Fake Google Chrome and Microsoft Word Alerts Spread Malware via PowerShell Commands

See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
PowerShell “Fix” Leads to Malware Infections
Proofpoint analysts identified three distinct attack chains, each varying slightly in their initial stages. However, the subsequent stages consistently lead to malware infections. The payloads delivered through these attacks include DarkGate, Matanbuchus, NetSupport, Amadey Loader, XMRig, a clipboard hijacker, and Lumma Stealer.
In the first attack chain, linked to ClearFake, users visiting compromised websites encounter a fake Google Chrome warning about a webpage display issue. The warning instructs users to copy a PowerShell script to install a “root certificate” and run it with administrative privileges.
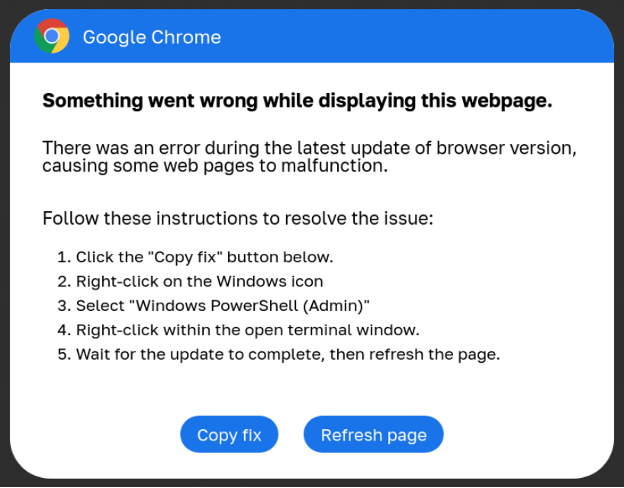 Fake Google Chrome error
Fake Google Chrome error
Source: Proofpoint
Executing this script triggers a series of actions:
- Flushing the DNS cache.
- Removing clipboard content.
- Displaying a decoy message.
- Downloading and executing additional payloads after performing anti-VM checks.
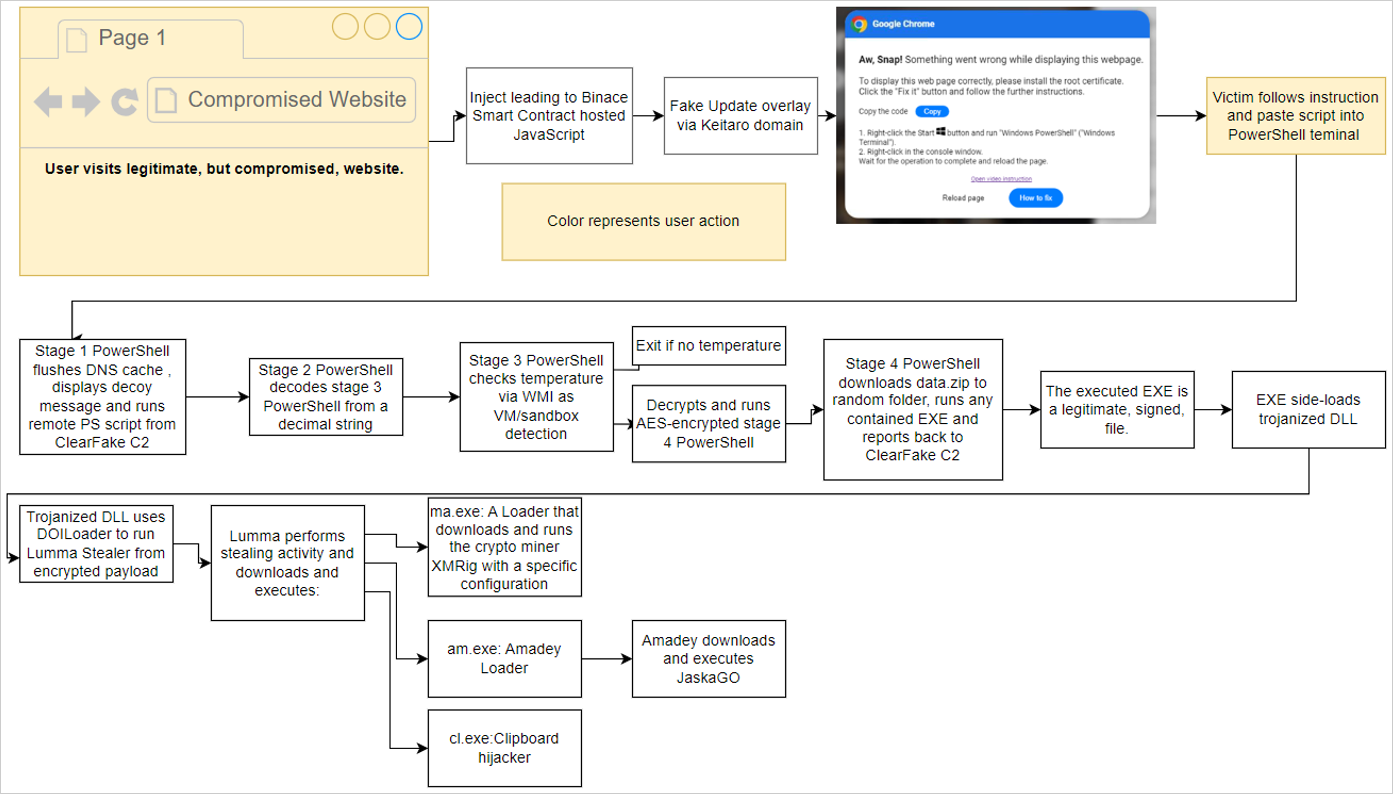 The ‘ClearFake’ attack chain
The ‘ClearFake’ attack chain
Source: Proofpoint
The second attack chain, attributed to the ClickFix campaign, involves injecting an iframe into compromised websites to display another fake Google Chrome error. Similar to the first chain, users are directed to run a PowerShell script, leading to the same malware infections.
