FIN7 Hacking Group Selling “AvNeutralizer” Tool to Other Hackers

The notorious FIN7 hacking group, active since 2013, is now selling its custom “AvNeutralizer” tool. This sophisticated software is designed to evade detection by disabling enterprise endpoint protection software on corporate networks. The tool, also known as AuKill, has been linked to several ransomware operations, highlighting the ongoing threat posed by FIN7.
Background on FIN7
FIN7, believed to be a Russian hacking group, initially engaged in financial fraud by stealing debit and credit card information. Over time, they expanded into ransomware, associating with platforms like DarkSide and BlackMatter. They are also suspected of involvement with BlackCat ransomware, which recently conducted an exit scam.
The group is notorious for its sophisticated phishing attacks, custom malware, and tools. They even created a fake security company, Bastion Secure, to hire unwitting developers for their malicious activities. FIN7 operates under various aliases, including Sangria Tempest, Carbon Spider, and the Carbanak Group.
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
AvNeutralizer: A Tool for Disablement
SentinelOne’s recent report reveals that FIN7 has been selling AvNeutralizer since 2022. Initially spotted in BlackBasta ransomware attacks, the tool has since been used by other ransomware operations like AvosLocker, MedusaLocker, BlackCat, Trigona, and LockBit.
“AvNeutralizer” tool is a sophisticated piece of malware developed by the FIN7 hacking group to disable antivirus and endpoint detection and response (EDR) software on infected systems. This tool leverages legitimate system drivers to terminate security processes, rendering the victim’s defenses ineffective and allowing the malware to operate undetected.
AvNeutralizer is sold on Russian-speaking hacking forums under aliases such as “goodsoft,” “lefroggy,” “killerAV,” and “Stupor.” Prices for the tool range from $4,000 to $15,000. The tool leverages legitimate SysInternals Process Explorer driver to terminate antivirus processes, targeting products from vendors like Windows Defender, Sophos, SentinelOne, Panda, Elastic, and Symantec.
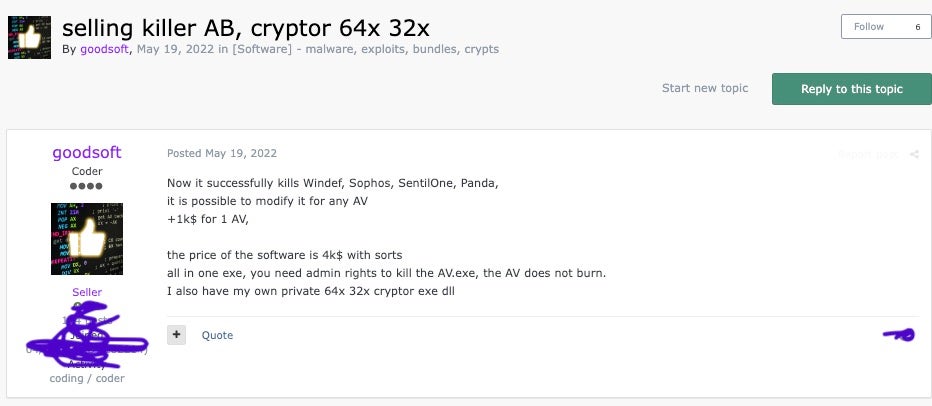 FIN7 actor selling AVNeutralizer on a hacking forums
FIN7 actor selling AVNeutralizer on a hacking forums
Source: SentinelOne
Technical Details
Recent versions of AvNeutralizer use the Windows ProcLaunchMon.sys driver to disable processes. This driver is found in the system drivers directory and, combined with updated Process Explorer drivers, can create failures in protected processes, leading to a denial of service condition.
Attack Chain
Initial Access: The threat actors gain initial access to the target network through phishing attacks, malicious USB devices, or exploiting vulnerabilities in exposed services such as RDP (Remote Desktop Protocol).
Execution of AvNeutralizer: Once inside the network, the attackers deploy AvNeutralizer. The tool uses the exploited drivers to disable antivirus and EDR software.
Process Hanging and Termination: AvNeutralizer hangs or terminates security processes using the legitimate drivers. By exploiting these drivers, it creates a failure in the protected processes, leading to a denial of service condition.
