Financially Motivated Hackers Exploit Legitimate Platforms in USB-Initiated Attacks

A financially motivated threat actor, identified as UNC4990 by Mandiant, has raised concerns with a sophisticated attack strategy involving USB devices and the strategic use of legitimate online platforms such as GitHub, Vimeo, and Ars Technica. This campaign, active since 2020 and primarily targeting users in Italy, kicks off with victims unknowingly launching a malicious LNK shortcut file on a USB drive. The attackers, keen on maintaining a covert approach, encode and embed payloads within seemingly harmless content on forum user profiles and video descriptions. These payloads, camouflaged as text strings, play a pivotal role in downloading and executing malware in later stages of the attack.
UNC4990 demonstrates a knack for involuntary payload hosting, initially utilizing encoded text files on GitHub and GitLab before switching to leveraging Vimeo and Ars Technica. Importantly, the attackers do not exploit vulnerabilities in these platforms but ingeniously use regular features like an Ars Technica forum profile’s About page or a Vimeo video description to discreetly host the obfuscated payload.
.png) Vimeo video hidding malicious code in the description
Vimeo video hidding malicious code in the description
Source: Mandiant
These seemingly harmless text strings, posing no direct threat to site visitors, serve as an effective way to bypass security systems, leveraging the trustworthiness and robust content delivery networks of these platforms.
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
The attackers benefit from the stealthy integration of payloads within legitimate content, making it challenging to pinpoint and remove the malicious code. This approach, combined with the ability to reintroduce payloads on different platforms, showcases the adaptability and resilience of UNC4990’s tactics.
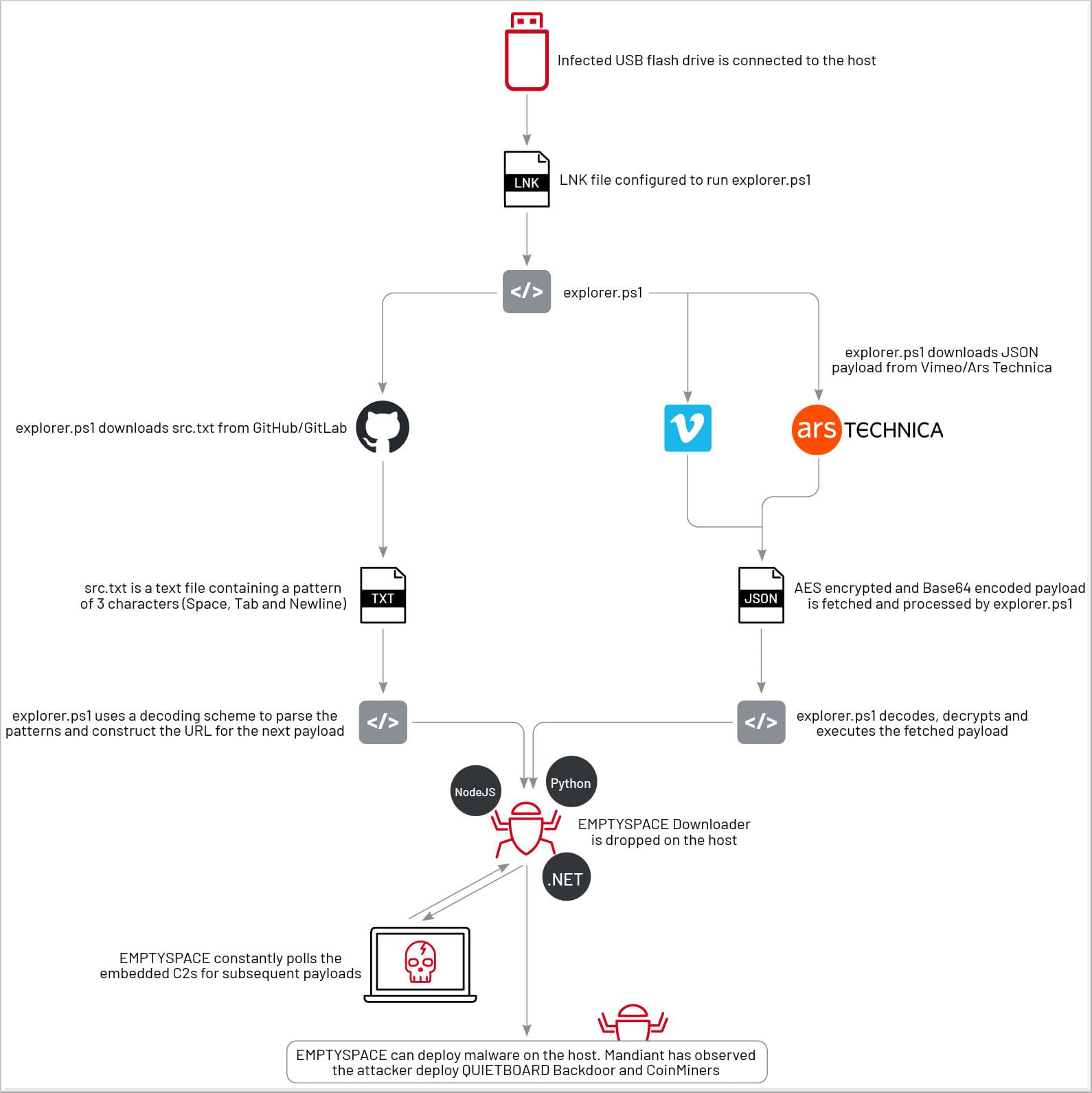 Complete UNC4990 attack chain
Complete UNC4990 attack chain
Source: Mandiant
The PowerShell script, once initiated, executes intermediate payloads fetched from legitimate sites, resulting in the deployment of the ‘EMPTYSPACE’ malware. This establishes communication with the command and control (C2) server, leading to the download of a sophisticated backdoor named ‘QUIETBOARD,’ along with crypto coin miners that have generated profits exceeding $55,000.
