GitHub code scanning now finds more security vulnerabilities

Reading Time: 1 Minute
Code hosting platform GitHub today launched new machine learning-based code scanning analysis features that will automatically discover more common security vulnerabilities before they end up in production.
These new experimental static analysis features are now available for JavaScript and TypeScript GitHub repositories in public beta.
“With the new analysis capabilities, code scanning can surface even more alerts for four common vulnerability patterns: cross-site scripting (XSS), path injection, NoSQL injection, and SQL injection,” said GitHub’s Tiferet Gazit and Alona Hlobina.
“Together, these four vulnerability types account for many of the recent vulnerabilities (CVEs) in the JavaScript/TypeScript ecosystem, and improving code scanning’s ability to detect such vulnerabilities early in the development process is key in helping developers write more secure code.”
Security vulnerabilities discovered by the new experimental code analysis features will show up as alerts in the ‘Security’ tab of enrolled repositories.
These new alerts are marked using an ‘Experimental’ label and will also be available via the pull requests tab.
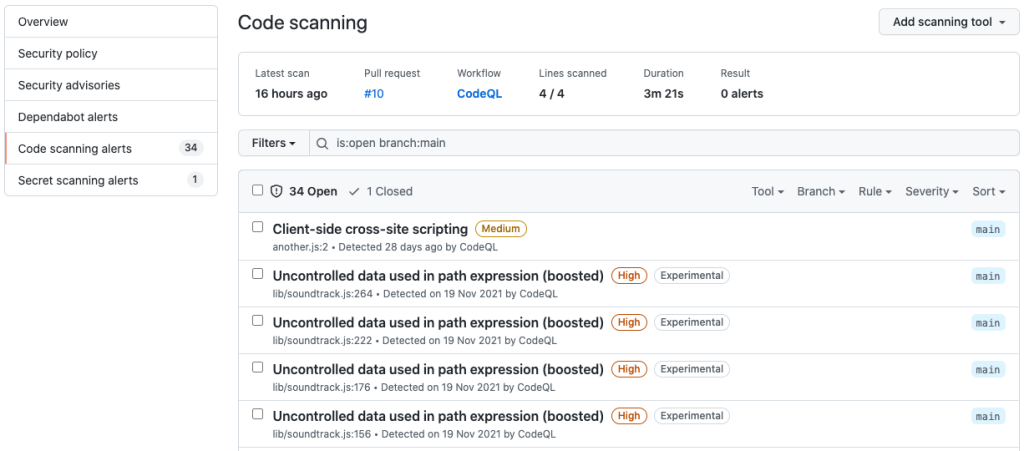
The CodeQL code analysis engine, which powers GitHub’s code scanning, was added to the platform’s capabilities after GitHub acquired code-analysis platform Semmle in September 2019.
GitHub released the first code scanning beta at GitHub Satellite in May 2020 and announced its general availability four months later, in September 2020.
During beta testing, the code scanning feature was used to scan more than 12,000 repositories 1.4 million times and found over 20,000 security issues, including remote code execution (RCE), SQL injection, and cross-site scripting (XSS) flaws.
GitHub Code scanning is free for public repositories and is available as a GitHub Advanced Security feature for GitHub Enterprise private repositories.
To configure code analysis for your JavaScript/TypeScript code, you can follow these instructions. The new features are available for code scanning’s security-extended and security-and-quality analysis suites.
“It’s important to note that while we continue to improve and test our machine learning models, this new experimental analysis can have a higher false-positive rate relative to results from our standard CodeQL analysis,” Gazit and Hlobina added.
“As with most machine learning models, the results will improve over time.”
See Also: OSINT & Recon Tool: Odin
See Also: How ILOVEYOU worm became the first global computer virus pandemic
Source: bleepingcomputer.com
Source Link












