‘EvilVideo’ Zero-Day Exploit Hits Telegram: Malicious APKs Disguised as Video Files

A zero-day vulnerability in Telegram for Android, dubbed ‘EvilVideo,’ has been discovered, allowing attackers to send malicious Android APK payloads disguised as video files. This flaw, which affected Telegram version 10.14.4 and older, was first sold by a threat actor named ‘Ancryno’ on the XSS hacking forum on June 6, 2024.
The exploit was uncovered by ESET researchers after a proof-of-concept demonstration was shared on a public Telegram channel. ESET confirmed the vulnerability and named it ‘EvilVideo.’ Researcher Lukas Stefanko responsibly disclosed the flaw to Telegram on June 26 and again on July 4, 2024.
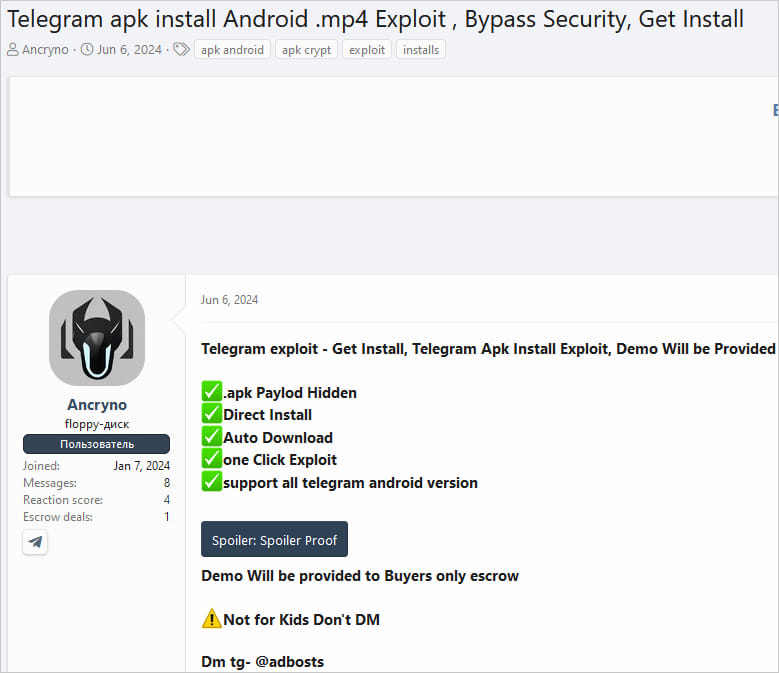 Threat actor selling the exploit on a hacking forum
Threat actor selling the exploit on a hacking forum
Source: ESET
Telegram acknowledged the report on July 4 and released a patch in version 10.14.5 on July 11, 2024. This timeline indicates that threat actors had at least five weeks to exploit the vulnerability before it was patched.
While it remains unclear if the flaw was actively used in attacks, ESET identified a command and control server used by the malicious payloads at ‘infinityhackscharan.ddns[.]net.’ BleepingComputer found two malicious APK files using that server on VirusTotal, masquerading as Avast Antivirus and an ‘xHamster Premium Mod.’
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Mechanism of the ‘EvilVideo’ Exploit
The ‘EvilVideo’ exploit specifically targeted Telegram for Android, allowing attackers to send specially crafted APK files that appeared as embedded videos. ESET believes the exploit leveraged the Telegram API to create messages displaying a 30-second video.
