GitHub introduces 2FA and quality of life improvements for npm

Reading Time: 3 Minutes
GitHub has announced the general availability of three significant improvements to npm (Node Package Manager), aiming to make using the software more secure and manageable.
In summary, the new features include a more streamlined login and publishing experience, the ability to link Twitter and GitHub accounts to npm, and a new package signature verification system.
At the same time, GitHub announced that the two-factor authentication program introduced in May 2022 is ready to exit beta and become available to all npm users.
The npm platform is a subsidiary of GitHub and is a package manager and repository (registry) for JavaScript coders, used by developers’ projects to download five billion packages daily.
It recently suffered large-scale security incidents that impacted hundreds of apps and websites, forcing GitHub to develop and urgently implement a security-boosting plan.
See Also: So you want to be a hacker?
Complete Offensive Security and Ethical Hacking Course
New features in npm
The new npm login and publishing system allows for authentication to be handled by the web browser, so valid authentication tokens can be retained on the same session for up to five minutes.
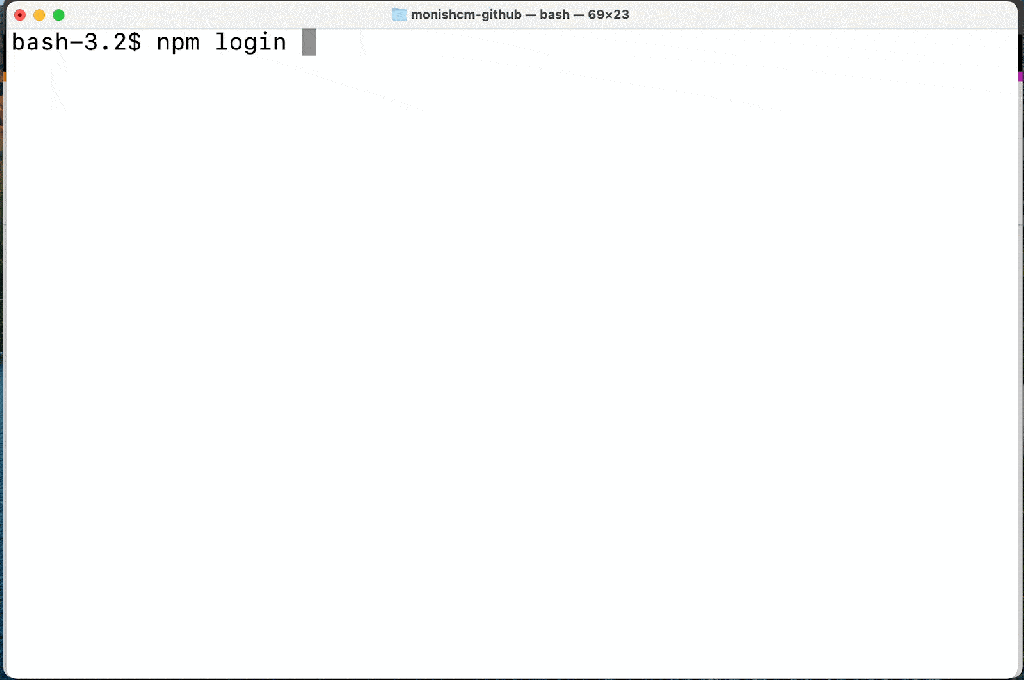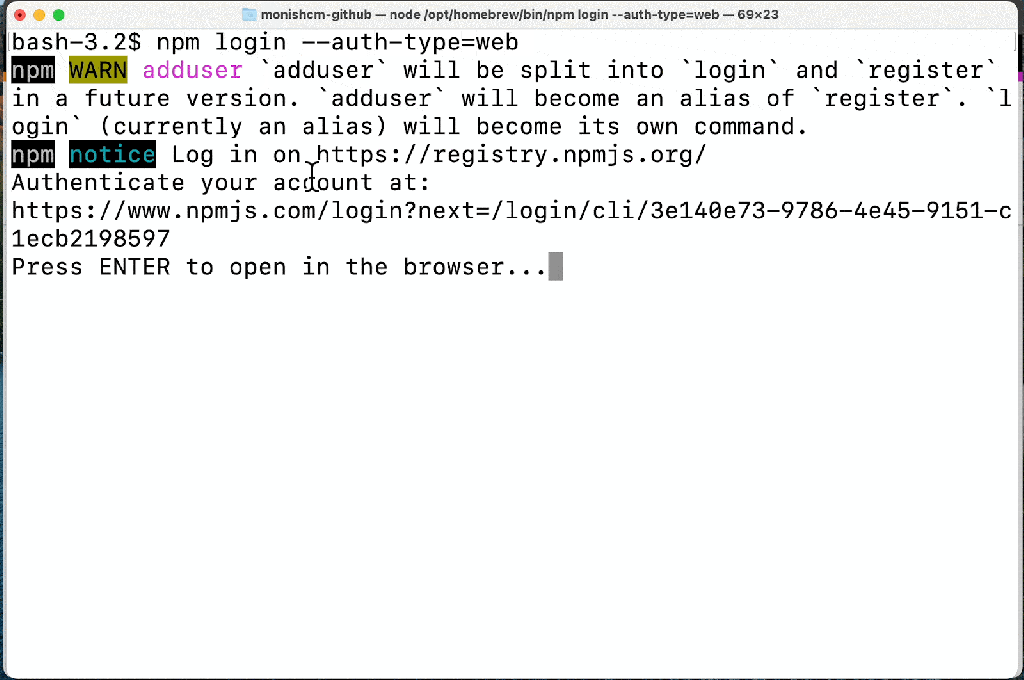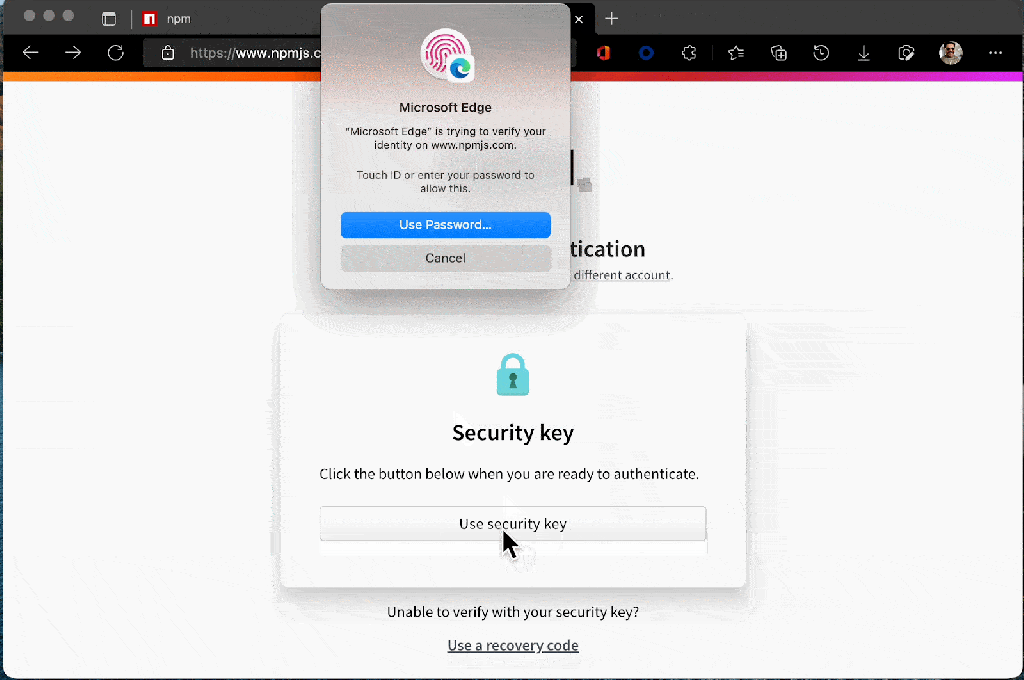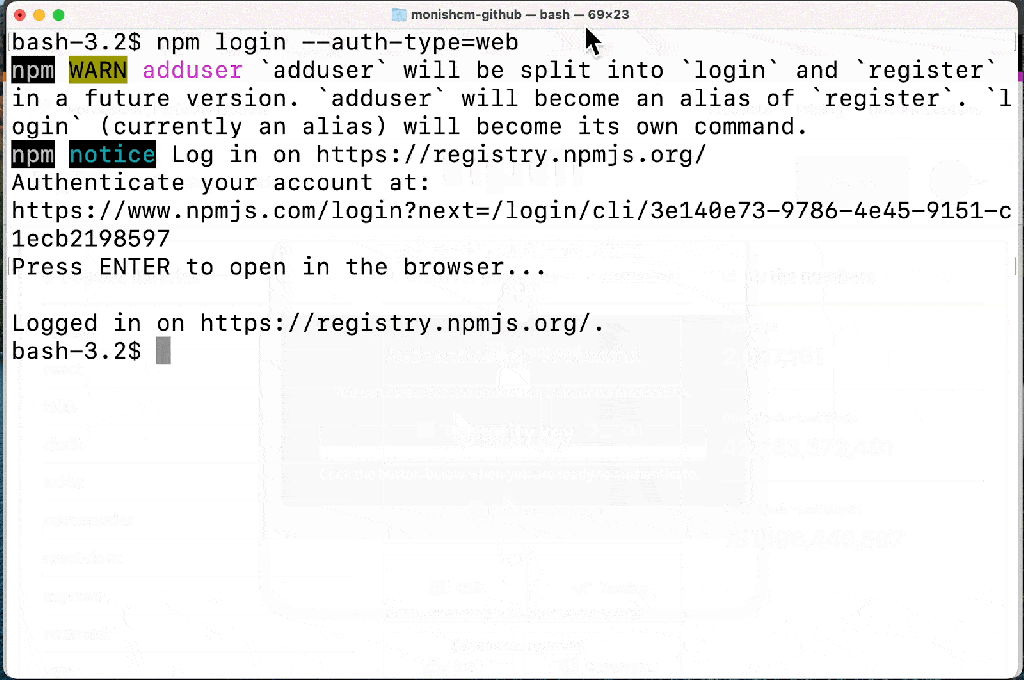
This change is to reduce friction created by the introduction of the 2FA system, which forced developers to enter new one-time passwords on every action.
The new option to connect GitHub and Twitter accounts to npm aims to help add credibility and serve as a form of identity verification so that npm accounts cannot impersonate creators of popular software.
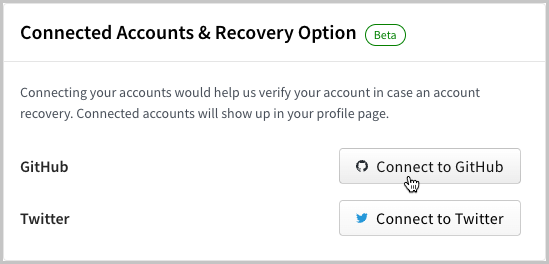
Moreover, this new system should help with account recovery when needed, making the process more reliable and less cumbersome and laying the ground for more automation in the future.
Trending: OSINT Tool: SARENKA
Finally, there’s a new signature auditing system that replaces the previous multi-step, complex PGP process, allowing developers a much easier method to verify the signature of npm packages.
Users will now be able to validate the source of the packages locally using the new “npm audit signatures” command in the npm CLI.