The third attack chain utilizes email-based tactics, where HTML attachments resembling Microsoft Word documents prompt users to install the “Word Online” extension. The error message provides “How to fix” and “Auto-fix” options, both leading to the execution of malicious PowerShell commands or the download of harmful files.
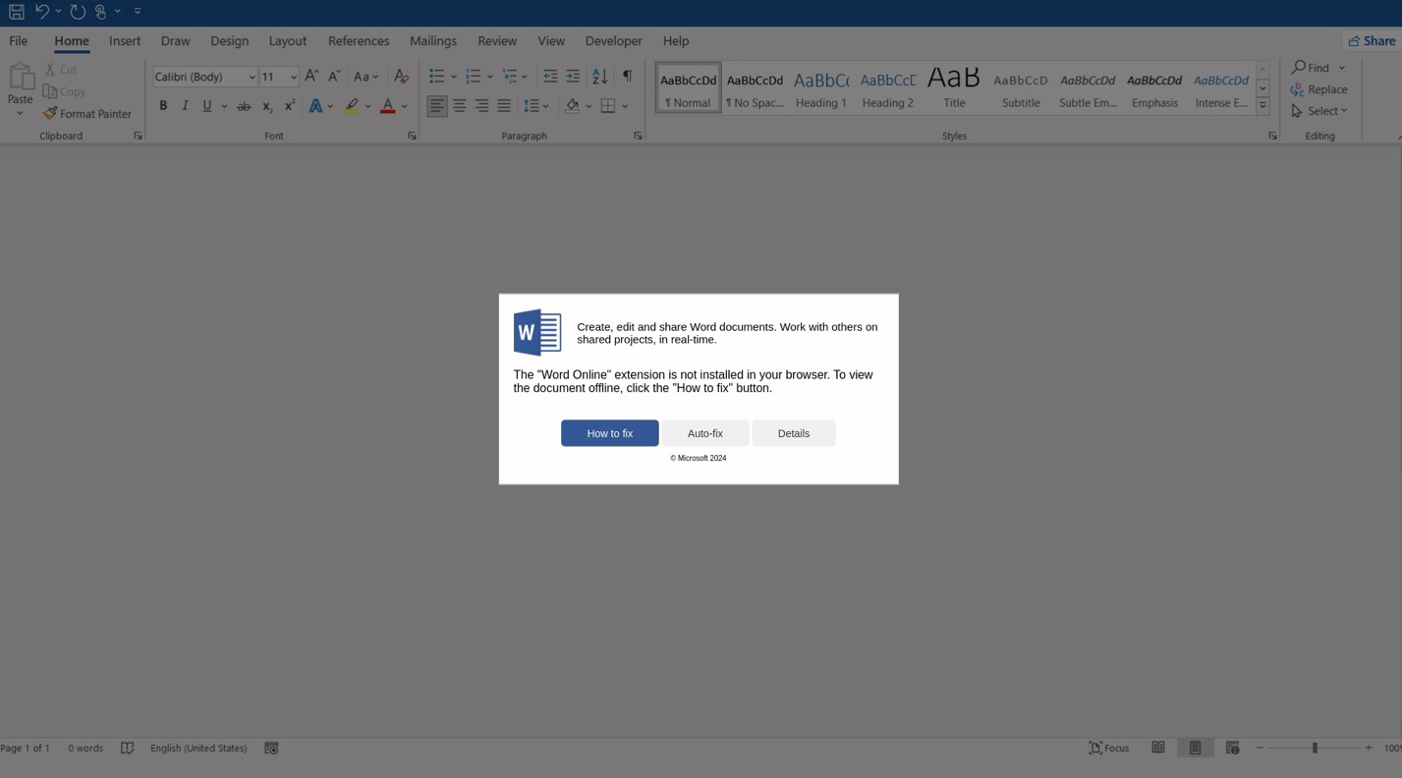 Fake Microsoft Word error leads to malware
Fake Microsoft Word error leads to malware
Source: Proofpoint
Trending: Offensive Security Tool: SecretOpt1c
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