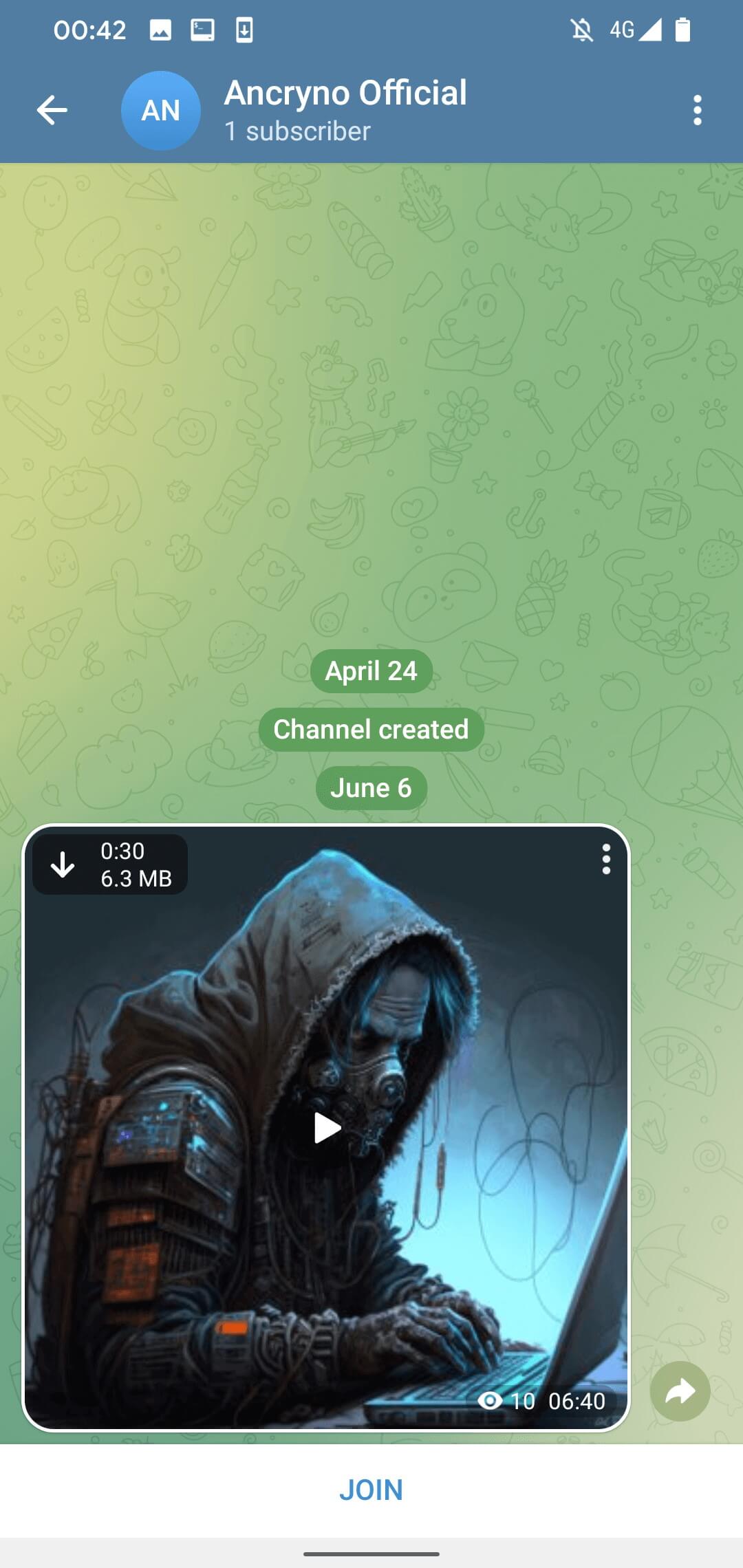 APK file previewed as a 30-sec clip
APK file previewed as a 30-sec clip
Source: ESET
With the default settings, Telegram on Android automatically downloads media files, delivering the payload once the conversation is opened. For users with auto-download disabled, tapping the video preview initiates the file download.
Steps to Execute the Malicious Payload
Upon attempting to play the fake video, Telegram suggests using an external player, potentially leading recipients to tap “Open” and execute the payload. However, to install the malicious APK, victims must enable the installation of unknown apps from their device settings.
