From Crypto Mining to BEC: Microsoft Exposes the Dark Side of OAuth Misuse

Reading Time: 3 Minutes
Financially-Motivated Threat Actors Exploit OAuth for Illicit Activities
Microsoft has issued a warning about the exploitation of OAuth applications by financially-motivated threat actors to automate Business Email Compromise (BEC) and phishing attacks, push spam, and deploy virtual machines for cryptomining. OAuth, an open standard for granting secure delegated access to server resources, has become a tool for cybercriminals to carry out their illicit activities.
Recent incidents investigated by Microsoft Threat Intelligence experts have revealed that attackers are targeting user accounts lacking robust authentication mechanisms, such as multi-factor authentication. These attacks focus on accounts with permissions to create or modify OAuth apps, allowing the hijacked accounts to be used for creating new OAuth applications with high privileges, enabling malicious activities to remain hidden and ensuring continued access even if the original account is lost.
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Exploiting High-Privileged OAuth Apps for Illicit Activities
The high-privileged OAuth apps created by threat actors are being utilized for a range of illicit activities, including deploying virtual machines for cryptocurrency mining, perpetrating Business Email Compromise (BEC) attacks, and launching spam campaigns that exploit compromised organizations’ domain names. One notable instance involves a threat actor tracked as Storm-1283, who created an OAuth app to deploy cryptocurrency mining virtual machines, resulting in significant financial impact on targeted organizations.
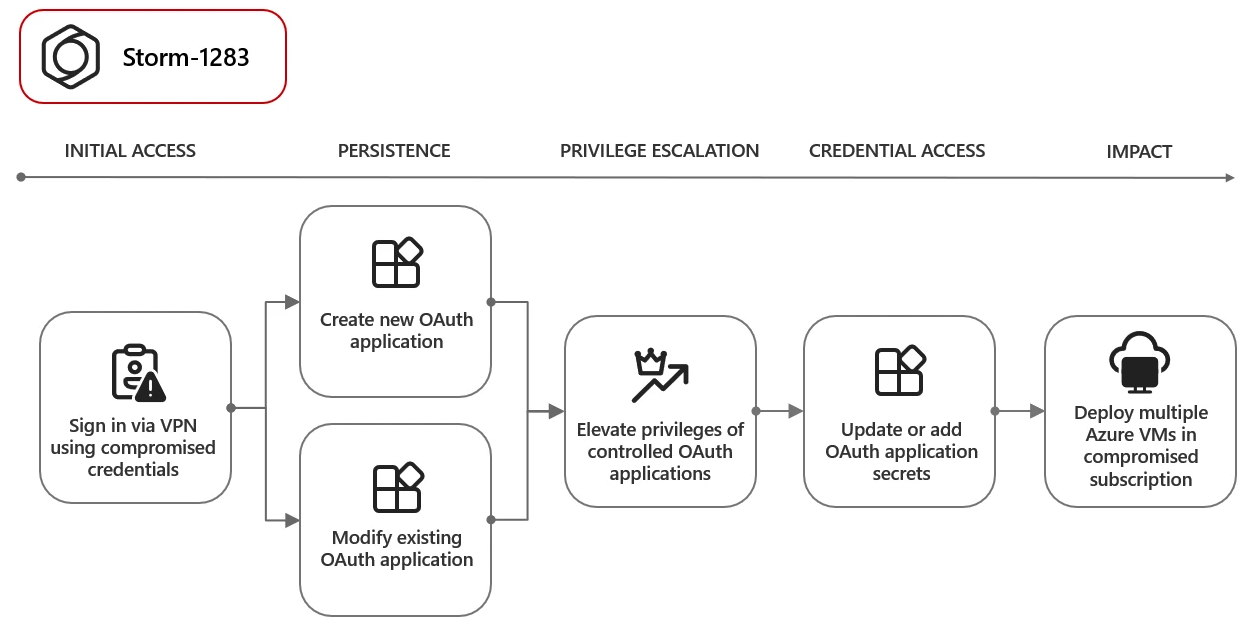 Storm-1283 OAuth attack (Microsoft)
Storm-1283 OAuth attack (Microsoft)Threat actors have exploited OAuth apps created using compromised accounts to maintain persistence and launch phishing campaigns, as well as conduct Business Email Compromise (BEC) reconnaissance. These attackers have used breached accounts for various malicious activities, including creating multitenant OAuth apps for persistence and sending phishing emails via the Microsoft Graph API.
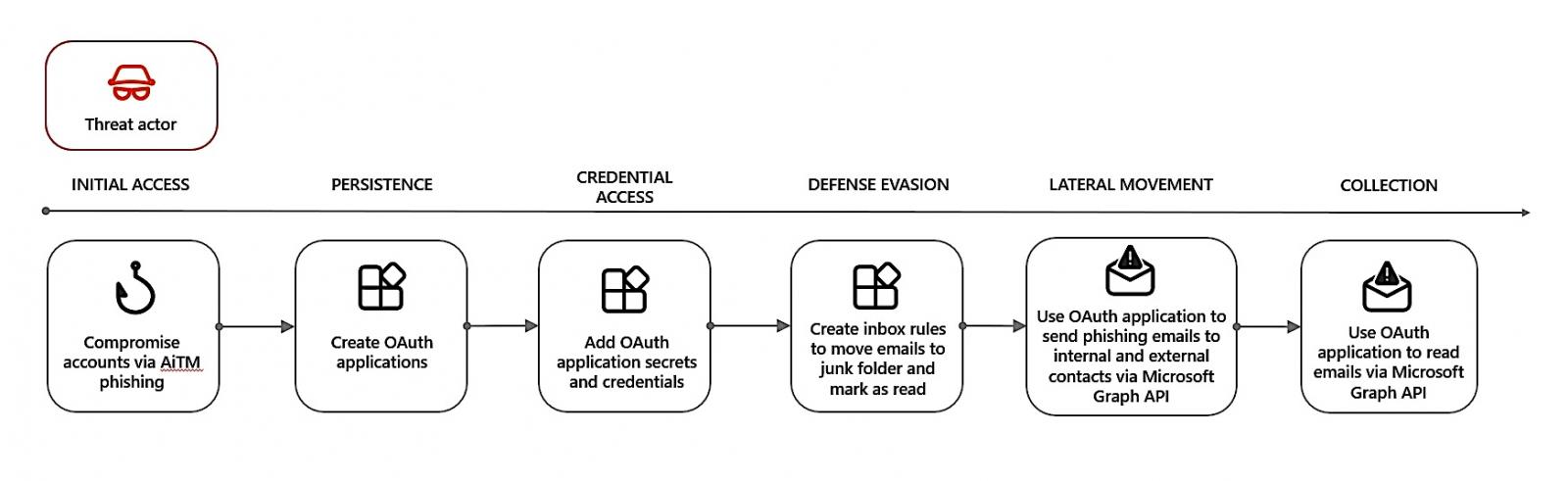 OAuth misused for phishing attacks (Microsoft)
OAuth misused for phishing attacks (Microsoft)Trending: Recon Tool: ReconSpider
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













