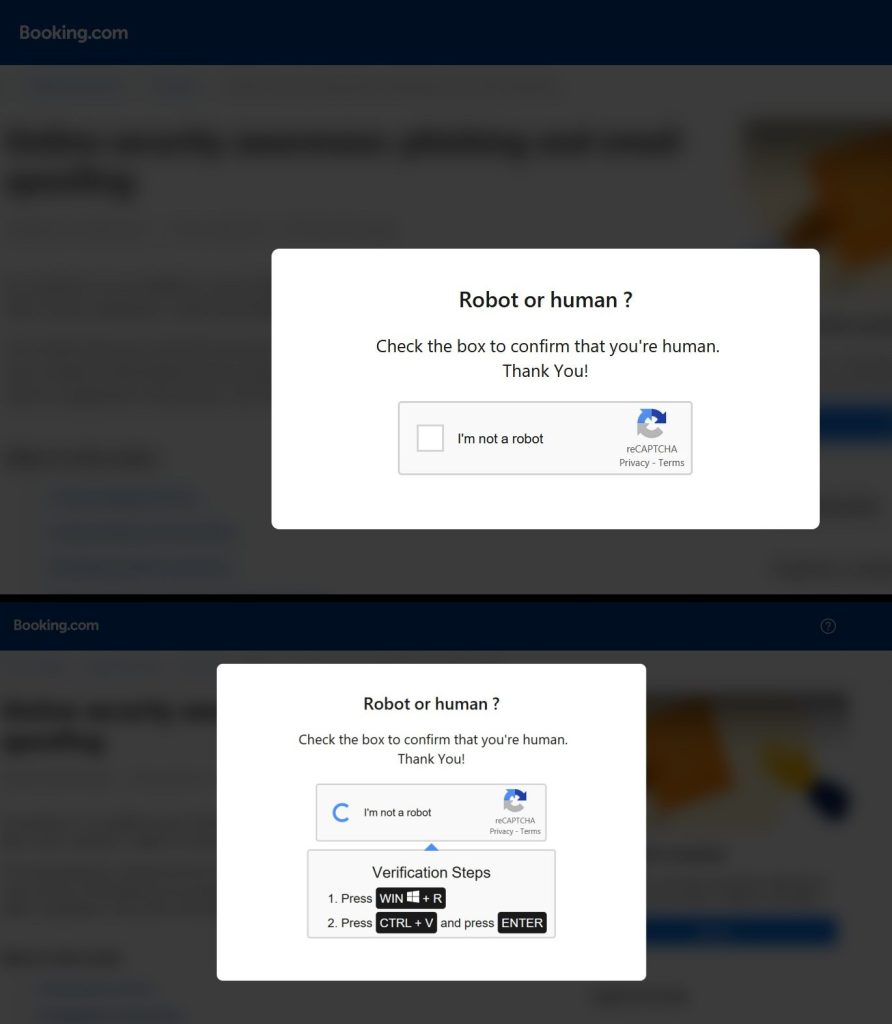
Fake Booking.com Emails Trick Hotel Staff into Installing AsyncRAT via Fake CAPTCHA

See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
The Malware: AsyncRAT, a Persistent and Evasive Trojan
At the heart of the scam is AsyncRAT, a widely used remote access trojan known for its stealth and flexibility. Active since 2019, it allows cybercriminals to:
Log keystrokes
Access files and steal data
Control desktops remotely
Install additional malware
Maintain long-term access to compromised devices
AsyncRAT is often deployed using trusted Windows processes like MSBuild.exe, making it difficult for some antivirus software to detect. Once installed, it hides in the %AppData% directory and communicates with a command-and-control server over a custom port.
Growing Threat from a Proven Actor
AsyncRAT has been observed in several high-profile campaigns. Microsoft flagged its use against aerospace and travel companies in 2021. By 2023, variants like DcRAT were spreading through fake adult content links. More recently, the malware was embedded in malicious image files and used to target U.S. infrastructure in early 2024.
Its consistent evolution and open-source nature make AsyncRAT a weapon of choice for cybercriminals seeking persistence and stealth.
Trending: Recon Tool: RADAR
Why This Campaign Is Especially Dangerous
Unlike common phishing scams that aim to steal passwords or login credentials, this attack takes a more insidious route: tricking users into installing the malware themselves. By guiding the victim through manual command execution, the attackers bypass traditional download filters and endpoint security mechanisms.
Successful infections could expose sensitive guest information, financial data, and internal hotel operations to external actors.
Security Advice for the Hospitality Industry
Hotel staff and IT teams are advised to remain vigilant and adopt the following best practices:
Do not click links in unsolicited emails, even if they appear official.
Never execute commands from unknown emails or websites, especially those instructing use of the Run dialog.
Verify URLs carefully — legitimate Booking.com links do not contain unfamiliar subdomains like
partlet-id739847.Report suspicious messages directly to Booking.com via official partner support channels.
Educate employees about phishing tactics and simulate awareness training regularly.
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: hackread.com