GEOBOX: Raspberry Pi Transforms Into A Tool For Fraud And Anonymization

Cybercriminals have escalated their tactics, repurposing innocuous devices like Raspberry Pi into potent, ‘plug-and-play’ instruments for digital fraud. Augmented with GEOBOX, their operations attain a new level of sophistication, enabling manipulation of GPS data, network simulation, Wi-Fi spoofing, and evasion of anti-fraud filters.
Recent research from Resecurity, a US-based cybersecurity solutions provider, has unveiled a troubling trend. Cybercriminals are leveraging IoT devices for illicit endeavors, employing operational security (OPSEC) techniques and customizable configurations to operate without leaving traces, ensuring anonymity for their activities.
According to Resecurity’s Cyber Threat Intelligence team, a significant discovery emerged from the depths of the Dark Web: GEOBOX, a malevolent tool designed to transform ordinary IoT hardware into potent cyber weapons. GEOBOX marks a paradigm shift in cybercriminal tactics, underscoring the evolving nature of digital threats.
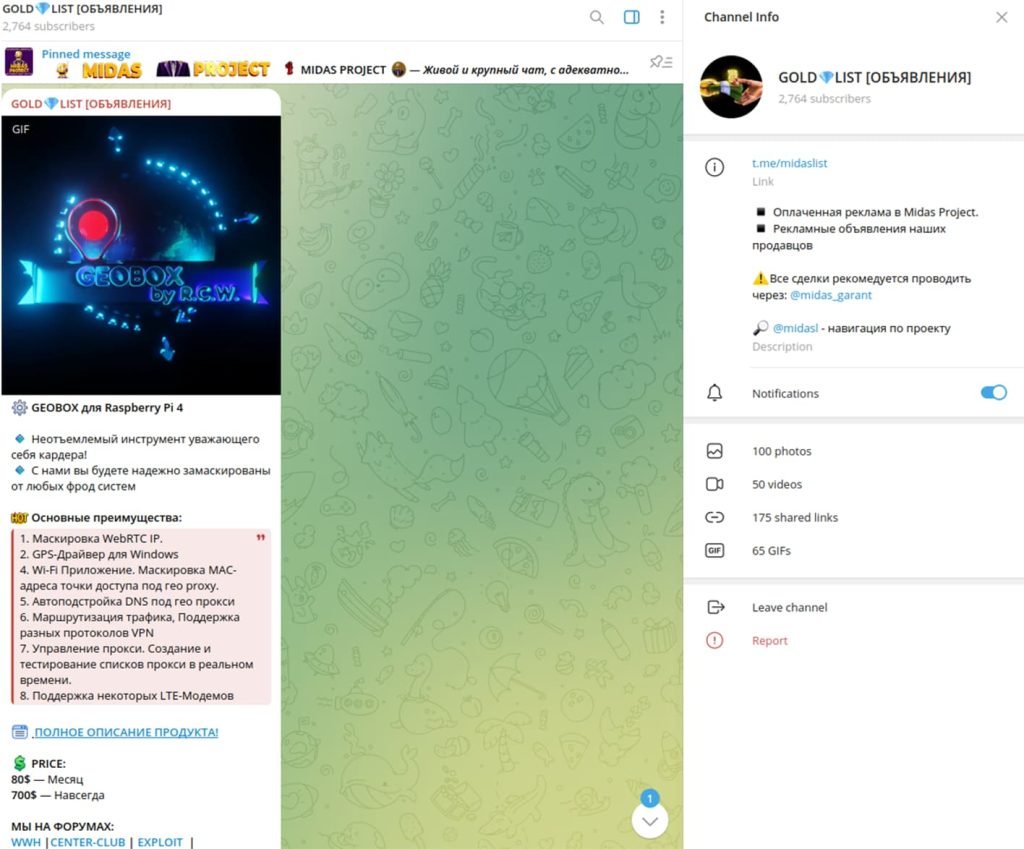 GEOBOX is being sold on Telegram (Screenshot credit: Resecurity)
GEOBOX is being sold on Telegram (Screenshot credit: Resecurity)
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Specifically crafted for Raspberry Pi 4 Model B devices, GEOBOX facilitates cybercriminals in anonymization and fraud. Its existence came to light during an investigation into an online banking theft involving a high-net-worth client of a Fortune 100 financial company, prompting deeper scrutiny by researchers.
The emergence of GEOBOX follows closely on the heels of another dark web tool, TMChecker, which has armed ransomware gangs, particularly targeting the e-commerce and aviation sectors with precision cyberattacks.
Resecurity’s research, shared exclusively with Hackread.com, revealed the utilization of multiple internet-connected GEOBOX devices as proxies by threat actors, strategically positioned at remote locations to enhance their anonymity. This strategy complicates investigation and tracking efforts, as GEOBOX devices do not retain logs by default. Notably, Resecurity observed a malicious actor utilizing GEOBOX with two LTE-based wireless modems for heightened anonymization, particularly in remote connections.
Available for a lifetime fee of $700 or a monthly rate of $80, payable in cryptocurrency, GEOBOX is advertised on major underground forums and Telegram. Its user manual provides comprehensive instructions on downloading and installing the Raspberry Pi OS using Raspberry Pi Imager, acquiring the GEOBOX Software Image, and operating the GEOBOX software.
Trending: Digital Forensics Tool: mailMeta