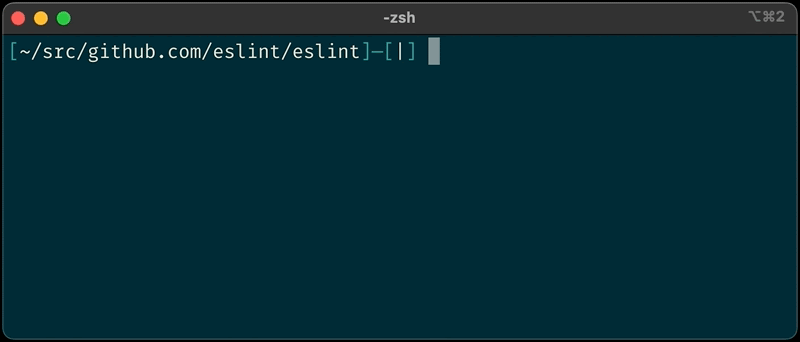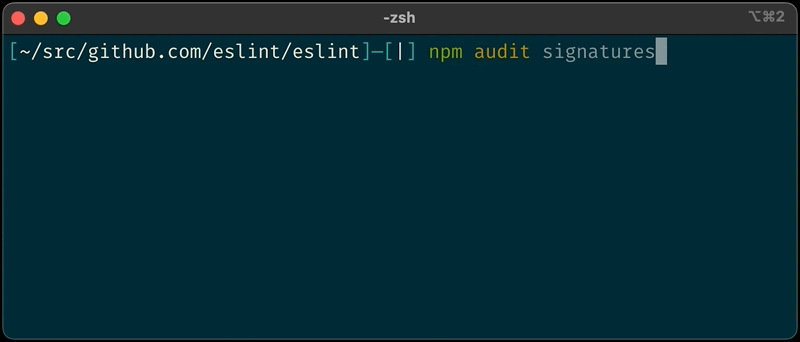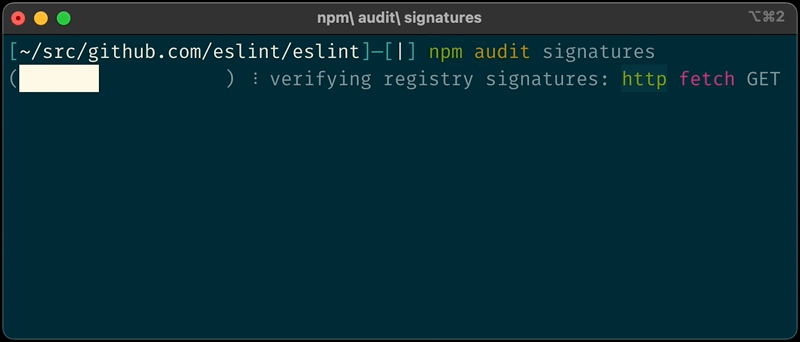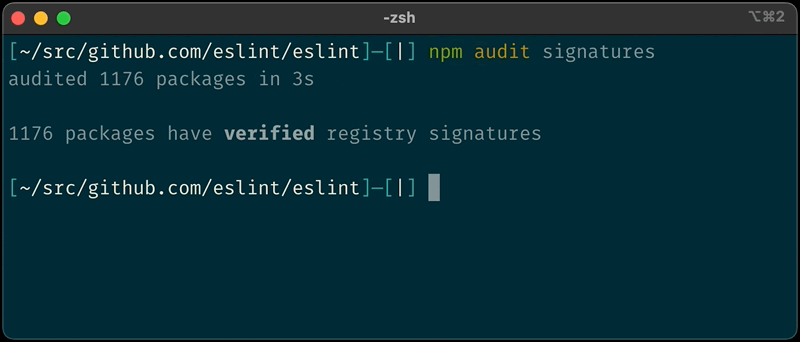
Simultaneously, the platform re-signs all packages with the ECDSA (elliptic curve cryptography) algorithm and uses HSM for key management, further bolstering security.
2FA on important accounts
The next step in securing the npm registry is to enforce two-factor authentication on all accounts that manage packages with more than a million weekly downloads or 500 dependents.
GitHub says this will be enforced only after the account recovery process is further improved with additional identity verification forms, so no strict timelines were provided besides that it’s coming next.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com












