Ddostf: MySQL Servers Turned DDoS Battlegrounds

A malware botnet named Ddostf is on the rampage, specifically targeting MySQL servers to harness them as part of a DDoS-as-a-Service platform available for rent by cybercriminals.
Unearthed by researchers at the AhnLab Security Emergency Response Center (ASEC), this campaign exposes the dark underbelly of cyber threats that exploit vulnerabilities in MySQL environments or exploit weak administrator credentials through brute force attacks.
Ddostf’s operators are strategically scanning the internet for susceptible MySQL servers, using a dual approach of exploiting vulnerabilities in unpatched systems and aggressively attempting to crack weak administrator account passwords. For Windows-based MySQL servers, the threat actors employ a technique known as User-Defined Functions (UDFs) to execute commands on the compromised systems.
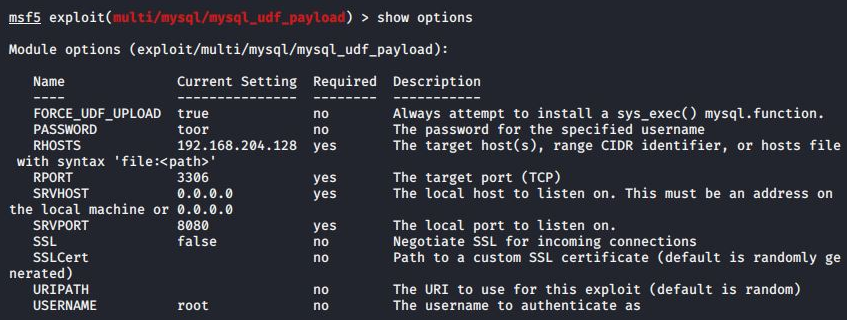 Metasploit module for abusing UDF (ASEC)
Metasploit module for abusing UDF (ASEC)
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
User-Defined Functions (UDFs) are a MySQL feature allowing users to define functions in C or C++ and compile them into a DLL (Dynamic Link Library) file, extending the capabilities of the database server. In this attack, the adversaries create their own malicious UDFs, registering them as a DLL file (amd.dll), enabling functions such as downloading payloads, executing system-level commands, and sending results of command execution back to the attackers.
This abuse of UDFs not only facilitates the deployment of the primary payload, the Ddostf bot client, but also opens the door for potential installation of other malware, data exfiltration, and the creation of backdoors for persistent access.
Ddostf Origins
Ddostf, a Chinese-origin malware botnet that has been active for approximately seven years, is not limited to a specific operating system, targeting both Linux and Windows systems. On Windows, it establishes persistence by registering itself as a system service, decrypting its command and control (C2) configuration to establish a connection.
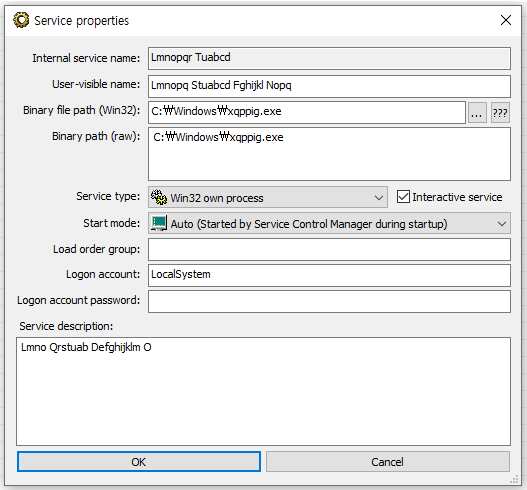 Ddostf’s system service (ASEC)
Ddostf’s system service (ASEC)
Trending: Jeff Foley – OWASP Amass Founder
Trending: Offensive Security Tool: Ghauri
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













