Explosion of New Variants Triggered by LockBit 3.0 Ransomware Builder Leak
The aftermath of last year’s LockBit 3.0 ransomware builder leak has triggered a cascade of threat actors exploiting the tool to generate an array of new ransomware variants.
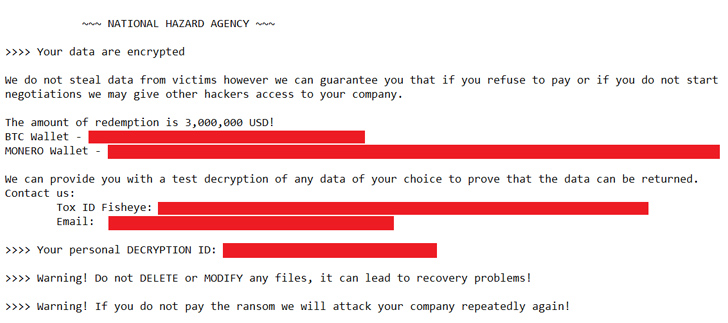
Kaspersky, a prominent Russian cybersecurity firm, recently reported the discovery of a ransomware breach involving a version of LockBit with a distinctive ransom demand procedure. Unlike the LockBit group, which uses its own communication and negotiation platform and omits the ransom amount, this attacker utilized a different ransom note. This note, associated with a previously unknown group called “NATIONAL HAZARD AGENCY,” explicitly specified the demanded payment for decryption keys and provided communication instructions via a Tox service and email.
This occurrence underlines the extent of the transformation following the leak. The LockBit 3.0 builder, now in the hands of various cybercrime gangs, has given rise to diverse iterations, including Bl00dy and Buhti, showcasing the adaptability and evolution of ransomware strategies.
In a further revelation, Kaspersky disclosed identifying a total of 396 unique LockBit samples in its telemetry, with 312 of these being fashioned using the leaked builder. Strikingly, 77 samples did not contain any mention of “LockBit” in their ransom notes. The research suggests that while many of these samples retained default builder configurations, some exhibited minor alterations, indicating rapid development possibly driven by urgent requirements.
Simultaneously, cybersecurity company Netenrich delved into the ongoing evolution of ADHUBLLKA, a rebranded ransomware strain with various iterations (BIT, LOLKEK, OBZ, U2K, and TZW) since 2019. These iterations, characterized by subtle changes in encryption techniques, ransom notes, and communication methods, were linked to ADHUBLLKA due to common source code and infrastructure elements.
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
Rakesh Krishnan, a security researcher, highlighted a common practice among cybercriminals to reuse successful ransomware samples and slightly modify their codebases to launch new projects. This adaptive approach enables them to modify encryption schemes, ransom notes, and communication channels, effectively rebranding themselves as “new” ransomware entities.
As the ransomware landscape continues to evolve, it has increasingly targeted Linux environments. Families such as Trigona, Monti, and Akira, which is linked to Conti-affiliated threat actors, demonstrate a growing focus on Linux systems.
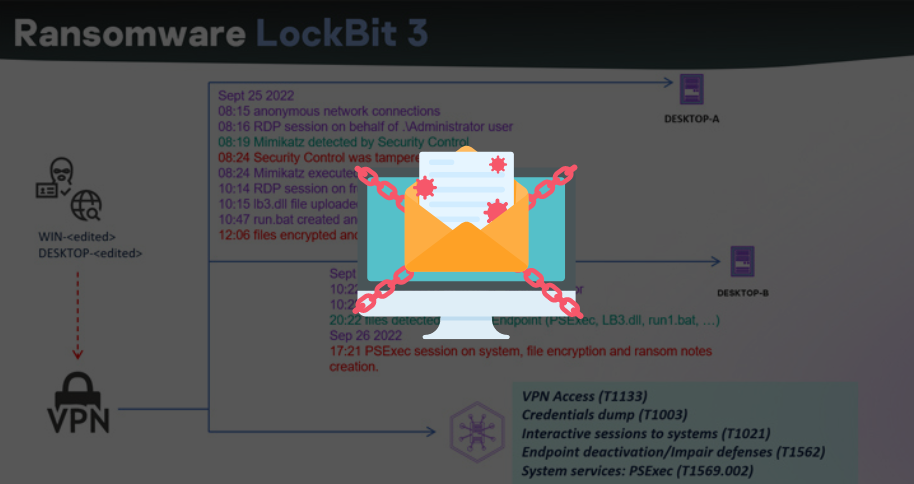
Additionally, the Akira ransomware has been involved in attacks leveraging Cisco VPN products as an attack vector. This approach aims to gain unauthorized access to enterprise networks by exploiting the absence of multi-factor authentication (MFA) or known vulnerabilities in VPN software. Following unauthorized access, attackers seek to extract credentials through LSASS (Local Security Authority Subsystem Service) dumps, facilitating further network exploration and privilege escalation.
The surge in ransomware attacks continues, with Cl0p ransomware breaching over 1,000 organizations through flaws in the MOVEit Transfer app, initiating network encryption. The majority of corporate victims were based in the U.S., followed by Germany, Canada, and the U.K. The mass-exploitation campaign, which began in May 2023, has affected more than 60 million individuals.
Trending: Offensive Security Tool: BruteSpray
The financial implications of these attacks are substantial, with estimates suggesting that threat actors could amass illicit profits ranging from $75 million to $100 million. While the MOVEit campaign may affect numerous companies directly and indirectly, only a small percentage of victims negotiated or considered paying. Those who chose to pay incurred substantially higher costs compared to previous campaigns.
According to the Sophos 2023 Active Adversary Report, the median dwell time for ransomware incidents decreased from nine days in 2022 to five days in the first half of 2023, indicating the increasing speed of ransomware operations. In contrast, non-ransomware incidents witnessed an extended dwell time, rising from 11 to 13 days. Notably, a significant portion of ransomware attacks occurred outside traditional working hours, with the majority detected on Fridays and Saturdays, underscoring the opportunistic nature of these cybercriminal operations
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: thehackernews.com












