Fake PoC Exploit Targets Cybersecurity Researchers with Linux Malware

In a recent development, cybersecurity researchers and threat actors have become targets of a fake proof of concept (PoC) exploit, known as CVE-2023-35829, which installs a Linux password-stealing malware. This malicious PoC was discovered by Uptycs analysts during routine scans when anomalies such as unauthorized system access attempts, unexpected network connections, and unusual data transfers were flagged by detection systems.
The malicious PoC exploit was found in three repositories, with two already removed from GitHub while one still remains active. Uptycs reports that this fake PoC has been widely shared among members of the security research community, suggesting that numerous computers might have already been infected.
 A malicious GitHub repository pushing the malware (BleepingComputer)
A malicious GitHub repository pushing the malware (BleepingComputer)
PoC Details
The deceptive PoC claims to be an exploit for CVE-2023-35829, a high-severity use-after-free vulnerability affecting the Linux kernel before version 6.3.2. However, upon closer inspection, it is revealed that the PoC is actually a copy of an old legitimate exploit targeting another Linux kernel vulnerability, CVE-2022-34918.
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
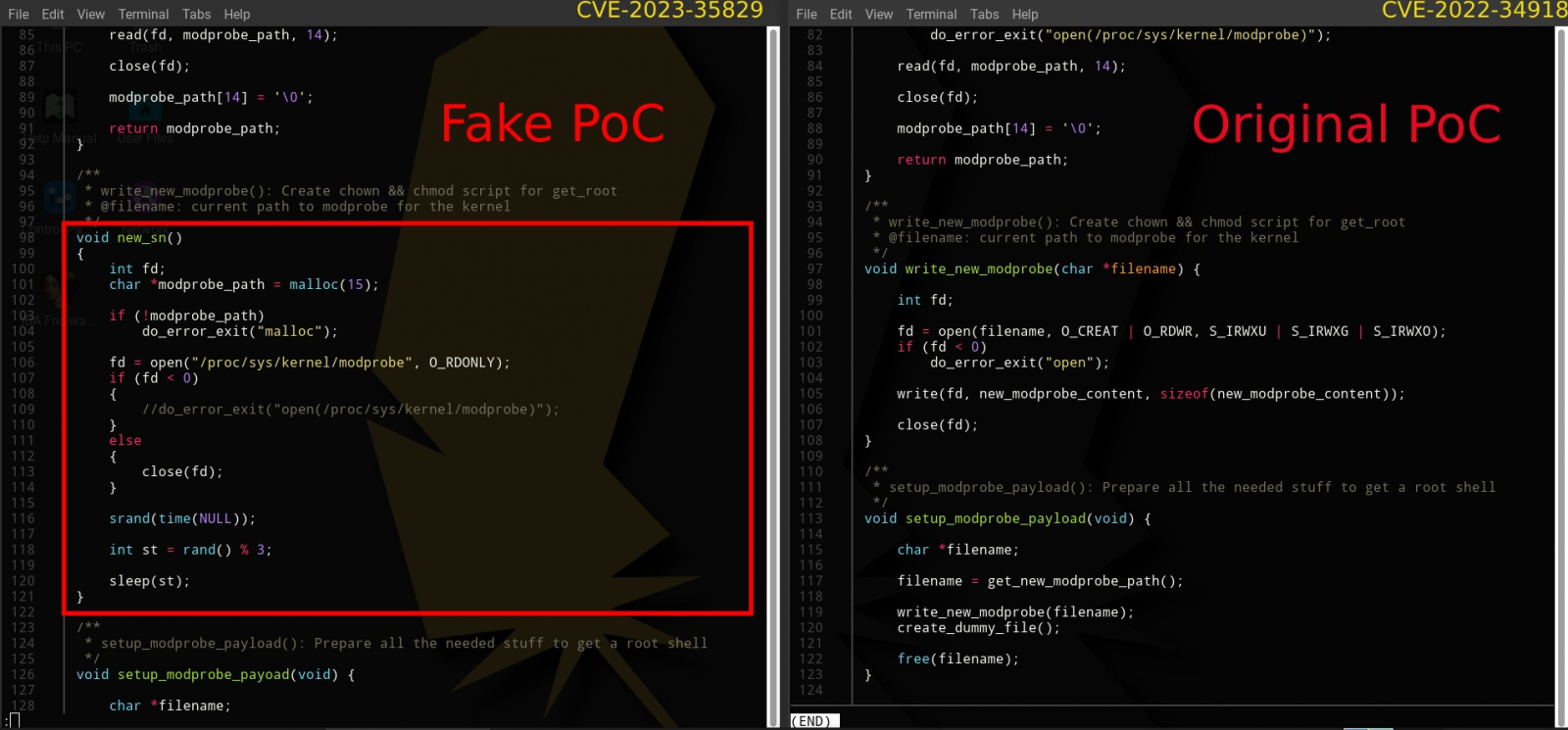 Code comparison between the two PoCs (Uptycs)
Code comparison between the two PoCs (Uptycs)
The malicious code takes advantage of Linux namespaces, a feature that partitions kernel resources, to create the illusion of a root shell while operating within the limitations of the user namespace. This tactic aims to deceive victims into believing that the exploit is genuine and functioning as expected, granting the attackers more time to freely navigate the compromised system.
