Game Developers on Steam to Face SMS Security Check in Response to Malicious Updates

Valve, the company behind the popular gaming platform Steam, has taken proactive steps to enhance security after recent incidents involving malicious updates being pushed to players via compromised Steamworks accounts. Steamworks is a set of tools and services that game developers and publishers use to distribute their products on Steam.
Throughout August and September 2023, there was an increased number of reports regarding compromised Steamworks accounts. Attackers exploited these accounts to upload malicious builds, ultimately infecting players with malware. Valve reassured the gaming community that the impact of these attacks was limited to a relatively small number of users, and these affected users were individually informed by the company.
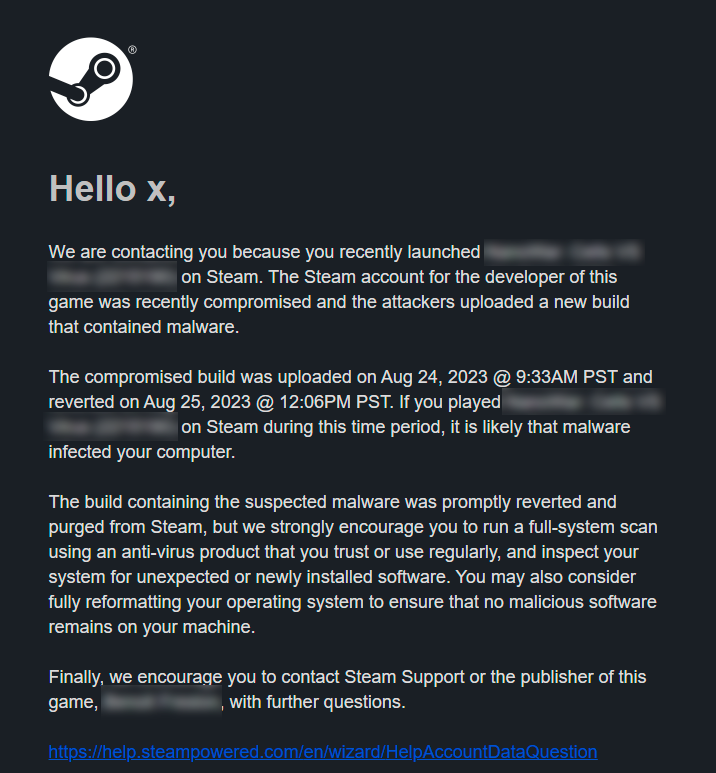 Notice sent to impacted players (@SteamDB)
Notice sent to impacted players (@SteamDB)
To address this security challenge, Valve is implementing a new SMS-based security check, effective October 24, 2023. Game developers will be required to pass this security check before they can push updates on the default release branch. The same SMS-based confirmation will be enforced for adding new users to the Steamworks partner group. Previously, adding new users required an email-based confirmation; now, an SMS code will be necessary for verification.
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
Valve’s announcement states, “As part of a security update, any Steamworks account setting builds live on the default/public branch of a released app will need to have a phone number associated with their account so that Steam can text you a confirmation code before continuing. The same will be true for any Steamworks account that needs to add new users.”
Valve also intends to extend this requirement to other Steamworks actions in the future.
However, while this SMS-based verification is a positive step towards enhancing supply chain security on Steam, it’s not a flawless solution. Some developers have noted that it wouldn’t have prevented the attack in which their accounts were compromised.
Hey Simon, I'm the developer of this game. ALL my accounts were hacked by a Token Grabber Malware. Unfortunately, the 2FA i s useless if the token is still active. I just used my dev account to release the game few hours before the hack I suppose.
— Benoît Freslon 👨💻 VideoGameCreation.fr (@BenoitFreslon) October 11, 2023
In some cases, attackers utilized information-stealing malware to gain unauthorized access. Additionally, SMS-based two-factor authentication (2FA) has its vulnerabilities, including SIM-swap attacks.
Trending: Recon Tool: fetchmeurls
To further bolster security, especially for projects with large communities, a more robust and modern solution might involve enforcing authenticator apps or physical security keys. This would add an extra layer of protection against evolving cyber threats. Valve’s response is undoubtedly a step in the right direction, but the ever-changing landscape of cyberattacks requires ongoing vigilance and adaptation.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com












