FortiGate Leak: Over 15,000 Devices’ Configs and VPN Credentials Exposed by New Hacking Group

See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Implications of the Leak
Despite being over two years old, the leaked data still poses severe risks. The exposed configuration files contain sensitive information, such as:
- Firewall rules, offering insight into network defenses.
- Credentials, which if unchanged, could grant attackers access to the networks.
Recommendations for Impacted Organizations
Organizations using FortiGate devices are urged to take immediate action:
- Change all exposed credentials: Update VPN and admin passwords immediately.
- Patch to the latest firmware: Ensure devices are running versions newer than 7.2.2 to address vulnerabilities.
- Audit network configurations: Review for unauthorized accounts, such as the ‘fortigate-tech-support’ super_admin.
- Monitor for potential threats: Watch for unusual traffic or access attempts originating from leaked IP addresses.
Trending: Offensive Security Tool: XSRFProbe
History of Fortinet Exploits
This is not the first time Fortinet devices have been targeted. In 2021, nearly 500,000 Fortinet VPN credentials were leaked due to exploitation of CVE-2018-13379. This pattern underscores the importance of timely patching and robust credential management.
Response from the Community
Beaumont plans to release a list of IP addresses from the leak to assist FortiGate administrators in assessing whether their devices were affected. Both Belsen Group and Fortinet have been contacted for comments, and updates to this story will follow as more information becomes available.
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com


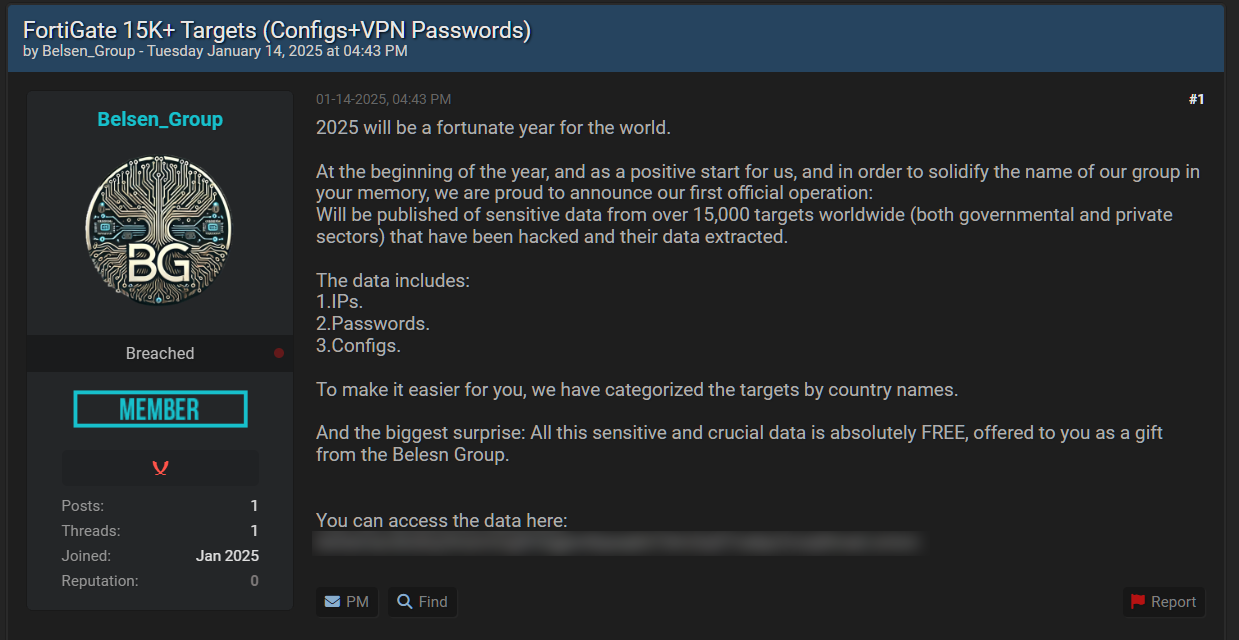 Post on hacking forum
Post on hacking forum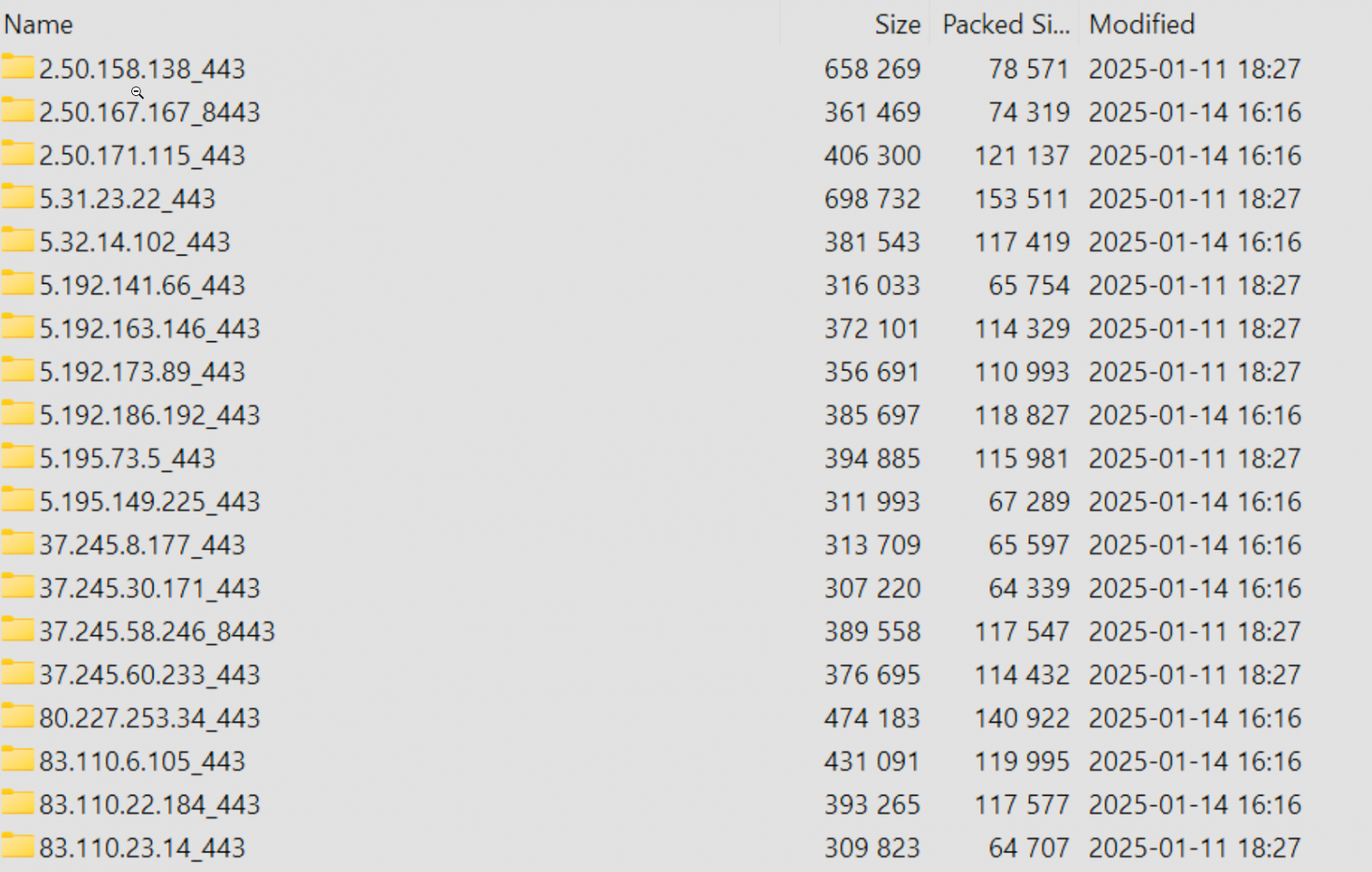 IP address folder for FortiGate devices and their configs
IP address folder for FortiGate devices and their configs










