Exploitable Weaknesses Found in Popular POST SMTP Mailer Plugin Affecting 300,000 WordPress Sites

In a recent discovery, security researchers Ulysses Saicha and Sean Murphy from Wordfence identified two critical vulnerabilities in the widely-used POST SMTP Mailer WordPress plugin, an email delivery tool employed by approximately 300,000 websites. These vulnerabilities pose a significant threat, potentially allowing attackers to gain complete control over site authentication.
The first vulnerability, tracked as CVE-2023-6875, is a critical authorization bypass flaw resulting from a “type juggling” issue on the connect-app REST endpoint. This flaw affects all versions of the plugin up to version 2.8.7. Exploiting this flaw, an unauthenticated attacker can reset the API key and access sensitive log information, including password reset emails. By manipulating a function related to the mobile app, the attacker can set a valid token with a zero value for the authentication key, triggering a password reset for the site’s admin.
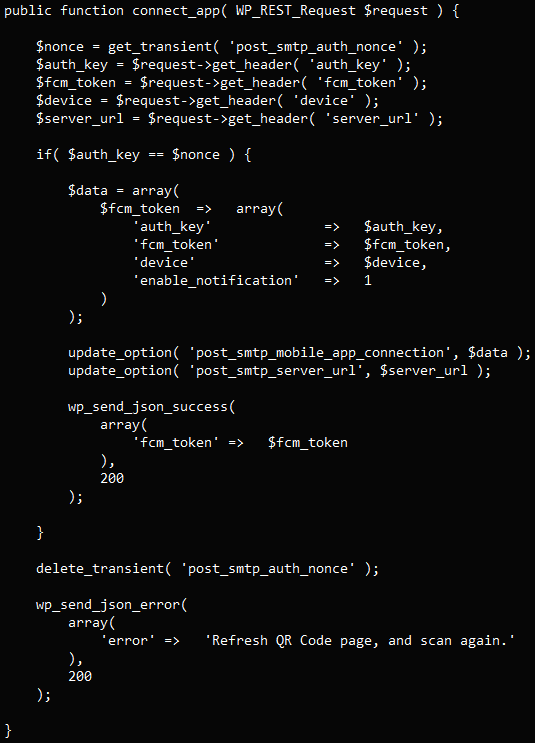 Vulnerable code handling the API request (Wordfence)
Vulnerable code handling the API request (Wordfence)
Subsequently, the attacker gains access to the key within the application, altering it and effectively locking the legitimate user out of their account.
With administrator privileges, the attacker can then execute actions like planting backdoors, modifying plugins and themes, and redirecting users to malicious destinations.
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
The second vulnerability, identified as CVE-2023-7027, is a cross-site scripting (XSS) issue stemming from insufficient input sanitization and output escaping. This flaw, affecting versions of POST SMTP up to 2.8.7, allows attackers to inject arbitrary scripts into the web pages of the affected site.
Wordfence promptly reported these critical flaws to the plugin’s vendor on December 8, 2023. Following the submission, they provided a proof-of-concept (PoC) exploit on December 15 for the authorization bypass flaw, and the XSS issue was reported on December 19, 2023, with a PoC shared the next day.
Trending: Offensive Security Tool: SessionProbe
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













