DISGOMOJI: New Linux Malware Uses Emojis for Command Execution

See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Unique C2 Mechanism: Discord and Emojis
The malware was discovered when Volexity researchers found a UPX-packed ELF executable in a ZIP archive, likely distributed via phishing emails. The malware appears to target a custom Linux distribution called BOSS, used by Indian government agencies as their desktop OS, though it can also infect other Linux distributions.
Upon execution, the malware downloads and displays a PDF lure—a beneficiary form from India’s Defence Service Officer Provident Fund. Concurrently, it downloads additional payloads, including DISGOMOJI and a shell script named ‘uevent_seqnum.sh,’ which searches for USB drives and steals data from them.
Once launched, DISGOMOJI exfiltrates system information, including IP address, username, hostname, operating system, and current working directory, sending this data back to the attackers. The threat actors control the malware using the open-source project discord-c2, which leverages Discord and emojis for communication and command execution.
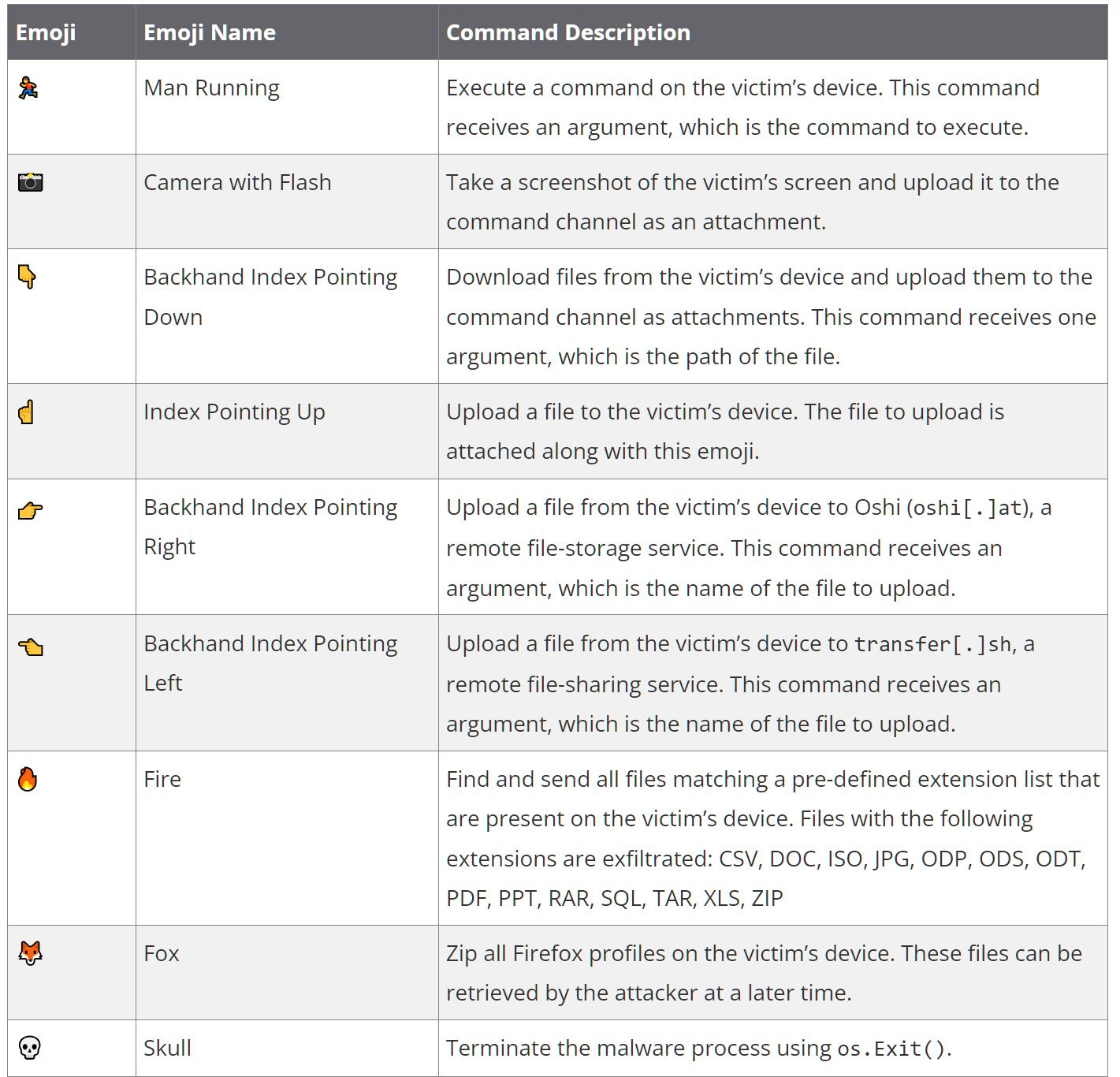
DISGOMOJI connects to an attacker-controlled Discord server and awaits emoji-based commands. “DISGOMOJI listens for new messages in the command channel on the Discord server,” Volexity explains. “C2 communication uses an emoji-based protocol where the attacker sends commands via emojis, with additional parameters as needed. While processing a command, the malware reacts with a ‘Clock’ emoji to indicate progress and a ‘Check Mark Button’ emoji upon completion.”
The malware uses nine different emojis to represent various commands for execution on the infected device.
Trending: Offensive Security Tool: SecretOpt1c
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: www.bleepingcomputer.com













