GoAnywhere MFT by Fortra: Exploit Released for Authentication Bypass, Admin User Creation

Exploit code has surfaced for a critical authentication bypass vulnerability present in Fortra’s GoAnywhere MFT (Managed File Transfer) software. This vulnerability allows attackers to generate new admin users on instances lacking the latest patches, exploiting the administration portal as the point of entry.
While Fortra silently patched the bug (CVE-2024-0204) on December 7 with the release of GoAnywhere MFT 7.4.1, the company only publicly disclosed it yesterday in an advisory offering limited information. However, Fortra also issued private advisories to customers on December 4 before fixing the flaw, urging them to secure their MFT services to keep their data safe.
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
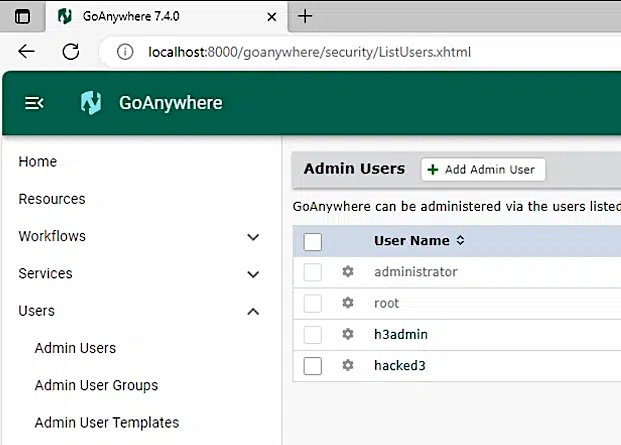 Exploit used to create new GoAnywhere MFT admin users (Horizon3)
Exploit used to create new GoAnywhere MFT admin users (Horizon3)Trending: Jeff Foley – OWASP Amass Founder
Trending: OSINT Tool: apk2url
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













