Fortune 50 Company Pays Record-Breaking $75 Million Ransom to Dark Angels
Historic Ransom Payment
A Fortune 50 company has made headlines by paying a record-breaking $75 million ransom to the Dark Angels ransomware gang, according to a report by Zscaler ThreatLabz.
“In early 2024, ThreatLabz uncovered a victim who paid Dark Angels $75 million, higher than any publicly known amount—an achievement that’s bound to attract the interest of other attackers looking to replicate such success by adopting their key tactics,” reads the 2024 Zscaler Ransomware Report.
Confirmation and Context
This unprecedented payment was further corroborated by crypto intelligence firm Chainalysis, which tweeted about it on X. Prior to this, the largest known ransom payment was $40 million, made by insurance giant CNA following an Evil Corp ransomware attack.
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
While Zscaler did not disclose the identity of the company that paid the $75 million ransom, they mentioned it was a Fortune 50 company targeted in early 2024. Notably, pharmaceutical giant Cencora, ranked #10 on the Fortune 50 list, suffered a cyberattack in February 2024. No ransomware gang claimed responsibility for this attack, potentially indicating a ransom was paid. BleepingComputer has reached out to Cencora for confirmation but has yet to receive a response.
Who Are the Dark Angels?
Dark Angels is a ransomware operation that emerged in May 2022, targeting companies worldwide. Similar to other human-operated ransomware gangs, Dark Angels breaches corporate networks, moves laterally to gain administrative access, and steals data from compromised servers. This stolen data is used as leverage to demand ransom payments.
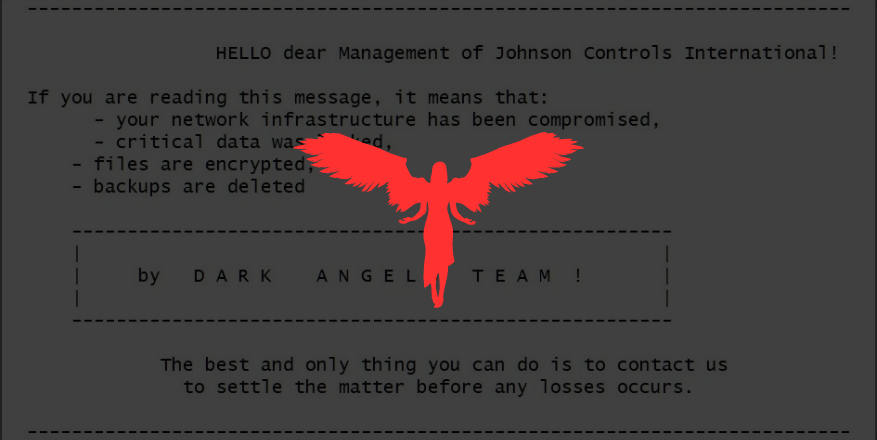
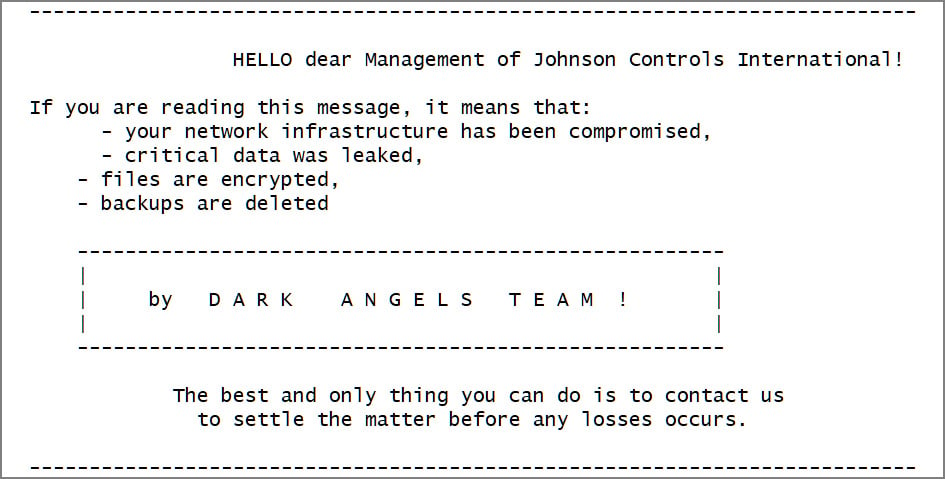 Dark Angels ransom note
Dark Angels ransom note
Source: BleepingComputer
Evolving Tactics
Initially, Dark Angels used Windows and VMware ESXi encryptors based on the leaked Babuk ransomware source code. Over time, they switched to a Linux encryptor, the same one used by Ragnar Locker since 2021. Following Ragnar Locker’s disruption by law enforcement in 2023, this Linux encryptor was employed in a Dark Angels attack on Johnson Controls, where they claimed to have stolen 27 TB of corporate data and demanded a $51 million ransom.
