Ficora and Capsaicin Botnets Exploit Outdated D-Link Routers in Global DDoS Surge

Two botnets, Ficora and Capsaicin, are escalating their attacks on D-Link routers that are either outdated or have reached their end of life.
Targets and Vulnerabilities
The attacks focus on widely used devices like the DIR-645, DIR-806, GO-RT-AC750, and DIR-845L. Both botnets exploit known vulnerabilities, specifically:
- CVE-2015-2051: A remote code execution flaw in D-Link’s management interface
- CVE-2019-10891: Firmware authentication bypass
- CVE-2022-37056: Improper access controls in D-Link routers
- CVE-2024-33112: A newly identified flaw allowing remote command execution
After gaining initial access, attackers exploit weaknesses in D-Link’s management interface (HNAP) by executing malicious commands through a GetDeviceSettings action.
Attack Capabilities
Compromised devices can:
- Steal data
- Execute shell scripts
- Participate in distributed denial-of-service (DDoS) attack
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Ficora Botnet
Ficora is a modernized variant of the Mirai botnet, designed specifically to exploit flaws in D-Link routers. According to Fortinet telemetry, Ficora shows random targeting but has had notable surges in activity in October and November 2024, particularly in Japan and the United States.
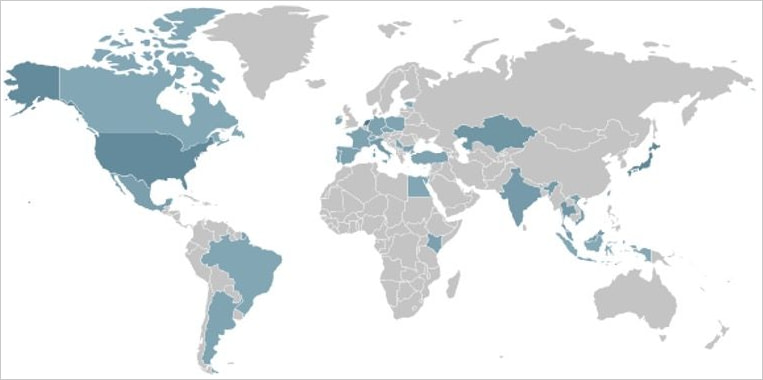 Location of devices infected by Ficora
Location of devices infected by Ficora
Source: Fortinet
Key Characteristics:
- Payload Delivery: Deploys a shell script named
multito download and execute malware via multiple methods (wget,curl,ftpget, andtftp). - Brute Force Functionality: Employs hard-coded credentials to infect other Linux-based devices.
- DDoS Capabilities: Implements UDP flooding, TCP flooding, and DNS amplification, maximizing the impact of its attacks.
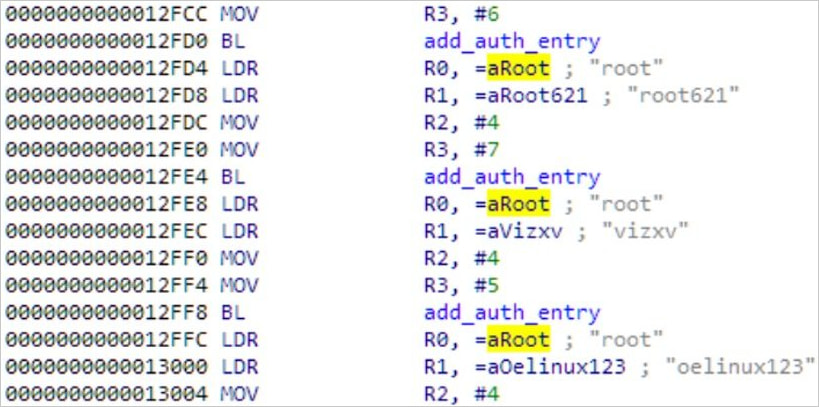 Ficora’s brute-forcing function
Ficora’s brute-forcing function
Source: Fortinet
Capsaicin Botnet
Capsaicin, a variant of the Kaiten botnet, is believed to originate from the Keksec group, known for malware like EnemyBot. While its activity spiked briefly between October 21-22, it primarily targeted East Asian devices.
