FinalDraft Malware Uses Outlook Drafts for Covert C2

See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Capabilities of FinalDraft
The backdoor supports 37 different commands, allowing attackers to:
- Steal sensitive data (files, credentials, system information)
- Inject malicious payloads into legitimate processes (e.g.,
mspaint.exe) - Execute PowerShell commands without launching
powershell.exe - Perform Pass-the-Hash attacks for lateral movement
- Proxy network traffic to conceal malicious activity
Researchers also found a Linux variant of FinalDraft, which can still use Outlook as a C2 channel and supports DNS, ICMP, TCP, and UDP-based communication.
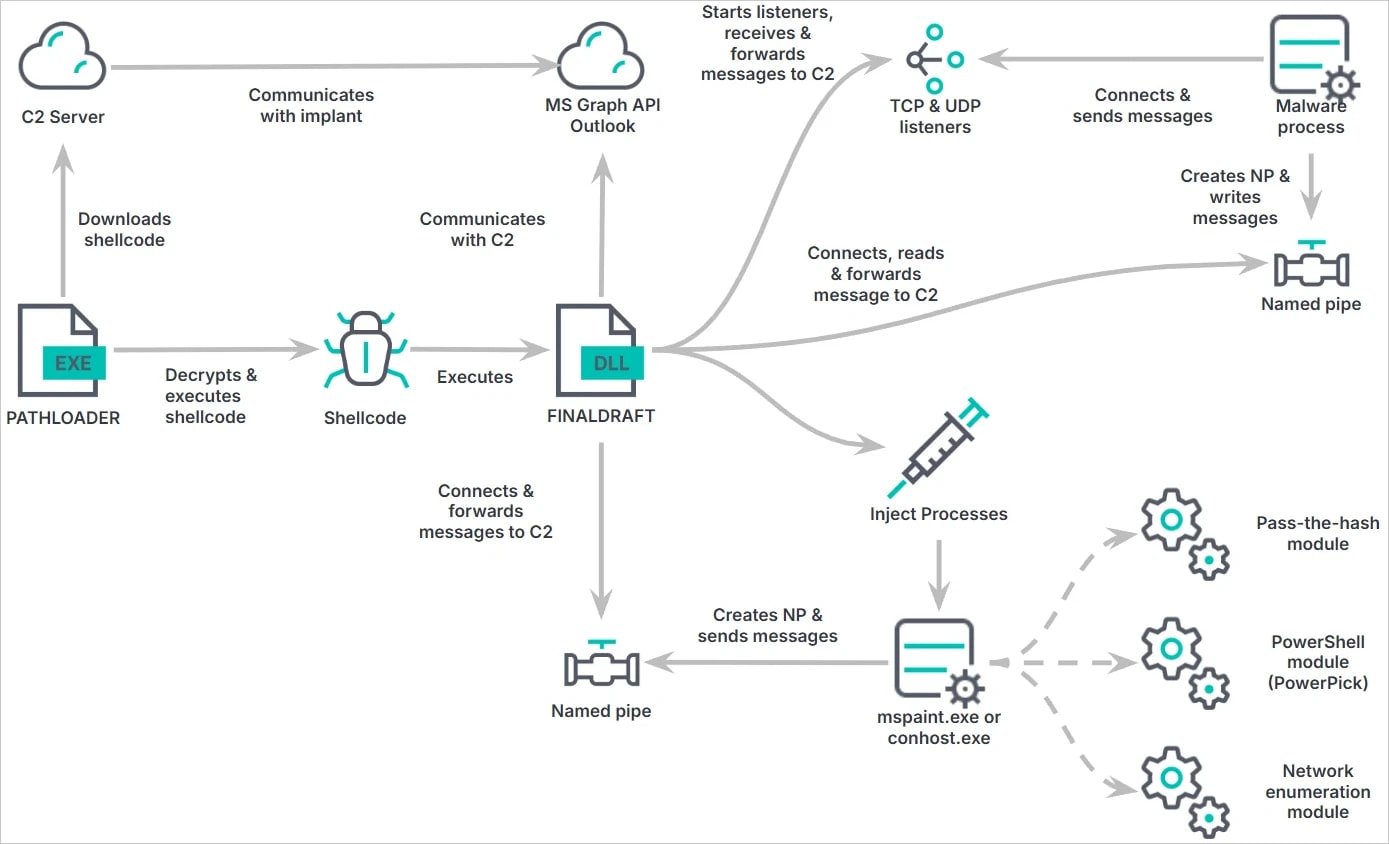 FinalDraft operational overview
FinalDraft operational overview
Source: Elastic Security
REF7707: A Coordinated Espionage Operation
Elastic Security Labs attributes these attacks to a cyber-espionage campaign dubbed REF7707, which primarily targeted a foreign ministry in South America. However, infrastructure analysis revealed connections to additional victims in Southeast Asia, indicating a larger operation.