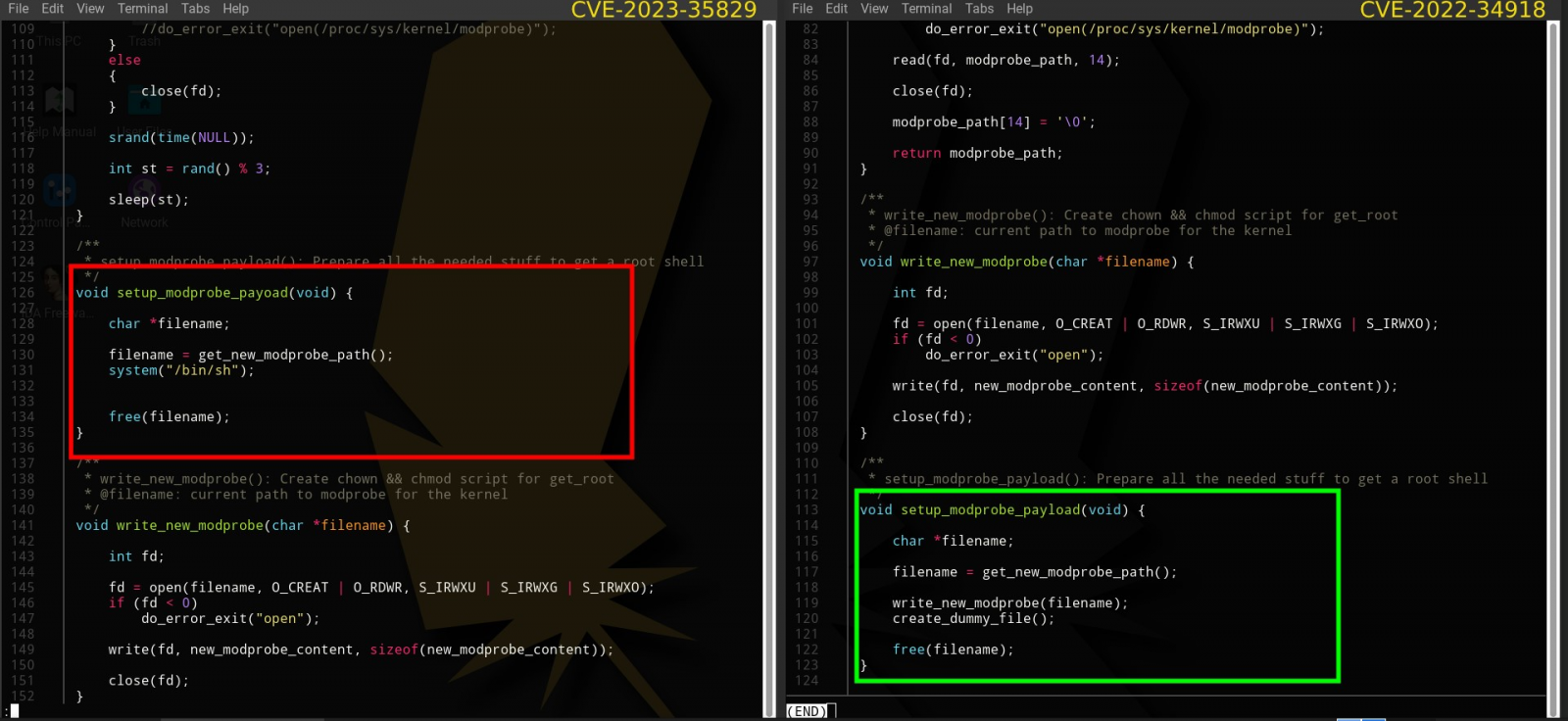 Code part for creating a fake shell (Uptycs)
Code part for creating a fake shell (Uptycs)
Upon execution, the PoC creates a ‘kworker’ file and adds its path to the ‘/etc/bashrc’ file for persistence. It then establishes communication with the attacker’s command-and-control (C2) server to download and execute a Linux bash script from an external URL. This downloaded script gains unauthorized access to the system by modifying the ‘/etc/passwd’ file, granting the attacker remote access through unauthorized modifications to the ‘~/.ssh/authorized_keys’ file. The stolen data includes the victim’s username, hostname, and contents of their home directory, which are exfiltrated using ‘transfer.sh’ via the curl command.
To evade detection, the bash script camouflages its operations as kernel-level processes, leveraging the trust placed in such entries by system administrators. This allows the attackers to navigate the compromised system undetected.
Uptycs advises researchers who have downloaded and utilized the fake PoC to take specific actions, including removing any unauthorized SSH keys, deleting the ‘kworker’ file, eliminating the ‘kworker’ path from the bashrc file, and checking ‘/tmp/.iCE-unix.pid’ for potential threats.
Trending: Recon Tool: Logsensor
Extra caution when using downloaded PoCs
It is essential for researchers to exercise caution when using PoCs downloaded from the internet, preferably testing them in isolated environments like virtual machines and inspecting the code before execution. Additionally, submitting binaries to platforms like VirusTotal can quickly identify potential malicious files.
This incident involving fake PoCs targeting researchers and threat actors with malware is not an isolated occurrence. In a similar vein, last month, VulnCheck analysts uncovered a campaign in which threat actors impersonated trusted cybersecurity researchers to distribute malware disguised as zero-day exploits for popular applications such as Chrome, MS Exchange, and Discord. Moreover, a technical paper published by university researchers in October 2022 shed light on the alarming fact that up to 10.3% of PoCs hosted on GitHub could potentially be malware. Additionally, the North Korean Lazarus hackers were implicated in a 2021 campaign that employed social media to target vulnerability researchers with fake PoCs, ultimately installing backdoors on their systems.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com