Trending: 10 Misconceptions about Hacking
Trending: Digital Forensics Tool: Horus
Data Leak Site and Strategy
Dark Angels operates a data leak site named ‘Dunghill Leaks’ to extort victims by threatening to leak data if the ransom is not paid. Zscaler ThreatLabz notes that Dark Angels employs the “Big Game Hunting” strategy, targeting a few high-value companies for massive payouts rather than attacking many companies for smaller ransoms.
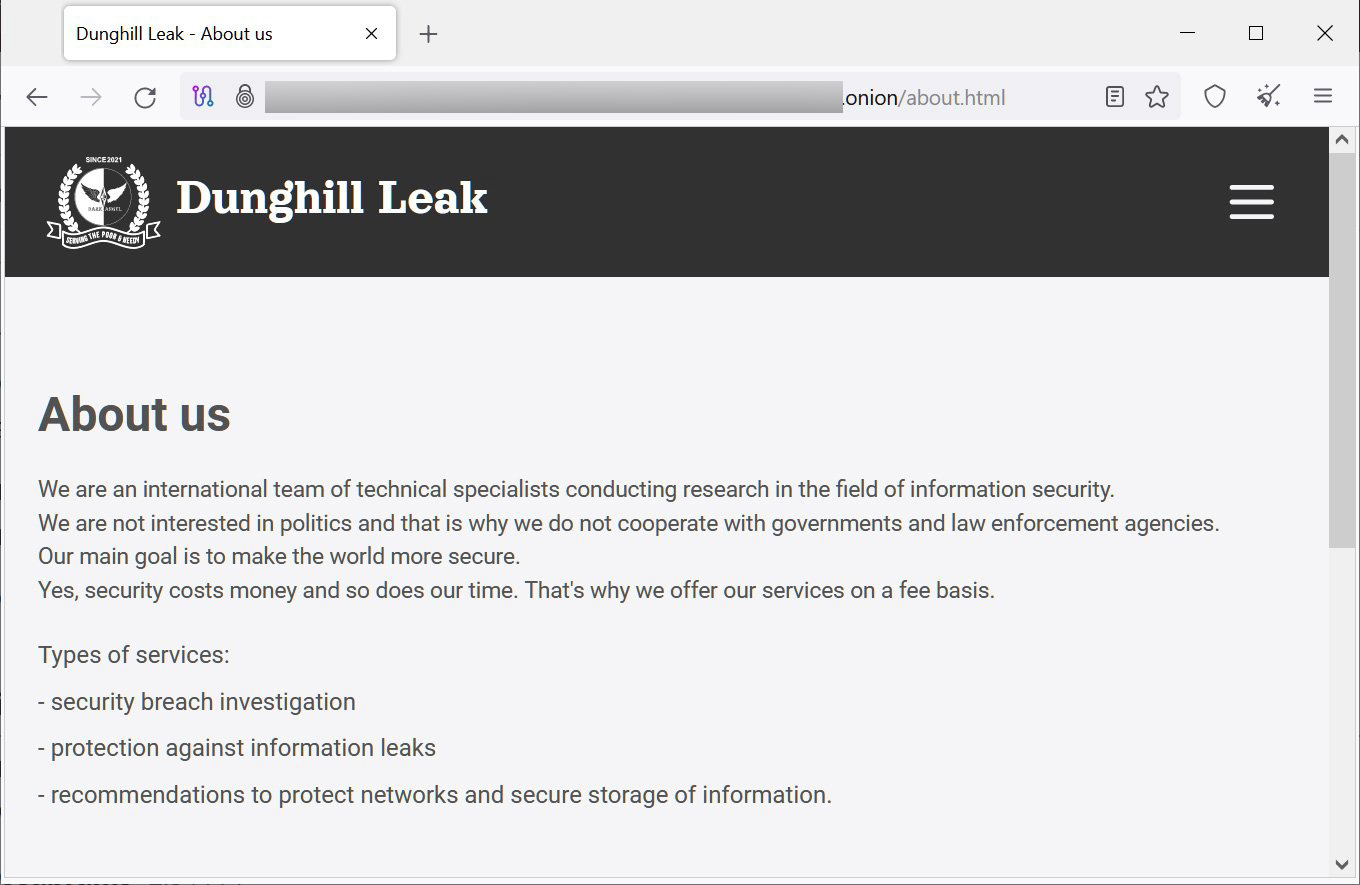 Dark Angel’s ‘Dunghill’ Leaks data leak site
Dark Angel’s ‘Dunghill’ Leaks data leak site
Source: BleepingComputer
“The Dark Angels group employs a highly targeted approach, typically attacking a single large company at a time,” explains the Zscaler ThreatLabz researchers. This strategy contrasts with most ransomware groups, which indiscriminately target victims and outsource attacks to affiliate networks of initial access brokers and penetration testing teams.
Trend in Ransomware Attacks
According to Chainalysis, the Big Game Hunting tactic has become a dominant trend among ransomware gangs over the past few years, highlighting a shift towards more strategic and high-stakes attacks.
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













