Fortinet Discloses Critical ‘FortiJump’ Zero-Day Flaw Exploited Since June

A critical vulnerability in Fortinet’s FortiManager system, dubbed ‘FortiJump’ and tracked as CVE-2024-47575, has been actively exploited since June 2024, according to a report by Mandiant. This zero-day flaw has compromised over 50 servers, making it a significant cyber threat in recent months.
Fortinet Confirms Authentication Flaw in FortiManager API
Rumors of the FortiManager zero-day exploitation had been circulating for days, following Fortinet’s private notifications to its customers. Today, Fortinet confirmed that the vulnerability is due to a missing authentication flaw in the FortiGate to FortiManager Protocol (FGFM) API. This flaw allowed attackers to send commands to FortiManager servers and managed FortiGate devices without proper authorization.
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Attackers Exploit Unauthenticated Access to Steal Data
Threat actors were able to take advantage of the vulnerability by using attacker-controlled FortiManager and FortiGate devices with valid certificates. Once connected to an exposed FortiManager server, they could execute API commands and steal sensitive configuration data from the managed devices.
Fortinet has since issued patches and recommended mitigation methods, such as restricting connections to specific IP addresses and enabling the fgfm-deny-unknown command to prevent unregistered devices from connecting.
Exploited by UNC5820 Threat Actor Since June 2024
Mandiant reports that a threat actor tracked as UNC5820 has been exploiting FortiManager systems since as early as June 27, 2024. The attackers exfiltrated configuration data from FortiGate devices managed by FortiManager, including user credentials and FortiOS256-hashed passwords.
This stolen data could allow the attackers to further compromise the FortiManager, infiltrate the connected FortiGate devices, and potentially expand their reach within enterprise environments.
Mandiant Uncovers Attack Chain and Exploited Devices
The first attack was observed coming from IP address 45.32.41[.]202, where the attackers registered an unauthorized FortiManager-VM to an exposed FortiManager server. The malicious device was listed as “localhost” and used a fake serial number to blend in. Mandiant discovered that the attackers created multiple files during the breach, including gzip archives of exfiltrated data and information about unregistered devices.
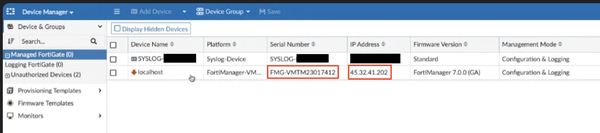 Attacker-controlled FortiManager-VM
Attacker-controlled FortiManager-VM
Source: Mandiant
However, Mandiant’s investigation revealed no malicious payloads or signs of further tampering with the system files. The attackers have so far only been observed stealing configuration data.
Trending: Recon Tool: emailFinder
Uncertain Goals: UNC5820’s Next Move Remains Unclear
Although the attackers have successfully exfiltrated sensitive data, there have been no indications of additional exploitation or lateral movement to other systems. Mandiant and Fortinet notified customers of the attack, prompting them to take measures such as changing credentials and securing their networks.
UNC5820’s goals and location remain unknown at this time. Mandiant is continuing its investigation and will update its findings as more information becomes available.
Fortinet Issues Advisory for CVE-2024-47575
Fortinet has published a security advisory for CVE-2024-47575 (FG-IR-24-423), which includes detailed mitigation and recovery methods. The advisory also provides Indicators of Compromise (IOCs), such as suspicious IP addresses and log entries, to help detect compromised FortiManager servers.
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