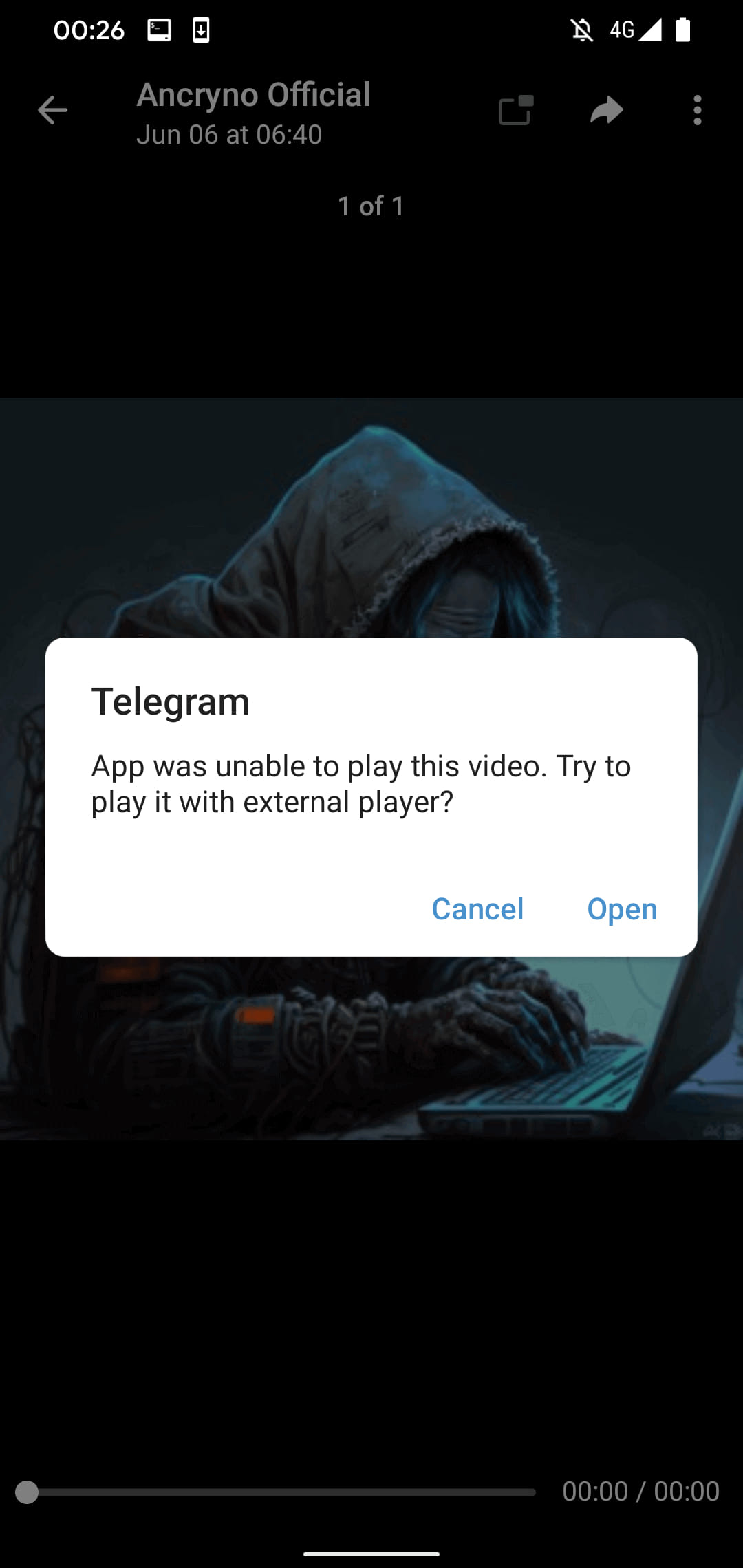 Prompt to launch an external video player
Prompt to launch an external video player
Source: ESET
Trending: Deep Dive to Fuzzing for Maximum Impact
Trending: Recon Tool: FinalRecon
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