Payload Deployment: With the security software disabled, the attackers can deploy additional payloads, such as ransomware, without fear of detection. This allows them to encrypt files, exfiltrate data, or perform other malicious activities unimpeded.
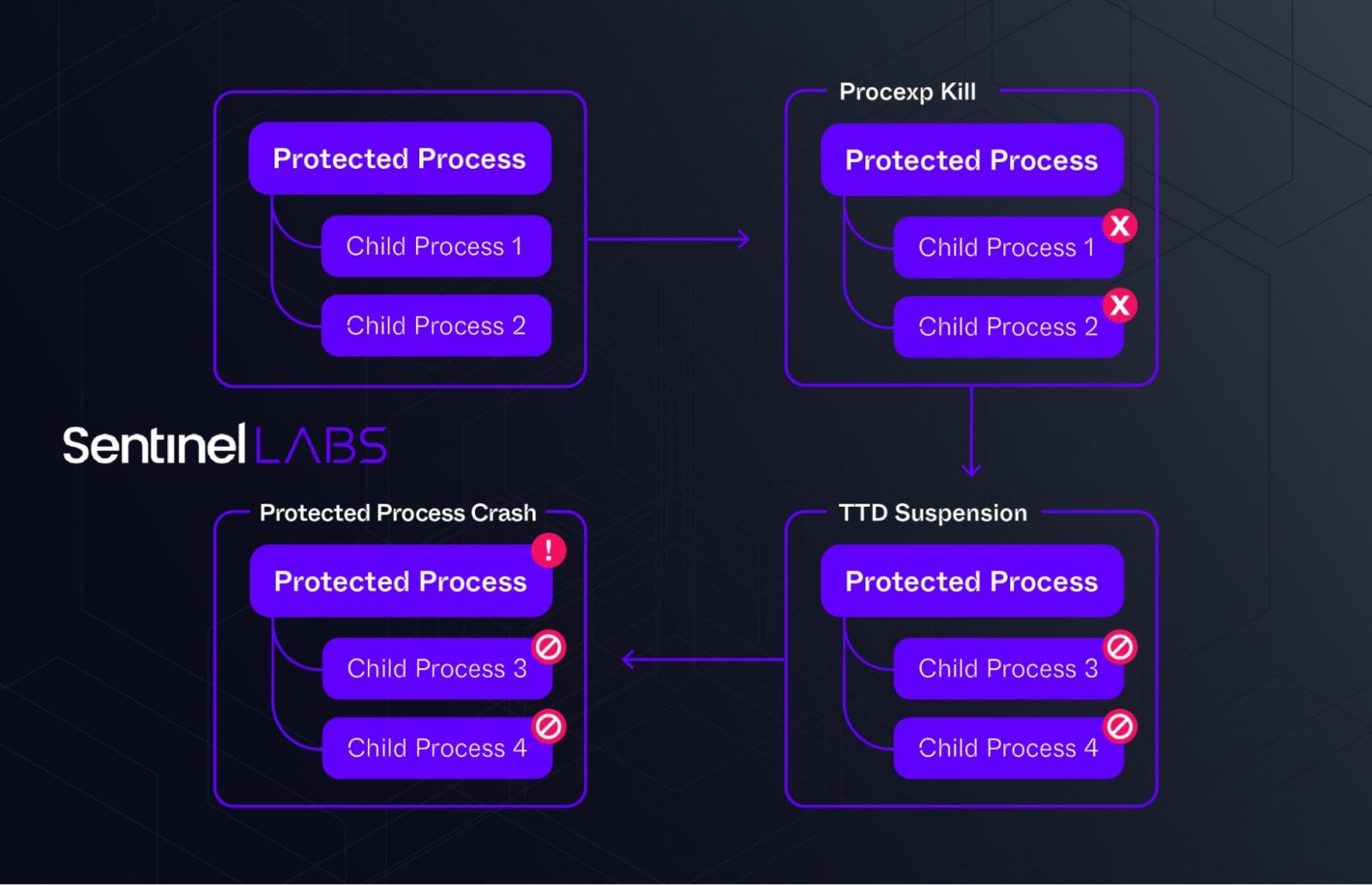 AvNeutralizer Workflow
AvNeutralizer Workflow
Source: SentinelOne
Trending: Offensive Security Tool: DDoSlayer
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