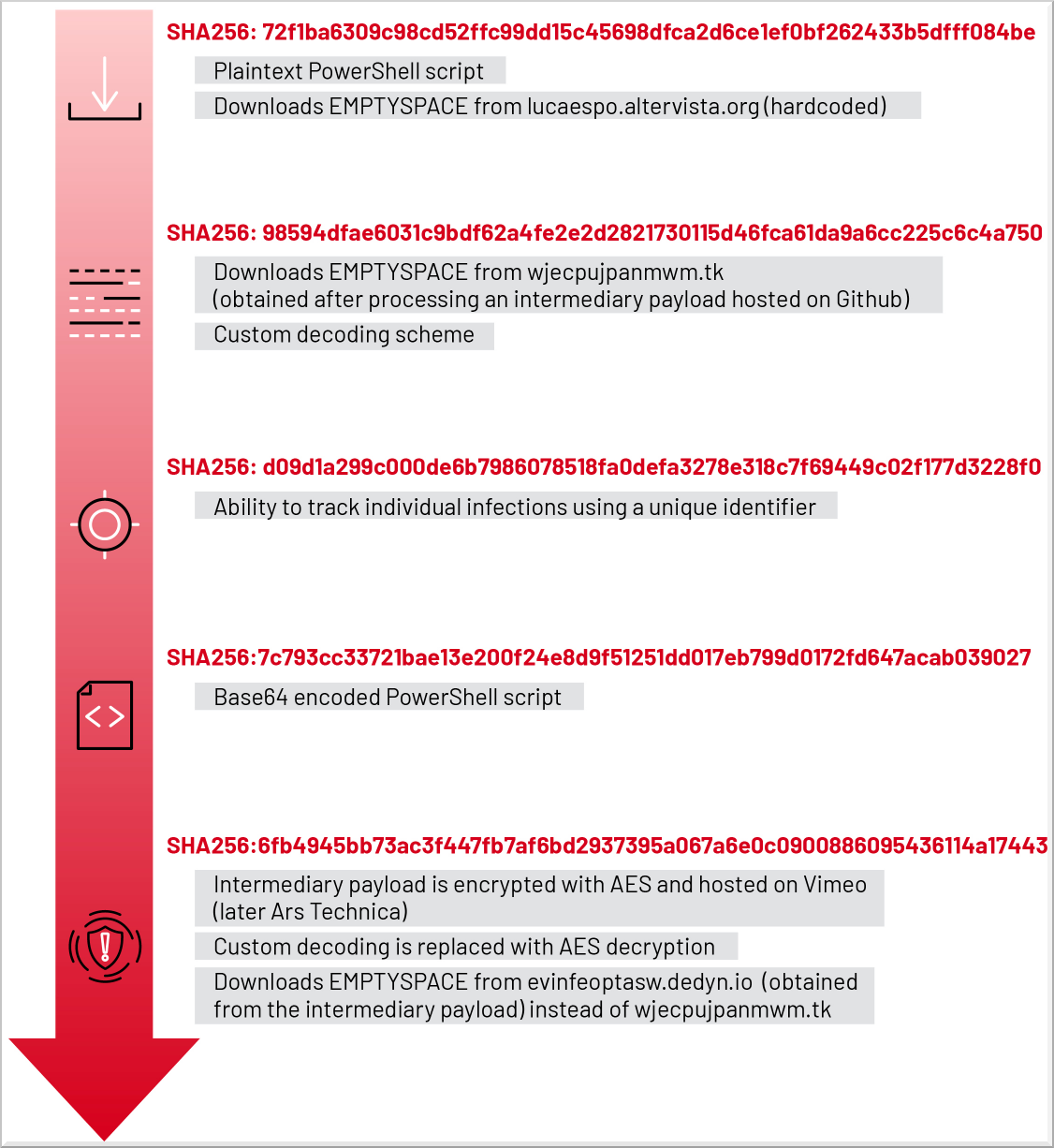 Evolution of the PowerShell script
Evolution of the PowerShell script
Source: Mandiant
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













