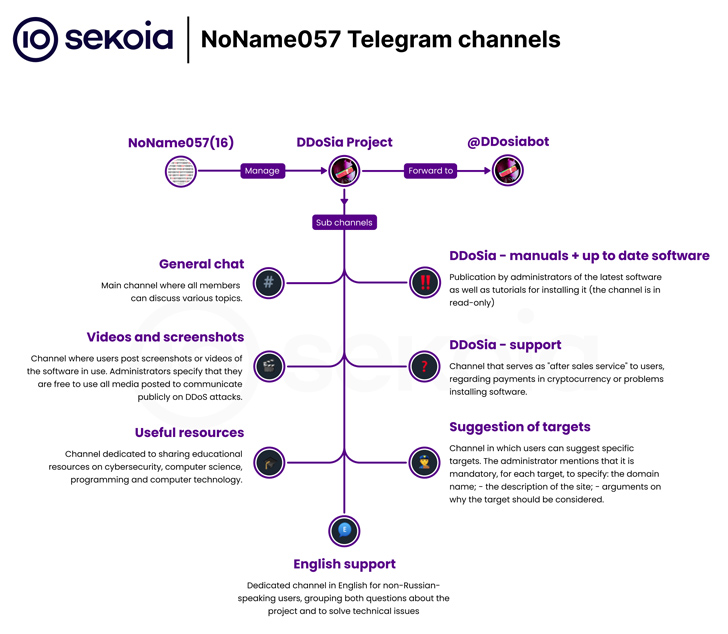
Distribution of DDoSia occurs through an automated process on Telegram, where individuals can register for the crowdsourced initiative. In exchange for a cryptocurrency payment, participants receive a ZIP archive containing the attack toolkit.
The latest version of DDoSia introduces encryption to mask the list of targets, indicating ongoing maintenance and development by the operators. Sekoia highlighted that NoName(057)16 is actively making efforts to expand compatibility with multiple operating systems, suggesting a broader scope of potential victims.
The release of the updated DDoSia tool coincides with a warning from the U.S. Cybersecurity and Infrastructure Security Agency (CISA) regarding targeted denial-of-service (DoS) and DDoS attacks against multiple organizations across various sectors. Such attacks can cause significant disruptions, leading to financial costs and reputational damage.
Trending: Recon Tool: Logsensor
While CISA did not provide specific details about the recent attacks, Anonymous Sudan claimed responsibility for the takedown of websites belonging to the Department of Commerce, Social Security Administration (SSA), and the Treasury Department’s Electronic Federal Tax Payment System (EFTPS) on its Telegram channel. Anonymous Sudan gained attention last month for launching Layer 7 DDoS attacks against Microsoft services, including OneDrive, Outlook, and Azure web portals. The group, claiming to act on behalf of oppressed Muslims, has been linked to the pro-Kremlin KillNet hacktivist collective.
In response to CISA’s advisory, Anonymous Sudan posted a statement on June 30, 2023, asserting its influence by claiming that a small Sudanese group with limited capabilities forced the most powerful government in the world to publish articles and tweets about their attacks.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: thehackernews.com