Key Findings:
- The attackers leveraged compromised telecommunications and ISP infrastructure in Southeast Asia
- A Southeast Asian university’s storage system was used to host malware payloads, suggesting either a prior breach or a supply chain compromise
- Another malware loader named GuidLoader was discovered, capable of decrypting and executing payloads in memory
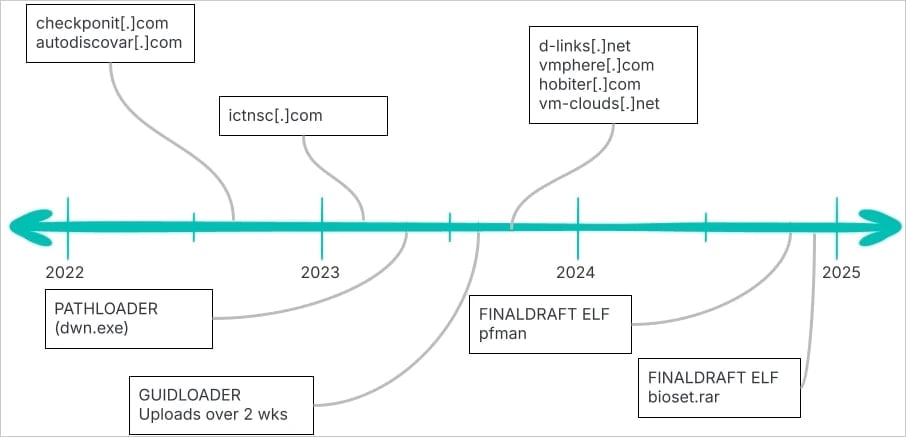 REF7077 malware timeline
REF7077 malware timeline
Source: Elastic Security
Trending: Recon Tool: getJS
Mitigation and Detection
To defend against this attack, organizations should:
- Monitor Outlook drafts for suspicious activity
- Restrict OAuth token access and enforce strict authentication policies
- Analyze network traffic for unexpected Microsoft Graph API requests
- Use YARA rules provided by Elastic Security Labs to detect FinalDraft, PathLoader, and GuidLoader
References:
Elastic Security Labs has published YARA rules and detailed indicators of compromise in their official reports.
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com


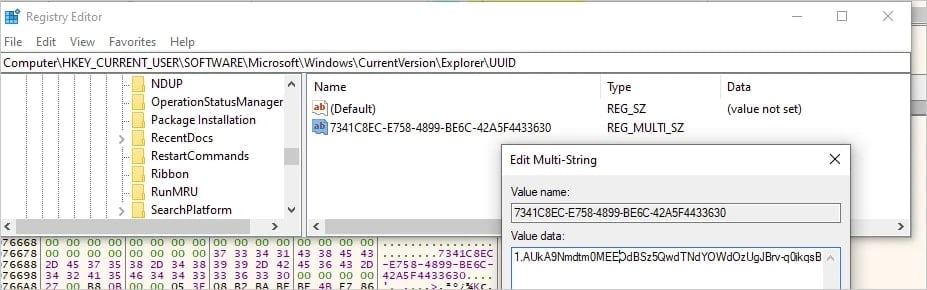 Token stored in the Windows Registry
Token stored in the Windows Registry