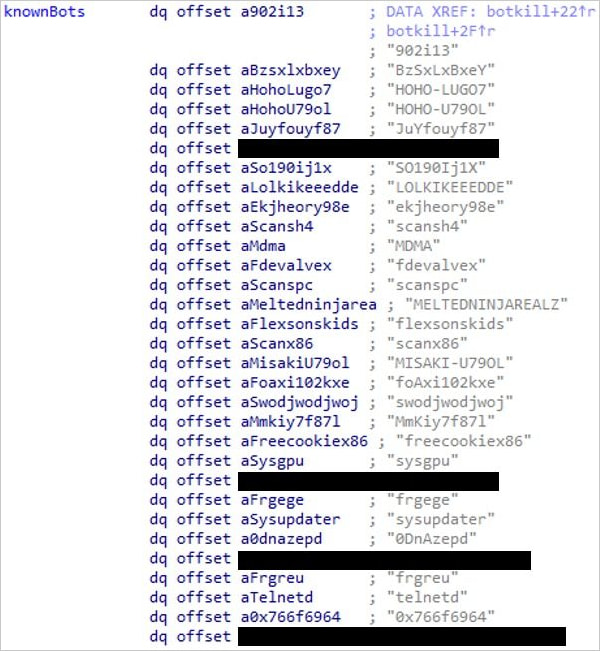 Names of other botnet malware Capsaicin disables
Names of other botnet malware Capsaicin disables
Source: Fortinet
Key Characteristics:
- Infection Mechanism: Uses a downloader script (
bins.sh) to fetch binaries prefixed with ‘yakuza’ for multiple architectures (e.g., arm, mips, sparc, x86). - Botnet Neutralization: Actively disables other botnet payloads present on infected devices.
- DDoS Capabilities: Similar to Ficora, Capsaicin supports UDP and TCP floods while also gathering host information for exfiltration to its command-and-control (C2) server.
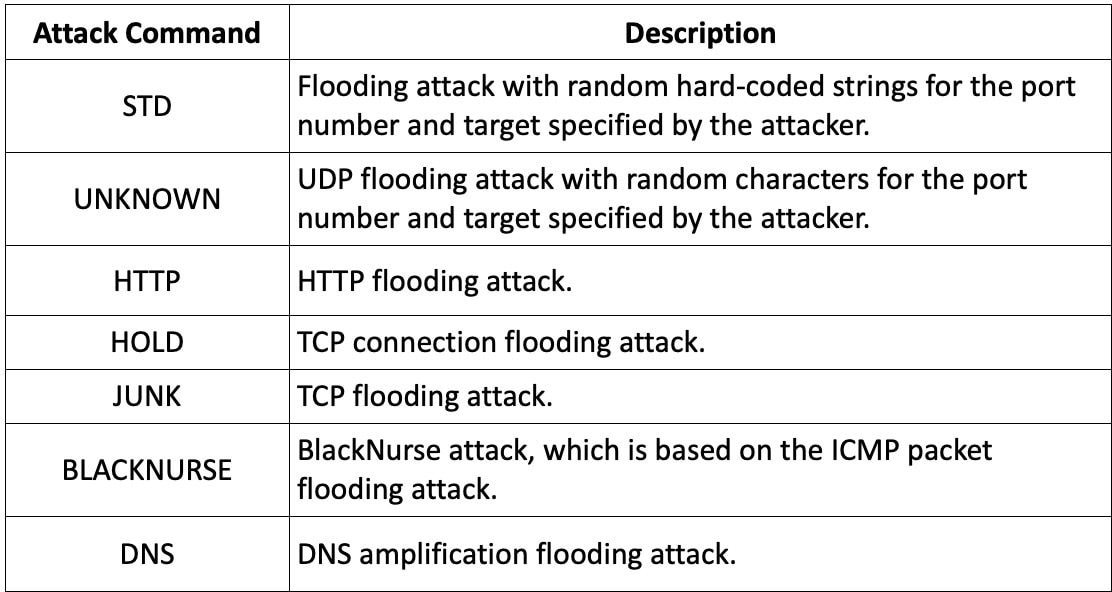 Capsaicin DDoS commands
Capsaicin DDoS commands
Source: Fortinet
Mitigation and Prevention Tips
To protect against threats like Ficora and Capsaicin, users and organizations should:
- Update Firmware: Ensure all devices run the latest firmware to patch known vulnerabilities.
- Replace End-of-Life Devices: Upgrade routers that no longer receive security updates.
- Secure Configurations:
- Replace default admin credentials with strong, unique passwords.
- Disable remote access interfaces unless absolutely necessary.
- Monitor Network Activity: Use security tools to detect unusual network behavior indicative of botnet activity.
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













